Which two inbound TCP ports should you open on the firewall?
Your network contains an Active Directory forest named contoso.com. The forest contains a member server
named Server1 that runs Windows Server 2016. Server1 is located in the perimeter network.You install the Active Directory Federation Services server role on Server1. You create an Active Directory
Federation Services (AD FS) farm by using a certificate that has a subject name of sts.contoso.com.
You need to enable certificate authentication from the Internet on Server1.
Which two inbound TCP ports should you open on the firewall? Each correct answer presents part of the
solution.
Which cmdlet should you run?
Your network contains an Active Directory forest named contoso.com.
You have an Active Directory Federation Services (AD FS) farm. The farm contains a server named Server1
that runs Windows Server 2012 R2.
You add a server named Server2 to the farm. Server2 runs Windows Server 2016.
You remove Server1 from the farm.
You need to ensure that you can use role separation to manage the farm.
Which cmdlet should you run?
How should you configure Server1?
HOTSPOT
You have a server named Server1 that runs Windows Server 2016. Server1 has the Windows Application
Proxy role service installed.
You need to publish Microsoft Exchange ActiveSync services by using the Publish New Application Wizard. The
ActiveSync services must use preauthentication.
How should you configure Server1? To answer, select the appropriate options in the answer area.
Hot Area:
Which five GPOs will apply to User1 in sequence when th…
DRAG DROP
Note: This question is part of a series of questions that use the same scenario. For your convenience, the
scenario is repeated in each question. Each question presents a different goal and answer choices, but the text
of the scenario is exactly the same in each question in this series.
Start of repeated scenario.
Your network contains an Active Directory domain named contoso.com. The domain contains a single site
named Site1. All computers are in Site1.
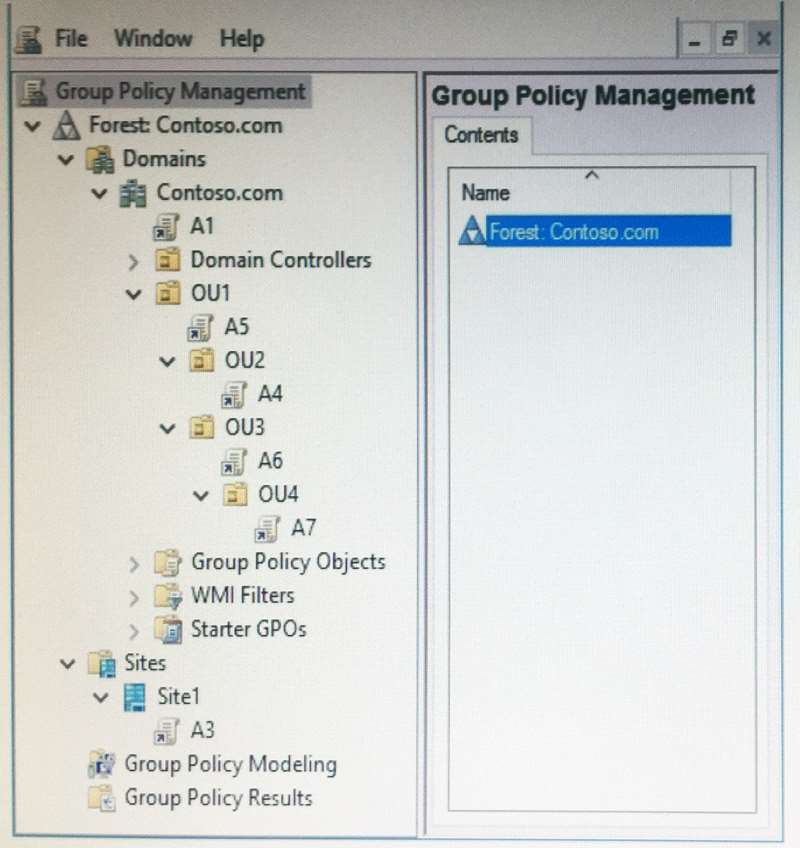
The Group Policy objects (GPOs) for the domain are configured as shown in the exhibit. (Click the Exhibit
button.)
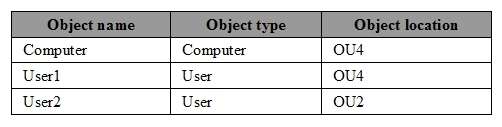
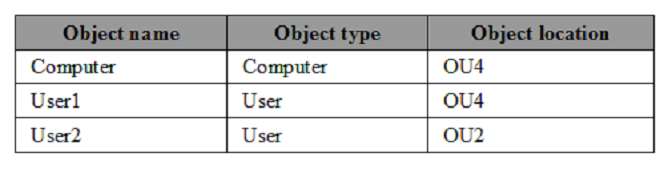
The relevant users and client computer in the domain are configured as shown in the following table.
End of repeated scenario.
Which five GPOs will apply to User1 in sequence when the user signs in to Computer1? To answer, move the
appropriate GPOs from the list to the answer area and arrange them in the correct order.
Select and Place:
Which GPOs will apply to User2 when the user signs in t…
Note: This question is part of a series of questions that use the same scenario. For your convenience, the
scenario is repeated in each question. Each question presents a different goal and answer choices, but the text
of the scenario is exactly the same in each question in this series.
Start of repeated scenario.
Your network contains an Active Directory domain named contoso.com. The domain contains a single site
named Site1. All computers are in Site1.
The Group Policy objects (GPOs) for the domain are configured as shown in the exhibit. (Click the Exhibit
button.)
