You need to configure the storage for the Hyper-V hosts
Your network contains 20 iSCSI storage appliances that will provide storage for 50 Hyper-V hosts
running Windows Server 2012 R2.
You need to configure the storage for the Hyper-V hosts. The solution must minimize administrative
effort.
What should you do first?
which order should you Perform the five actions?
DRAG DROP
Your network contains an Active Directory domain named contoso.com. All file servers in the
domain run Windows Server 2012 R2.
The computer accounts of the file servers are in an organizational unit (OU) named OU1. A Group
Policy object (GPO) named GPO1 is linked to OU1.
You plan to modify the NTFS permissions for many folders on the file servers by using central access
policies.
You need to identify any users who will be denied access to resources that they can currently access
once the new permissions are implemented.
In which order should you Perform the five actions?
You need to configure the storage for the Hyper-V hosts
Your network contains 20 iSCSI storage appliances that will provide storage for 50 Hyper-V hosts
running Windows Server 2012 R2.
You need to configure the storage for the Hyper-V hosts. The solution must minimize administrative
effort.
What should you do first?
What should you configure?
Your network contains an Active Directory domain named contoso.com. The domain contains a file
server named Server1 that runs Windows Server 2012 R2. All client computers run Windows 8.
You need to configure a custom Access Denied message that will be displayed to users when they
are denied access to folders or files on Server1.
What should you configure?
What should you configure?
Your network contains an Active Directory domain named contoso.com. The domain contains a file
server named Server1 that runs Windows Server 2012 R2. All client computers run Windows 8.
You need to configure a custom Access Denied message that will be displayed to users when they
are denied access to folders or files on Server1.
What should you configure?
Which cmdlet should you use to achieve each requirement?
DRAG DROP
Youhave a server that runs Windows Server 2012 R2.
Youcreate a new work folder named Share1.
Youneed to configure Share1 to meet the following requirements:
Ensure that all synchronized copies of Share1 are encrypted.
Ensure that clients synchronize to Share1 every 30 minutes.
Ensure that Share1 inherits the NTFS permissions of the parent folder.
Which cmdlet should you use to achieve each requirement?
To answer, drag the appropriate cmdlets to the correct requirements. Each cmdlet may be used
once, more than once, or not at all. Youmay need to drag the split bar between panes or scroll to
view content.
Which two settings should you configure in GPO1?
HOTSPOT
Your network contains an Active Directory domain named contoso.com. All client computers run
Windows 8 Enterprise.
You have a remote site that only contains client computers. All of the client computer accounts are
located in an organizational unit (OU) named Remote1. A Group Policy object (GPO) named GPO1 is
linked to the Remote1 OU.
You need to configure BranchCache for the remote site.
Which two settings should you configure in GPO1?
To answer, select the two appropriate settings in the answer area.
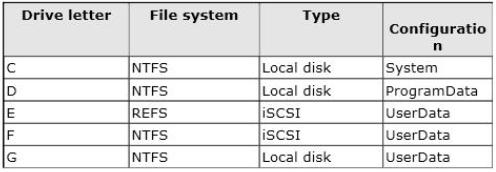
Which three drives should you identify?
You have a server named Server1 that runs Windows Server 2012 R2. The storage on Server1 is
configured as shown in the following table.
You plan to implement Data Deduplication on Server1.
You need to identify on which drives you can enable Data Deduplication.
Which three drives should you identify? (Each correct answer presents part of the solution. Choose
three.)
You need to ensure that access requests are unaffected when the rule is published
Your network contains an Active Directory domain named contoso.com. All servers run Windows
Server 2012 R2.
You are creating a central access rule named TestFinance that will be used to audit members of the
Authenticated Users group for access failure to shared folders in the finance department.
You need to ensure that access requests are unaffected when the rule is published.
What should you do?
You need to ensure that access requests are unaffected when the rule is published
Your network contains an Active Directory domain named contoso.com. All servers run Windows
Server 2012 R2.
You are creating a central access rule named TestFinance that will be used to audit members of the
Authenticated Users group for access failure to shared folders in the finance department.
You need to ensure that access requests are unaffected when the rule is published.
What should you do?