Which behavior should you configure and apply to the service?
A Windows Communication Foundation (WCF) service interacts with the database of a
workflow engine. Data access authorization is managed by the database, which raises
security exceptions if a user is unauthorized to access it. You need to ensure that the
application transmits the exceptions raised by the database to the client that is calling the
service. Which behavior should you configure and apply to the service?
Which configuration segment should you use?
You are developing a Windows Communication Foundation (WCF) service. You must
record all available information for the first 1,000 messages processed, even if they are
malformed. You need to configure the message logging section of the configuration file.
Which configuration segment should you use?
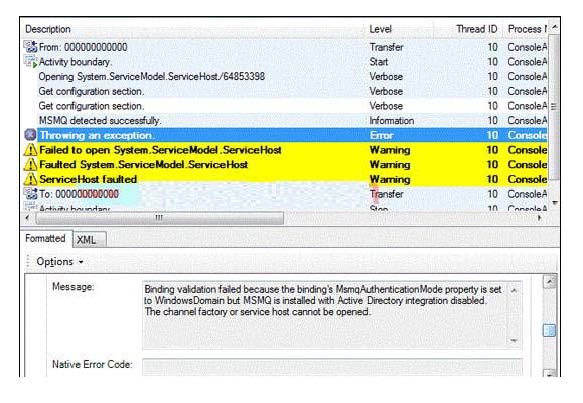
You need to interpret the trace results to determine where the error occurred and what to do next
You are using tracing to diagnose run-time issues when you look at the traces for the
service in Svc Trace viewer exe, you see what is shown in the exhibit (Click the Exhibit
button) The exception trace is selected in Svc Trace reviewer exe. You need to interpret the
trace results to determine where the error occurred and what to do next. What should you
do?
You need to configure the WCF service to execute under the Windows logged-on identity of the calling applicati
A Windows Communication Foundation (WCF) service that handles corporate accounting
must be changed to comply with government regulations of auditing and accountability You
need to configure the WCF service to execute under the Windows logged-on identity of the
calling application. What should you do?
What should you do?
The endpoint of a Windows Communication Foundation (WCF) service uses
basicHttpBinding for its binding Your Company’s policies have changed to require that
messages not be sent in clear text. You must ensure that all messages are encrypted when
traveling across the network What should you do?
What are two possible properties you can use to achieve this goal?
Self-hosted Windows Communication Foundation (WCF) service uses a secure HTTP
binding with a custom principal permission mode. The binding requires users to provide
their Windows logon credentials. You need to retrieve the identity of the caller. What are two
possible properties you can use to achieve this goal? (Each correct answer presents a
complete solution Choose two)
You need to ensure that users can access the WCF services without having to re-authenticate
You are creating an ASP.NET Web application that hosts several Windows Communication
Foundation (WCF) services. The services have ASP.NET Compatibility Mode enabled.
Users authenticate with the Web application by using a cookie-based ASP.NET Forms
Authentication model. You add a service file named Authentication.svc that contains the
following code segment. <%@ ServiceHost
Service=”System.Web.ApplicationServices.AuthenticationService”
Factory=”System.Web.ApplicationServices.ApplicationServicesHostFactory” %> You need
to ensure that users can access the WCF services without having to re-authenticate. Which
two configuration settings should you add (Each is part of a complete solution. Choose two.)
You need to implement the service to meet these requirements
You are creating a windows Communication Foundation (WCF) service to process orders.
The data contract for the order is defined as follows: [DataContract] public class Order { …
[DataMemberl public string CardHolderName { get; set; [DataMember] public string
CreditCardNumber { get; set; } } You have the following requirements – – – Enable the
transmission of the contents of Order from the clients to the service. Ensure that the
contents of CreditCardNumber are not sent across the network in clear text. Ensure that the
contents of CreditCardNumber are accessible by the service to process the order. You need
to implement the service to meet these requirements. What should you do?
What are two possible ways to achieve this goal?
You are developing a Windows Communication Foundation (WCF) service that returns
location information for authorized law enforcement agencies. The service contract is as
follows. [ServiceContract] public interface IMappingService { [OperationContract] long[]
GetLocationCoordinates(String cityNaroe); [OperationContract] long[]
GetLocationOfCitizen(String ssn) ; } Users are authenticated and impersonated. The system
uses ASP.NET roles. The members of law enforcement are members of the
LawEnforcement role. You need to ensure that only members of the LawEnforcement role
can call these methods. What are two possible ways to achieve this goal? (Each correct
answer presents a complete solution. Choose two.)
You need to track unsuccessful attempts to access the service
You have a secured Windows Communication Foundation (WCF) service. You need to
track unsuccessful attempts to access the service. What should you do?