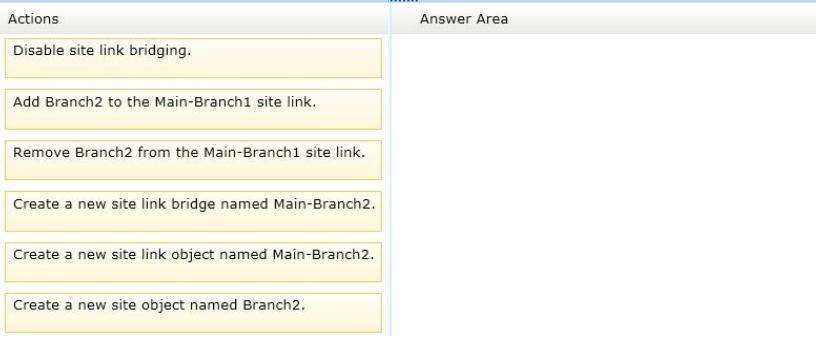
Which three actions should you perform?
Your network contains an Active Directory forest. The forest contains a single domain named contoso.com. The
forest contains two Active Directory sites named Main and Branch1. The sites connect to each other by using a
site link named Main-Branch1. There are no other site links.
Each site contains several domain controllers. All domain controllers run Windows Server 2012 R2. Your
company plans to open a new branch site named Branch2. The new site will have a WAN link that connects to
the Main site only. The site will contain two domain controllers that run Windows Server 2012 R2.
You need to create a new site and a new site link for Branch2. The solution must ensure that the domain
controllers in Branch2 only replicate to the domain controllers in Branch1 if all of the domain controllers in Main
are unavailable.
Which three actions should you perform?
To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in
the correct order.
Select and Place:
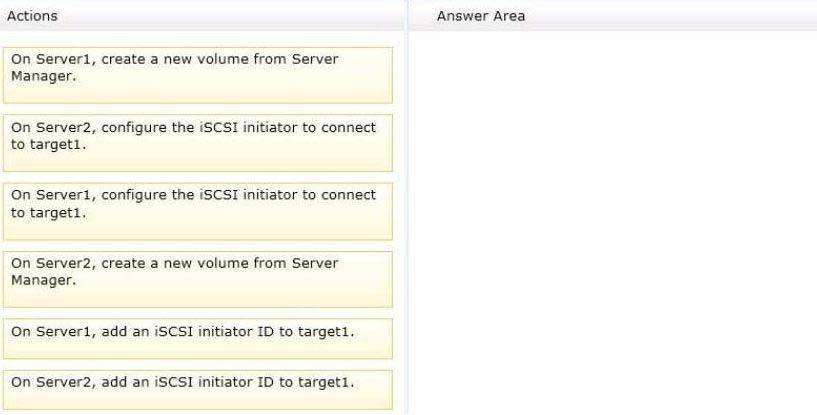
Which three actions should you perform in sequence?
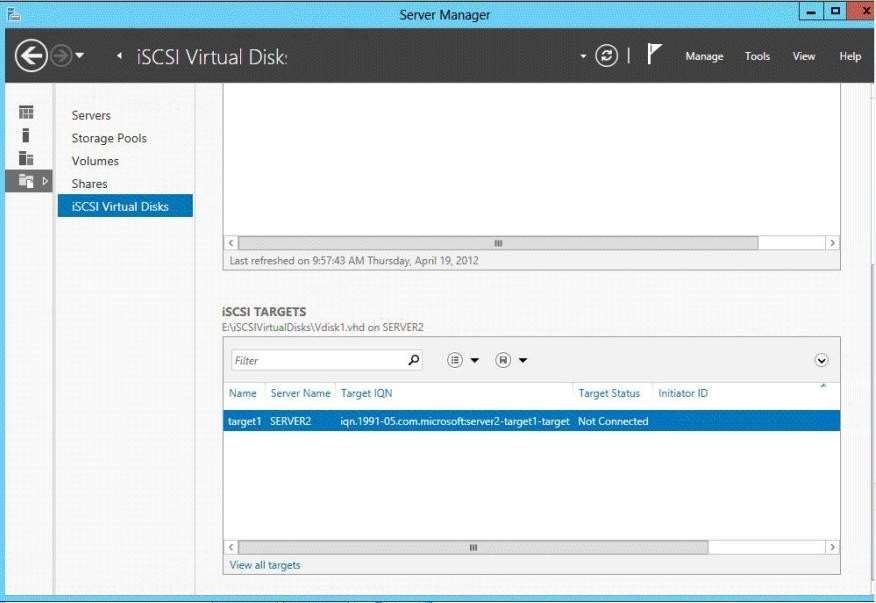
You have a server named Server2 that runs Windows Server 2012 R2. You have storage provisioned on
Server2 as shown in the exhibit. (Click the Exhibit button.)
