Which two secure communication protocols should you use?
You create an application by using Microsoft Visual Studio .NET 2008 and the .NET Framework 3.5.
The application consists of the following components:
– An ASP.NET Web application that is deployed on a Web server named WEB1
– An ASMX Web service that is deployed on an application server named APP1
– A Microsoft SQL Server database that is deployed on a database server named SQL1
The ASP.NET application connects to an ASMX Web service. The APP1 server hosts several ASMX Web service applications.
The ASMX Web service stores and retrieves data from SQL1.
You need to ensure that the secure communication strategy meets the following requirements:
– The communication configuration between WEB1 and APP1 must be secured without other applications being affected.
– Server authentication and data encryption must be performed between APP1 and SQL1.
Which two secure communication protocols should you use? (Each correct answer presents part of the solution. Choose two.)
What should you do?
You create an application by using Microsoft Visual Studio .NET 2008 and the .NET Framework 3.5.
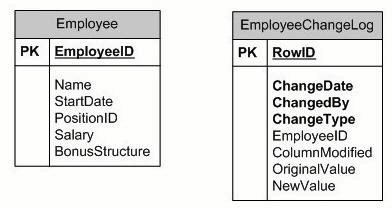
The application stores human resources data in a Microsoft SQL Server 2008 database. A partial database schema is as shown in the exhibit.
(Click the Exhibit button.) Each time a row is added, modified, or deleted from the Employee table, a corresponding entry must be recorded
in the EmployeeChangeLog table. You need to implement the data change logging.
What should you do?
Which strategy should you recommend?
You create an application by using Microsoft Visual Studio .NET 2008 and the .NET Framework 3.5.
The ASP.NET application connects to a shared Microsoft SQL Server 2008 database instance.
The application requires certain changes in the relationships represented in the data. However, any changes to the database schema can break
existing applications that share the database instance. You need to recommend a strategy that allows the application to make the required relationship
changes without affecting the underlying database schema. You also need to ensure that the strategy uses the minimum amount of development effort.
Which strategy should you recommend?
What should you do?
You create an application by using Microsoft Visual Studio .NET 2008 and the .NET Framework 3.5.
The application processes sales order documents. The application contains a component that retrieves the sales order documents from a FTP server
and stores the data in a Microsoft SQL Server database. You need to ensure that the component meets the following requirements:
– Periodically polls the FTP server to check for new order documents
– Executes without dependencies on other software components
– Executes without user interaction
– Executes by using a specific security context
– Allows system administrators to change the security context by retaining the same component code What should you do?
What should you do?
You create an application by using Microsoft Visual Studio .NET 2008 and the .NET Framework 3.5.
Users access the application by using Windows-based client applications or Web-based client applications.
All client applications share common business logic to handle transaction processing requests.
You need to ensure that the application is easy to maintain. What should you do?
What should you do?
You create an application by using Microsoft Visual Studio .NET 2008 and the .NET Framework 3.5.
You plan to implement a data access component to retrieve product data from a corporate database.
The component will return data for the products that meet the defined criteria.
You need to ensure that the component conforms to the following requirements:
– Access to the database is provided only when necessary.
– The database schema is hidden from the application that calls the component.
– Calls are returned by the component as quickly as possible.
What should you do?
What should you do?
You create a solution by using Microsoft Visual Studio .NET 2008 and the .NET Framework 3.5.
The solution contains a Microsoft Windows Forms application and a Windows Communication Foundation (WCF) service.
You discover that when the application is run, certain tasks take a very long time to execute. You verify that all CPUs are idle while these tasks are being executed.
You need to design a strategy to identify the methods that cause the tasks to be delayed in the application. What should you do?
Which storage mechanism should you use?
You create an ASP.NET application by using Microsoft Visual Studio .NET 2008 and the .NET Framework 3.5.
The application retrieves a large amount of application-wide data from a database. The data retrieval is very slow. The data gets refreshed every 30 minutes.
You need to ensure that the data is available for frequent access. You also need to make the most efficient use of resources.
Which storage mechanism should you use?
What should you do?
You create an application by using Microsoft Visual Studio 2008 and the .NET Framework 3.5.
The application is hosted on a Web server that runs Microsoft Windows Server 2003. It connects to a third-party system by using Web service calls.
The third-party system experiences occasional unplanned outages. When a system outage occurs, the application must perform the following tasks:
– Log error details.
– Notify an on-call technician.
You need to develop a strategy to perform the required tasks.
What should you do?
What should you do?
You create an application by using Microsoft Visual Studio .NET 2008 and the .NET Framework 3.5.
The application exposes a Windows Communication Foundation (WCF) Web service. The Web service is consumed by third-party applications.
You need to ensure that the WCF service provides interoperable and secure end-to-end communications.
What should you do?