The relevant users and client computer in the domain are configured as shown in the following table.
End of repeated scenario.
You are evaluating what will occur when you disable the Group Policy link for A6.
Which GPOs will apply to User2 when the user signs in to Computer1 after the link for A6 is disabled?
Which five GPOs will apply to User1 in sequence when th…
DRAG DROP
Note: This question is part of a series of questions that use the same scenario. For your convenience, the
scenario is repeated in each question. Each question presents a different goal and answer choices, but the text
of the scenario is exactly the same in each question in this series.
Start of repeated scenario.
Your network contains an Active Directory domain named contoso.com. The domain contains a single site
named Site1. All computers are in Site1.
The Group Policy objects (GPOs) for the domain are configured as shown in the exhibit. (Click the Exhibit
button.)
The relevant users and client computer in the domain are configured as shown in the following table.
End of repeated scenario.
You plan to enforce the GPO link for A6.
Which five GPOs will apply to User1 in sequence when the user signs in to Computer1 after the link is
enforced? To answer, move the appropriate GPOs from the list of GPOs to the answer area and arrange them
in the correct order.
Select and Place:
Which GPO or GPOs will apply to User1 when the user sig…
Note: This question is part of a series of questions that use the same scenario. For your convenience, the
scenario is repeated in each question. Each question presents a different goal and answer choices, but the text
of the scenario is exactly the same in each question in this series.
Start of repeated scenario.
Your network contains an Active Directory domain named contoso.com. The domain contains a single site
named Site1. All computers are in Site1.
The Group Policy objects (GPOs) for the domain are configured as shown in the exhibit. (Click the Exhibit
button.)
The relevant users and client computer in the domain are configured as shown in the following table.
End of repeated scenario.
You are evaluating what will occur when you block inheritance on OU4.
Which GPO or GPOs will apply to User1 when the user signs in to Computer1 after block inheritance is
configured?
Which command should you use in the contoso.com domain …
HOTSPOT
Note: This question is part of a series of questions that use the same scenario. For you convenience, the
scenario is repeated in each question. Each question presents a different goal and answer choices, but the text
of the scenario is exactly the same in each question in this series.
Start of repeated scenario.
You work for a company named Contoso, Ltd.
The network contains an Active Directory forest named contoso.com. A forest trust exists between
contoso.com and an Active Directory forest named adatum.com.
The contoso.com forest contains the objects configured as shown in the following table.
Group1 and Group2 contain only user accounts.
Contoso hires a new remote user named User3. User3 will work from home and will use a computer named
Computer3 that runs Windows 10. Computer3 is currently in a workgroup.
An administrator named Admin1 is a member of the Domain Admins group in the contoso.com domain.
From Active Directory Users and Computers, you create an organizational unit (OU) named OU1 in the
contoso.com domain, and then you create a contact named Contact1 in OU1.
An administrator of the adatum.com domain runs the Set-ADUser cmdlet to configure a user named User1 to
have a user logon name of User1@litwareinc.com.
End or repeated scenario.
You need to join Computer3 to the contoso.com domain by using offline domain join.
Which command should you use in the contoso.com domain and on Computer3? To answer, select the
appropriate options in the answer area.
Hot Area:
What should you modify?
Note: This question is part of a series of questions that use the same scenario. For your convenience, the
scenario is repeated in each question. Each question presents a different goal and answer choices, but the text
of the scenario is exactly the same in each question in this series.Start of repeated scenario.
You work for a company named Contoso, Ltd.
The network contains an Active Directory forest named contoso.com. A forest trust exists between
contoso.com and an Active Directory forest named adatum.com.
The contoso.com forest contains the objects configured as shown in the following table.
Group1 and Group2 contain only user accounts.
Contoso hires a new remote user named User3. User3 will work from home and will use a computer named
Computer3 that runs Windows 10. Computer3 is currently in a workgroup.
An administrator named Admin1 is a member of the Domain Admins group in the contoso.com domain.
From Active Directory Users and Computers, you create an organizational unit (OU) named OU1 in the
contoso.com domain, and then you create a contact named Contact1 in OU1.
An administrator of the adatum.com domain runs the Set-ADUser cmdlet to configure a user named User1 to
have a user logon name of User1@litwareinc.com.
End or repeated scenario.
You need to ensure that Admin1 can add Group2 as a member of Group3.
What should you modify?
What should you modify?
Note: This question is part of a series of questions that use the same scenario. For you convenience, the
scenario is repeated in each question. Each question presents a different goal and answer choices, but the text
of the scenario is exactly the same in each question in this series.
Start of repeated scenario.
You work for a company named Contoso, Ltd.
The network contains an Active Directory forest named contoso.com. A forest trust exists between
contoso.com and an Active Directory forest named adatum.com.
The contoso.com forest contains the objects configured as shown in the following table.
Group1 and Group2 contain only user accounts.
Contoso hires a new remote user named User3. User3 will work from home and will use a computer named
Computer3 that runs Windows 10. Computer3 is currently in a workgroup.
An administrator named Admin1 is a member of the Domain Admins group in the contoso.com domain.
From Active Directory Users and Computers, you create an organizational unit (OU) named OU1 in the
contoso.com domain, and then you create a contact named Contact1 in OU1.
An administrator of the adatum.com domain runs the Set-ADUser cmdlet to configure a user named User1 to
have a user logon name of User1@litwareinc.com.
End of repeated scenario.
You need to ensure that User2 can add Group4 as a member of Group5.
What should you modify?