You need to uninstall the graphical user interface (GUI) on Server1
You have a server named Server1 that runs a full installation of Windows Server 2012.
You need to uninstall the graphical user interface (GUI) on Server1. You must achieve this goal by using the
minimum amount of Administrative effort.
What should you do?
Which command should you run first?
Your network contains a Windows Server 2012 image named Server12.wim. Server12.wim contains the
images shown in the following table.
Server12.wim is located in C:\.
You need to enable the Windows Server Migration Tools feature in the Windows Server 2012 Server
Datacenter image.
You want to achieve this goal by using the minimum amount of Administrative effort.
Which command should you run first?
You need to prevent Server1 from attempting to resolve Internet host names for the client computers
Your network contains an Active Directory domain named contoso.com. The network contains 500 client
computers that run Windows 2012. All of the client computers connect to the Internet by using a web proxy.
You deploy a server named Server1 that runs WindowsServer 2012.
Server1 has the DNS Server server role installed. You configure all of the client computers to use Server1 as
their primary DNS server. You need to prevent Server1 from attempting to resolve Internet host names for the
client computers.
What should you do on Server1?
Which tool should you use?
You perform a Server Core Installation of Windows Server 2012 on a server named Server1.
You need to add a graphical user interface (GUI) toServer1.
Which tool should you use?
You need to create aGPO in contoso.com based on the settings of GPO1
Your network contains a production Active Directoryforest named contoso.com and a test Active Directory
forest named contoso.test. A trust relationship does not exist between the forests.
In the contoso.test domain, you create a backup of a Group Policy object (GPO) named GPO1.
You transfer the backup of GPO1 to a domain controller in the contoso.com domain. You need to create aGPO
in contoso.com based on the settings of GPO1.
You must achieve this goal by using the minimum amount of administrative effort.
What should you do?
What should you create?
You have a server that runs Windows Server 2012. The server contains the disks configured as shown in the
following table.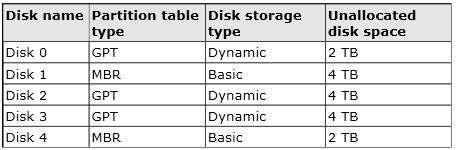
You need to create a volume that can store up to 3 TB of user files. The solution must ensure that theuser files
are available if one of the disks in the volume fails.
What should you create?
What should you configure?
HOTSPOT
Your network contains a server named Server1 that runs Windows Server 2012. App1 has the Print and
Document Services server role installed.
All client computers run Windows 8.
The network contains a network-attached print device named Printer1.
From App1, you share Printer1.
You need to ensure that users who have connected toPrinter1 previously can print to Printer1 if App1 fails.
What should you configure?
To answer, select the appropriate option in the answer area.
Which node should you use to add the DHCP Relay Agent?
HOTSPOT
You have a server named Server1. Server1 runs Windows Server 2012.
Server1 has two network adapters and is located in a perimeter network.
You need to install a DHCP Relay Agent on Server1.
Which node should you use to add the DHCP Relay Agent? To answer, select the appropriate node in the
answer area.
Which rule should you modify?
HOTSPOT
Your network contains an Active Directory domain named corp.contoso.com. The domain contains a domain
controller named DC1.
When you run ping dc1.corp.contoso.com, you receivethe result as shown in the exhibit.
(Refer to the Exhibit.)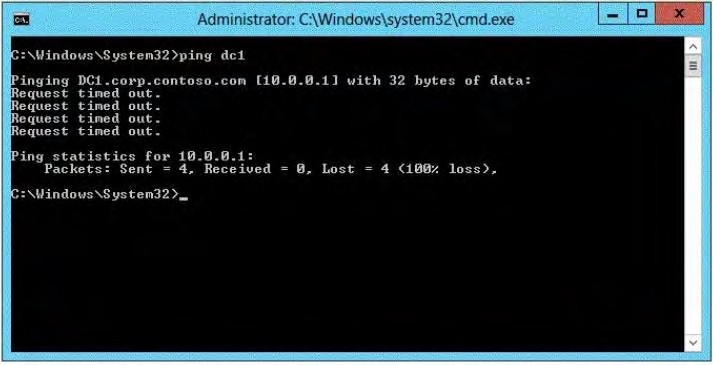
You need to ensure that DC1 can respond to the Pingcommand.
Which rule should you modify?
To answer, select the appropriate rule in the answer area.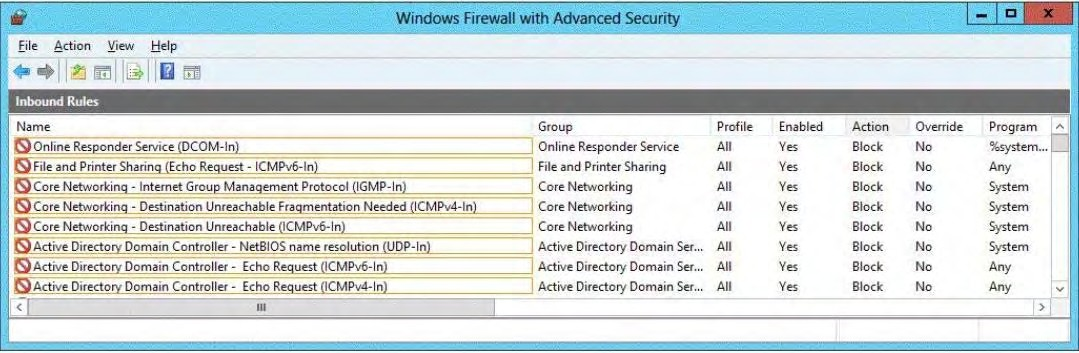
Which three actions should you perform?
DRAG DROP
Your network contains two Active Directory forests named contoso.com and adatum.com. Both forests contain
multiple domains. A two-way trust exists between the forests.
The adatum.com domain contains a domain local security group named Group1. Group1 contains adatum
\user1 and contoso\user1.
You need to ensure that Group1 can only contain users from the adatum.com domain.
Which three actions should you perform?
To answer, move three actions from the list of actions to the answer area and arrange them in the correct
order.

