You need to ensure that traffic destined for only the cluster nodes is not sent to all ports of the switching
You are the network administrator for your company. The network consists of a single Active Directory domain. All computers on the network are members of the domain. You administer a four-node Network Load Balancing cluster. All nodes run Windows Server 2003. The cluster has converged successfully.
You use Network Load Balancing Manager on the default host to configure all nodes of the cluster. The nodes have a single network adapter and are connected to the same switching hub device. Administrators of non-cluster servers that are connected to the same switching hub device report that their servers receive traffic that is destined for the cluster nodes. Receiving this additional network traffic impairs the network performance of the non-cluster servers.
You need to ensure that traffic destined for only the cluster nodes is not sent to all ports of the switching hub device. You do not want to move the cluster to another switching hub device.
What should you do?
You need to plan how to monitor the application server and to have a message generated when broadcast traffic
You are the network administrator for your company. The network contains an application server running Windows Server 2003. Users report that the application server intermittently responds slowly. When the application server is responding slowly, requests that normally take 1 second to complete take more than 30 seconds to complete.
You suspect that the slow server response is because of high broadcast traffic on the network. You need to plan how to monitor the application server and to have a message generated when broadcast traffic is high. You also want to minimize the creation of false alarms when nonbroadcast traffic is high.
What should you do?
Which two actions should you take? (Each correct answer presents part of the solution
You are the network administrator for your company. The network consists of a single Active Directory domain. All servers run Windows Server 2003.
When the network was designed, the design team set design specifications. After the network was implemented, the deployment team set baseline specifications. The specifications for broadcast traffic are:
The design specification requires that broadcast traffic must be 5 percent or less of total network traffic.
The baseline specification showed that the broadcast traffic is always 1 percent or less of total network traffic during normal operation.
You need to monitor the network traffic and find out if the level of broadcast traffic is within design and baseline specifications. You decide to use Network Monitor. After monitoring for 1 hour, you observe the results shown in the exhibit.
You need to report the results of your observations to management.
Which two actions should you take? (Each correct answer presents part of the solution. Choose two.)
Exhibit:
You need to view all IPSec policies that are being applied to Server1
You are the network administrator for your company. The network consists of a single Active Directory domain. The domain contains a Windows Server 2003 computer named Server1 that is located in an organizational unit (OU) named Servers. Server1 contains confidential data, and all network communications with Server1 must be encrypted by using IPSec.
The default Client (Respond Only) IPSec policy is enabled in the Default Domain Policy Group Policy object (GPO). You create a new GPO and link it to the Servers OU. You configure the new GPO by creating and enabling a custom IPSec policy. You monitor and discover that network communications with Server1 are not being encrypted.
You need to view all IPSec policies that are being applied to Server1.
What should you do?
You need to provide Internet connectivity to users on Subnet2
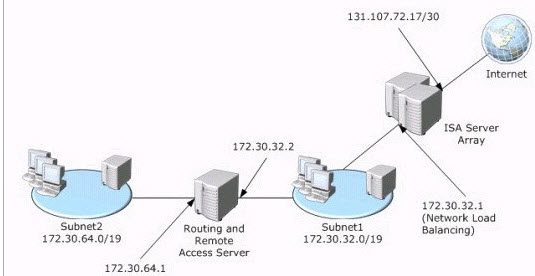
You are the network administrator for your company. The network consists of a single Active Directory domain. The network contains two IP subnets connected by a Windows Server 2003 computer running Routing and Remote Access. All servers run Windows Server 2003. All client computers run Windows XP Professional. Each subnet contains a domain controller. Each subnet contains a DHCP server, which provides TCP/IP configuration information to the computers on only its subnet. The relevant portion of the network is shown in the exhibit.
You recently implemented a Microsoft Internet Security and Acceleration (ISA) Server 2000 array on the network to provide Internet connectivity. The ISA Server array uses Network Load Balancing on the internal adapters. The array’s Network Load Balancing cluster address is 172.30.32.1.
