Which tool should you use?
Your network contains an Active Directory domain named contoso.com. The domain
contains a domain controller named DC5. DC5 has a Server Core Installation of Windows
Server 2012 R2.
You need to uninstall Active Directory from DC5 manually.
Which tool should you use?
Which virtual machine settings should you configure on VM1 and VM2?
Your network contains two Hyper-V hosts named Host1 and Host2. Host1 contains a virtual
machine named VM1. Host2 contains a virtual machine named VM2. VM1 and VM2 run
Windows Server 2012 R2.
You install the Network Load Balancing feature on VM1 and VM2.
You need to ensure that the virtual machines are configured to support Network Load
Balancing (NLB).
Which virtual machine settings should you configure on VM1 and VM2?
Which settings should you configure?
HOTSPOT
Your network contains an Active Directory domain named contoso.com.
Technicians use Windows Deployment Services {WDS) to deploy Windows Server 2012 R2.
The network contains a server named Server1 that runs Windows Server 2012 R2. Server1
has the Hyper-V server role installed.
You need to ensure that you can use WDS to deploy Windows Server 2012 R2 to a virtual
machine named VM1.
Which settings should you configure?
To answer, select the appropriate settings in the answer area.
which node should you configure the exclusion range?
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The network
contains two subnets. The subnets are configured as shown in the following table.
The network contains a member server named Server1 that runs Windows Server 2012 R2.
Server1 has the DHCP Server server role installed. Server1 is configured to lease IP
addresses to the two subnets.
You add three new printers to the MainOffice subnet. The printers have static IP addresses.
The IP addresses are consecutive.
You need to create an exclusion range that contains the IP addresses of the printers.
From which node should you configure the exclusion range?To answer, select the
appropriate node in the answer area.
Which snap-in should you use?
Your network contains an Active Directory domain named contoso.com. The domain
contains a server named Server1. Server1 runs Windows Server 2012 R2.
An administrator creates a security template named Template1.
You need to apply Template1 to Server1.
Which snap-in should you use?
You need to configure GPO1 to apply to all of the users in OU1
Your network contains an Active Directory domain named contoso.com.
You have a Group Policy object (GPO) named GPO1 that contains several user settings.
GPO1 is linked to an organizational unit (OU) named OU1.
The help desk reports that GPO1 applies to only some of the users in OU1.
You open Group Policy Management as shown in the exhibit. (Click the Exhibit button.)
You need to configure GPO1 to apply to all of the users in OU1.
What should you do?
You need to ensure that all users see only their own home folder when they access Home
Your network contains an Active Directory domain named adatum.com. The domain
contains a file server named Server2 that runs Windows Server 2012 R2. Server2 contains a
shared folder named Home. Home contains the home folder of each user.
All users have the necessary permissions to access only their home folder.
A user named User1 opens the Home share as shown in the exhibit. (Click the Exhibit
button.)
You need to ensure that all users see only their own home folder when they access Home.
What should you do from Server2?
You need to ensure that users can recover files that they accidently delete from Documents
Your network contains an Active Directory domain named contoso.com. The domain
contains a member server named Server1. Server1 runs Windows Server 2012 R2 and has
the File and Storage Services server role installed.
On Server1, you create a share named Documents.
You need to ensure that users can recover files that they accidently delete from Documents.
What should you do?
You need to ensure that you can connect to Network1 from Windows Server 2012 R2
You have a laptop named Computer1. Computer1 runs Windows 8 Enterprise.
Computer1 has a wired network adapter and a wireless network adapter. Computer1
connects to a wireless network named Network1.
For testing purposes, you install Windows Server 2012 R2 on Computer1 as a second
operating system. You install the drivers for the wireless network adapter.
You need to ensure that you can connect to Network1 from Windows Server 2012 R2.
What should you do?
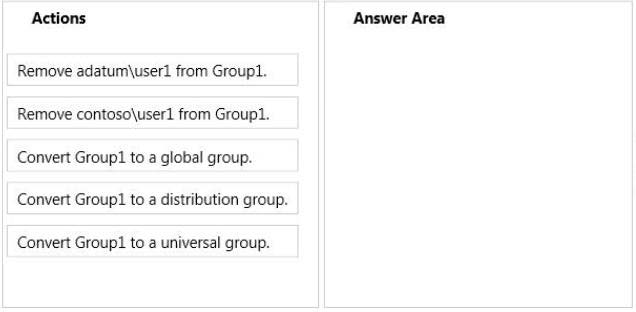
Which three actions should you perform?
DRAG DROP
Your network contains two Active Directory forests named adatum.com and contoso.com.
Both forests contain multiple domains. A two-way trust exists between the forests.
The contoso.com domain contains a domain local security group named Group1. Group1
contains Contoso\user1 and adatum\user1.
You need to ensure that Group1 can only contain users from the contoso.com domain.
Which three actions should you perform?
To answer, move three actions from the list of actions to the answer area and arrange them
in the correct order.