You need to configure the storage so that it appears in Windows Explorer as a drive letter on Server1.
Which three actions should you perform in sequence?
the three appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Select and Place:
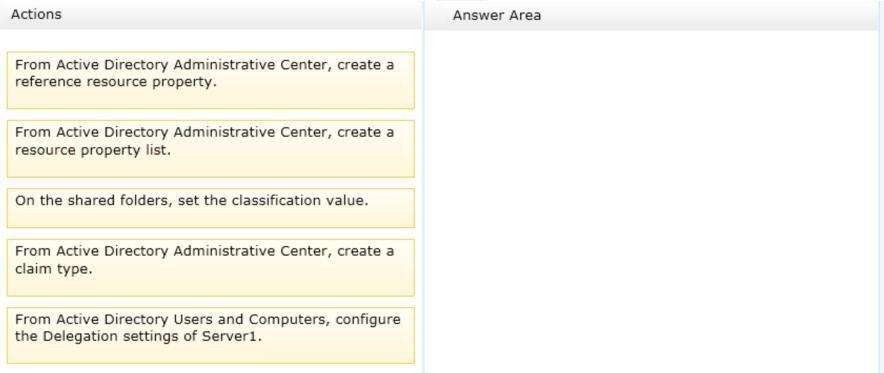
Which three actions should you perform in sequence?
Your network contains an Active Directory domain named contoso.com. The domain contains a file server
named Server1. All servers run Windows Server 2012 R2.
All domain user accounts have the Division attribute automatically populated as part of the user provisioning
process. The Support for Dynamic Access Control and Kerberos armoring policy is enabled for the domain.
You need to control access to the file shares on Server1 based on the values in the Division attribute and the
Division resource property.
Which three actions should you perform in sequence?
Select and Place:
What should you identify?
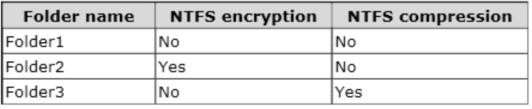
You have a file server named Server1 that runs Windows Server 2012 R2. The folders on Server1 are
configured as shown in the following table.
A new corporate policy states that backups must use Microsoft Online Backup whenever possible.
You need to identify which technology you must use to back up Server1. The solution must use Microsoft
Online Backup whenever
What should you identify?
To answer, drag the appropriate backup type to the correct location or locations. Each backup type may be
used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view
content.Select and Place:
which order should you Perform the five actions?
Your network contains an Active Directory domain named contoso.com. All file servers in the domain run
Windows Server 2012.
The computer accounts of the file servers are in an organizational unit (OU) named OU1. A Group Policy object
(GPO) named GPO1 is linked to OU1.
You plan to modify the NTFS permissions for many folders on the file servers by using central access policies.
You need to identify any users who will be denied access to resources that they can currently access once the
new permissions are implemented.
In which order should you Perform the five actions?
Select and Place:
Which two actions should you perform?
Your network contains an Active Directory domain named contoso.com. The domain contains a server named
Server1 that runs Windows Server 2012 R2.
Server1 is an enterprise root certification authority (CA) for contoso.com.
You need to ensure that the members of a group named Group1 can request code signing certificates. The
certificates must be issued automatically to the members.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
You need to ensure that a user named User1 can decrypt …
Your network contains an Active Directory domain named adatum.com. The domain contains a server named
CA1 that runs Windows Server 2012 R2. CA1 has the Active Directory Certificate Services server role installed
and is configured to support key archival and recovery.
You need to ensure that a user named User1 can decrypt private keys archived in the Active Directory
Certificate Services (AD CS) database. The solution must prevent User1 from retrieving the private keys from
the AD CS database.
What should you do?
Which two actions should you perform?
Your network contains an Active Directory domain named contoso.com. The domain contains a certification
authority (CA).
You suspect that a certificate issued to a Web server is compromised.
You need to minimize the likelihood that users will trust the compromised certificate.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
Which type of trust policy should you create?
Your network contains an Active Directory domain named contoso.com. The domain contains a server named
Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Rights Management Services
server role installed.
Your company works with a partner organization that does not have its own Active Directory Rights
Management Services (AD RMS) implementation.
You need to create a trust policy for the partner organization.
The solution must meet the following requirements:
Grant users in the partner organization access to protected content.
Provide users in the partner organization with the ability to create protected content.Which type of trust policy should you create?
Which two permissions should you assign to Group1?
Your network contains an Active Directory domain named contoso.com. The domain contains a server named
Server1 that runs Windows Server 2012 R2. Server1 has the Active Directory Certificate Services server role
installed and is configured to support key archival and recovery.
You create a new Active Directory group named Group1.
You need to ensure that the members of Group1 can request a Key Recovery Agent certificate. The solution
must minimize the permissions assigned to Group1.
Which two permissions should you assign to Group1? (Each correct answer presents part of the solution.
Choose two.)