Which two actions should you perform?
Your company plans to migrate from On-Premises Exchange to Exchange Online in Office 365.
You plan to integrate your existing Active Directory Domain Services (AD DS) infrastructure with Azure AD.
You need to ensure that users can log in by using their existing AD DS accounts and passwords. You need to
achieve this goal by using minimal additional systems.
Which two actions should you perform? Each answer presents part of the solution.
Which settings should you use?
DRAG DROP
Your company network includes a single forest with multiple domains. You plan to migrate from On-Premises
Exchange to Exchange Online.
You want to provision the On-Premises Windows Active Directory (AD) and Azure Active Directory (Azure AD)
service accounts.
You need to set the required permissions for the Azure AD service account.
Which settings should you use? To answer, drag the appropriate permission to the service account. Each
permission may be used once, more than once, or not at all. You may need to drag the split bar between panes
or scroll to view content.
Select and Place:
Hot Area:
HOTSPOT
You administer an Azure Active Directory (Azure AD) tenant.
You add a custom application to the tenant.
The application must be able to:
Read data from the tenant directly.
Write data to the tenant on behalf of a user.
In the table below, identify the permission that must be granted to the application. Make only one selection in
each column.
Hot Area:
You need to give anonymous users read access to all of …
Your company is launching a public website that allows users to stream videos.
You upload multiple video files to an Azure storage container.
You need to give anonymous users read access to all of the video files in the storage container.
What should you do?
Hot Area:
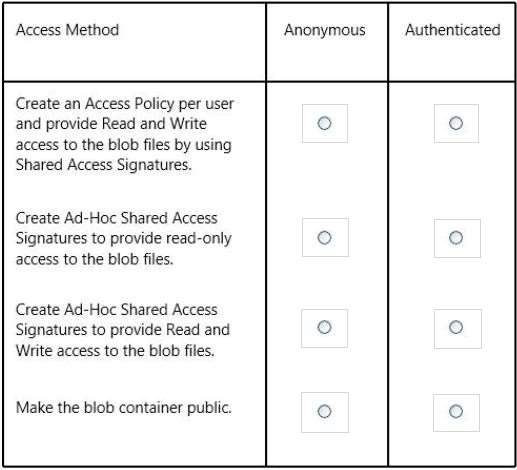
HOTSPOT
You manage a public-facing web application which allows authenticated users to upload and download large
files. On the initial public page there is a promotional video.
You plan to give users access to the site content and promotional video.
In the table below, identify the access method that should be used for the anonymous and authenticated parts
of the application. Make only one selection in each column.
Hot Area:
Hot Area:
HOTSPOT
You have an Azure SQL Database named Contosodb. Contosodb is running in the Standard/S2 tier and has a
service level objective of 99 percent.
You review the service tiers in Microsoft Azure SQL Database as well as the results of running performance
queries for the usage of the database for the past week as shown in the exhibits. (Click the Exhibits button.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Hot Area:
You need to reduce the costs associated with storing th…
You administer an Azure Storage account with a blob container. You enable Storage account logging for read,
write and delete requests.
You need to reduce the costs associated with storing the logs.
What should you do?
Which log entry should you use to verify access?
You administer an Azure Storage account named contosostorage. The account has a blob container to store
image files.
A user reports being unable to access an image file.
You need to ensure that anonymous users can successfully read image files from the container.
Which log entry should you use to verify access?
Hot Area:
HOTSPOT
You manage an Azure subscription.
You develop a storage plan with the following requirements:
Database backup files that are generated once per year are retained for ten years.
High performance system telemetry logs are created constantly and processed for analysis every month.
In the table below, identify the storage redundancy type that must be used. Make only one selection in each
column.
Hot Area:
What are two possible ways to achieve this goal?
Your company has recently signed up for Azure.
You plan to register a Data Protection Manager (DPM) server with the Azure Backup service.
You need to recommend a method for registering the DPM server with the Azure Backup vault.
What are two possible ways to achieve this goal? Each correct answer presents a complete solution.