You configure the DHCP server on Subnet1 to provide the array’s Network Load Balancing cluster address as the new default gateway. You configure the DHCP server on Subnet2 to provide the IP address 172.30.64.1 as the default gateway for Subnet2. Users on Subnet2 report that they cannot connect to Internet-based resources. They can successfully connect to resources located on Subnet1.
Users on Subnet1 can successfully connect to Internet- based resources. You investigate and discover that no Internet requests from computers on Subnet2 are being received by the ISA Server array. You need to provide Internet connectivity to users on Subnet2.
What should you do?
Exhibit:
You need to ensure that you can change the value of the validity period of the certificate that users request
You are the network administrator for your company. The network contains a single Active Directory domain. All computers on the network are members of the domain. All domain controllers run Windows Server 2003. You are planning a public key infrastructure (PKI). The PKI design documents for your company specify that certificates that users request to encrypt files must have a validity period of two years.
The validity period of a Basic EFS certificate is one year. In the Certificates Templates console, you attempt to change the validity period for the Basic EFS certificate template.
However, the console does not allow you to change the value. You need to ensure that you can change the value of the validity period of the certificate that users request to encrypt files.
What should you do?
You need to comply with the network design requirement
You are the network administrator for Tailspin Toys. The company has a main office and two branch offices. The network in the main office contains 10 servers and 100 client computers. Each branch office contains 5 servers and 50 client computers. Each branch office is connected to the main office by a direct T1 line. The network design requires that company IP addresses must be assigned from a single classful private IP address range. The network is assigned a class C private IP address range to allocate IP addresses for servers and client computers. Tailspin Toys acquires a company named Wingtip Toys.
The acquisition will increase the number of servers to 20 and the number of client computers to 200 in the main office. The acquisition is expected to increase the number of servers to 20 and the number of client computers to 200 in the branch offices. The acquisition will also add 10 more branch offices. After the acquisition, all branch offices will be the same size.
Each branch office will be connected to the main office by a direct T1 line. The new company will follow the Tailspin Toys network design requirements. You need to plan the IP addressing for the new company. You need to comply with the network design requirement.
What should you do?
You need to configure Server1 to log the details of access attempts by VPN users
You are the network administrator for your company. The network consists of a single Active Directory domain. The network contains Windows Server 2003 file servers. The network also contains a Windows Server 2003 computer named Server1 that runs Routing and Remote Access and Internet Authentication Service (IAS).
Server1 provides VPN access to the network for users’ home computers. You suspect that an external unauthorized user is attempting to access the network through Server1. You want to log the details of access attempts by VPN users when they attempt to access the network.
You want to compare the IP addresses of users’ home computers with the IP addresses used in the access attempts to verify that the users are authorized. You need to configure Server1 to log the details of access attempts by VPN users.
What should you do?
You need to minimize bandwidth utilization
You are a network administrator for your company. The company has a main office and two branch offices. The branch offices are connected to the main office by T1 lines. The network consists of three Active Directory sites, one for each office. All client computers run either Windows 2000 Professional or Windows XP Professional.
Each office has a small data center that contains domain controllers, WINS, DNS, and DHCP servers, all running Windows Server 2003. Users in all offices connect to a file server in the main office to retrieve critical files. The network team reports that the WAN connections are severely congested during peak business hours. Users report poor file server performance during peak business hours. The design team is concerned that the file server is a single point of failure.
The design team requests a plan to alleviate the WAN congestion during business hours and to provide high availability for the file server. You need to provide a solution that improves file server performance during peak hours and that provides high availability for file services. You need to minimize bandwidth utilization.
What should you do?
What should you do?
You are a network administrator for your company. The network consists of a single Active Directory domain. All domain controllers run Windows Server 2003. The domain contains 20 member servers that run Windows Server 2003. Client computers run either Windows 2000 Professional or Windows XP Professional. The network does not use IPSec policies.
You receive a report that a member server named Server1 cannot communicate with any domain controllers in the domain. The other member servers are operating properly. Client computers continue to connect to Server1 normally. You examine the security settings in the local computer policy of Server1. The relevant settings are shown in the exhibit.
You want Server1 to be able to connect to the domain controllers in the domain.
What should you do?
Exhibit: