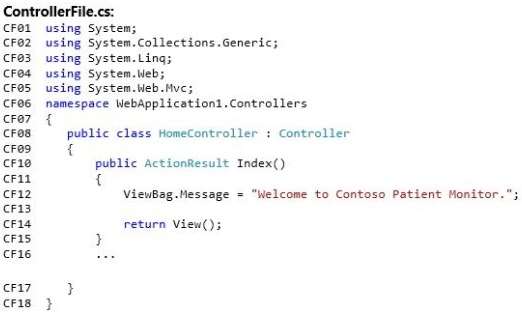
You need to ensure that the website is always responsive
###BeginCaseStudy###
Testlet 1
Background
Contoso, Ltd. is developing a patient monitoring solution for a hospital. The solution consists of an Azure
website and a set of mobile applications that health care providers use to monitor patients remotely.
Monitoring devices that run the embedded version of Windows will be attached to patients. The devices will
collect information from patients and will transmit real-time continuous data to a service that runs on Azure. The
service collects and distributes data. The data that the service provides must be accessible by the website and
by the mobile applications.
Business Requirements
Patients
All patient data must be stored securely on Azure. Data security must meet or exceed Health Insurance
Portability and Accountability Act of 1996 (HIPAA) standards in the United States and must meet or exceed
ISO/ICE 27002 data security standards in the rest of the world.
Contractors
Third-party contractors will develop the mobile applications. All contractors must develop the applications by
using virtual machines (VMs) that are hosted on Azure. Only authorized contractors and authorized IP
addresses are permitted to access the VMs. The contractors can use Near Field Communication (NFC) tags to
launch Remote Desktop (RD) connections to the VMs from NFC-enabled devices. For testing purposes,
contractors must be able to run multiple instances of mobile applications within the VMs.
Data Collection and Distribution Service
The service must monitor the patient data and send out alerts to health care providers when specific conditions
are detected. The service must send the alerts to mobile applications and to the website in real time so that
doctors, nurses, and caregivers can attend to the patient. Partner organizations and diagnostic laboratories
must be able to securely access the data and the website from remote locations.
Current Issues
A partner that is testing a prototype of the website reports that after signing in to the website, the partner is
redirected to the settings page instead of to the home page.
The data from the patient devices is slow to appear on the website and does not always appear. All patient
devices online have active connections to the data collection service.
Technical Requirements
Contractors
All contractors will use virtual machines that are initially configured as size A3. Contractors must sign in to the
assigned VM by using IP addresses from a list of preapproved addresses.
Data Collection and Distribution Service
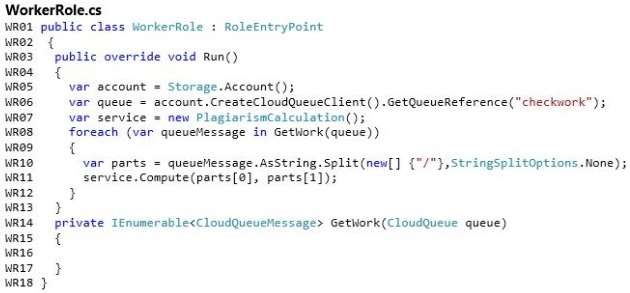
The service runs Node.js in a worker role.
The service must use at least 2048-bit encryption and must use port 8888.
All patient information must be encrypted and stored by using a NoSQL data store.
Data must be stored and retrieved securely by using RESTful endpoints.
Data must NOT be stored within a virtual machine.
All deployed services must send an alert email to watchguard@contoso.com when any of the following
conditions is met:
The CPU Percentage metric is at or above 85 percent for at least 10 minutes.
The Network In metric is at or above 2 KB for at least 10 minutes.
The Network Out metric is at or above 2 KB for at least 10 minutes.
The Disk Write metric is at or above 1 KB/sec for at least 30 minutes.
The Disk Read metric is at or above 1 KB/sec for at least 30 minutes.
Website and Mobile Devices
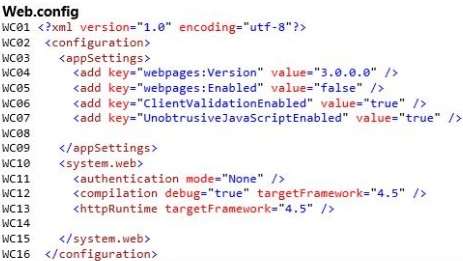
The website must be secure and must be accessible only within the hospital’s physical grounds. All mobileapplications and websites must be responsive. All websites must produce error logs that can be viewed
remotely.
Virtual Machines
All Azure instances must be deployed and tested on staging instances before they are deployed to
production instances.
All deployed instances must scale up to the next available CPU instance at a CPU usage threshold of 90
percent and scale down when the usage is below 10 percent.
Application Structure
Relevant portions of the application files are shown in the following code segments. Line numbers in the code
segments are included for reference only and include a two-character prefix that denotes the specific file to
which they belong.
###EndCaseStudy###
Users report that after periods of inactivity the website is slow to render pages and to process sign-in attempts.
You need to ensure that the website is always responsive.
What should you do?
Which Windows PowerShell command should you use?
###BeginCaseStudy###
Testlet 1
Background
Contoso, Ltd. is developing a patient monitoring solution for a hospital. The solution consists of an Azure
website and a set of mobile applications that health care providers use to monitor patients remotely.
Monitoring devices that run the embedded version of Windows will be attached to patients. The devices will
collect information from patients and will transmit real-time continuous data to a service that runs on Azure. The
service collects and distributes data. The data that the service provides must be accessible by the website and
by the mobile applications.
Business Requirements
Patients
All patient data must be stored securely on Azure. Data security must meet or exceed Health Insurance
Portability and Accountability Act of 1996 (HIPAA) standards in the United States and must meet or exceed
ISO/ICE 27002 data security standards in the rest of the world.
Contractors
Third-party contractors will develop the mobile applications. All contractors must develop the applications by
using virtual machines (VMs) that are hosted on Azure. Only authorized contractors and authorized IP
addresses are permitted to access the VMs. The contractors can use Near Field Communication (NFC) tags to
launch Remote Desktop (RD) connections to the VMs from NFC-enabled devices. For testing purposes,
contractors must be able to run multiple instances of mobile applications within the VMs.
Data Collection and Distribution Service
The service must monitor the patient data and send out alerts to health care providers when specific conditions
are detected. The service must send the alerts to mobile applications and to the website in real time so that
doctors, nurses, and caregivers can attend to the patient. Partner organizations and diagnostic laboratories
must be able to securely access the data and the website from remote locations.
Current Issues
A partner that is testing a prototype of the website reports that after signing in to the website, the partner is
redirected to the settings page instead of to the home page.
The data from the patient devices is slow to appear on the website and does not always appear. All patient
devices online have active connections to the data collection service.
Technical Requirements
Contractors
All contractors will use virtual machines that are initially configured as size A3. Contractors must sign in to the
assigned VM by using IP addresses from a list of preapproved addresses.
Data Collection and Distribution Service
The service runs Node.js in a worker role.
The service must use at least 2048-bit encryption and must use port 8888.
All patient information must be encrypted and stored by using a NoSQL data store.
Data must be stored and retrieved securely by using RESTful endpoints.
Data must NOT be stored within a virtual machine.
All deployed services must send an alert email to watchguard@contoso.com when any of the following
conditions is met:
The CPU Percentage metric is at or above 85 percent for at least 10 minutes.
The Network In metric is at or above 2 KB for at least 10 minutes.
The Network Out metric is at or above 2 KB for at least 10 minutes.
The Disk Write metric is at or above 1 KB/sec for at least 30 minutes.
The Disk Read metric is at or above 1 KB/sec for at least 30 minutes.
Website and Mobile Devices
The website must be secure and must be accessible only within the hospital’s physical grounds. All mobileapplications and websites must be responsive. All websites must produce error logs that can be viewed
remotely.
Virtual Machines
All Azure instances must be deployed and tested on staging instances before they are deployed to
production instances.
All deployed instances must scale up to the next available CPU instance at a CPU usage threshold of 90
percent and scale down when the usage is below 10 percent.
Application Structure
Relevant portions of the application files are shown in the following code segments. Line numbers in the code
segments are included for reference only and include a two-character prefix that denotes the specific file to
which they belong.
###EndCaseStudy###
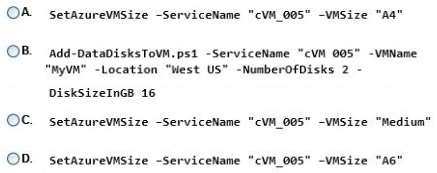
You create a VM named cVM_005 for a newly hired contractor.
The contractor reports that the VM runs out of memory when the contractor attempts to test the mobile
applications.
You need to double the memory that is available for the VM.
Which Windows PowerShell command should you use?
You need to implement data storage for patient information
###BeginCaseStudy###
Testlet 1
Background
Contoso, Ltd. is developing a patient monitoring solution for a hospital. The solution consists of an Azure
website and a set of mobile applications that health care providers use to monitor patients remotely.
Monitoring devices that run the embedded version of Windows will be attached to patients. The devices will
collect information from patients and will transmit real-time continuous data to a service that runs on Azure. The
service collects and distributes data. The data that the service provides must be accessible by the website and
by the mobile applications.
Business Requirements
Patients
All patient data must be stored securely on Azure. Data security must meet or exceed Health Insurance
Portability and Accountability Act of 1996 (HIPAA) standards in the United States and must meet or exceed
ISO/ICE 27002 data security standards in the rest of the world.
Contractors
Third-party contractors will develop the mobile applications. All contractors must develop the applications by
using virtual machines (VMs) that are hosted on Azure. Only authorized contractors and authorized IP
addresses are permitted to access the VMs. The contractors can use Near Field Communication (NFC) tags to
launch Remote Desktop (RD) connections to the VMs from NFC-enabled devices. For testing purposes,
contractors must be able to run multiple instances of mobile applications within the VMs.
Data Collection and Distribution Service
The service must monitor the patient data and send out alerts to health care providers when specific conditions
are detected. The service must send the alerts to mobile applications and to the website in real time so that
doctors, nurses, and caregivers can attend to the patient. Partner organizations and diagnostic laboratories
must be able to securely access the data and the website from remote locations.
Current Issues
A partner that is testing a prototype of the website reports that after signing in to the website, the partner is
redirected to the settings page instead of to the home page.
The data from the patient devices is slow to appear on the website and does not always appear. All patient
devices online have active connections to the data collection service.
Technical Requirements
Contractors
All contractors will use virtual machines that are initially configured as size A3. Contractors must sign in to the
assigned VM by using IP addresses from a list of preapproved addresses.
Data Collection and Distribution Service
The service runs Node.js in a worker role.
The service must use at least 2048-bit encryption and must use port 8888.
All patient information must be encrypted and stored by using a NoSQL data store.
Data must be stored and retrieved securely by using RESTful endpoints.
Data must NOT be stored within a virtual machine.
All deployed services must send an alert email to watchguard@contoso.com when any of the following
conditions is met:
The CPU Percentage metric is at or above 85 percent for at least 10 minutes.
The Network In metric is at or above 2 KB for at least 10 minutes.
The Network Out metric is at or above 2 KB for at least 10 minutes.
The Disk Write metric is at or above 1 KB/sec for at least 30 minutes.
The Disk Read metric is at or above 1 KB/sec for at least 30 minutes.
Website and Mobile Devices
The website must be secure and must be accessible only within the hospital’s physical grounds. All mobileapplications and websites must be responsive. All websites must produce error logs that can be viewed
remotely.
Virtual Machines
All Azure instances must be deployed and tested on staging instances before they are deployed to
production instances.
All deployed instances must scale up to the next available CPU instance at a CPU usage threshold of 90
percent and scale down when the usage is below 10 percent.
Application Structure
Relevant portions of the application files are shown in the following code segments. Line numbers in the code
segments are included for reference only and include a two-character prefix that denotes the specific file to
which they belong.
###EndCaseStudy###
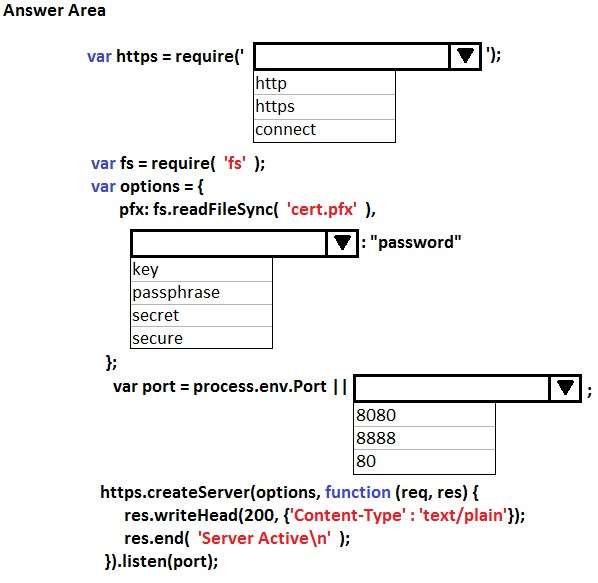
You need to implement data storage for patient information.
What should you do?
How should you complete the relevant code?
###BeginCaseStudy###
Testlet 1
Background
Contoso, Ltd. is developing a patient monitoring solution for a hospital. The solution consists of an Azure
website and a set of mobile applications that health care providers use to monitor patients remotely.
Monitoring devices that run the embedded version of Windows will be attached to patients. The devices will
collect information from patients and will transmit real-time continuous data to a service that runs on Azure. The
service collects and distributes data. The data that the service provides must be accessible by the website and
by the mobile applications.
Business Requirements
Patients
All patient data must be stored securely on Azure. Data security must meet or exceed Health Insurance
Portability and Accountability Act of 1996 (HIPAA) standards in the United States and must meet or exceed
ISO/ICE 27002 data security standards in the rest of the world.
Contractors
Third-party contractors will develop the mobile applications. All contractors must develop the applications by
using virtual machines (VMs) that are hosted on Azure. Only authorized contractors and authorized IP
addresses are permitted to access the VMs. The contractors can use Near Field Communication (NFC) tags to
launch Remote Desktop (RD) connections to the VMs from NFC-enabled devices. For testing purposes,
contractors must be able to run multiple instances of mobile applications within the VMs.
Data Collection and Distribution Service
The service must monitor the patient data and send out alerts to health care providers when specific conditions
are detected. The service must send the alerts to mobile applications and to the website in real time so that
doctors, nurses, and caregivers can attend to the patient. Partner organizations and diagnostic laboratories
must be able to securely access the data and the website from remote locations.
Current Issues
A partner that is testing a prototype of the website reports that after signing in to the website, the partner is
redirected to the settings page instead of to the home page.
The data from the patient devices is slow to appear on the website and does not always appear. All patient
devices online have active connections to the data collection service.
Technical Requirements
Contractors
All contractors will use virtual machines that are initially configured as size A3. Contractors must sign in to the
assigned VM by using IP addresses from a list of preapproved addresses.
Data Collection and Distribution Service
The service runs Node.js in a worker role.
The service must use at least 2048-bit encryption and must use port 8888.
All patient information must be encrypted and stored by using a NoSQL data store.
Data must be stored and retrieved securely by using RESTful endpoints.
Data must NOT be stored within a virtual machine.
All deployed services must send an alert email to watchguard@contoso.com when any of the following
conditions is met:
The CPU Percentage metric is at or above 85 percent for at least 10 minutes.
The Network In metric is at or above 2 KB for at least 10 minutes.
The Network Out metric is at or above 2 KB for at least 10 minutes.
The Disk Write metric is at or above 1 KB/sec for at least 30 minutes.
The Disk Read metric is at or above 1 KB/sec for at least 30 minutes.
Website and Mobile Devices
The website must be secure and must be accessible only within the hospital’s physical grounds. All mobileapplications and websites must be responsive. All websites must produce error logs that can be viewed
remotely.
Virtual Machines
All Azure instances must be deployed and tested on staging instances before they are deployed to
production instances.
All deployed instances must scale up to the next available CPU instance at a CPU usage threshold of 90
percent and scale down when the usage is below 10 percent.
Application Structure
Relevant portions of the application files are shown in the following code segments. Line numbers in the code
segments are included for reference only and include a two-character prefix that denotes the specific file to
which they belong.
###EndCaseStudy###
HOTSPOT
You need to implement the worker role to support the real-time continuous data-collection service.
How should you complete the relevant code? To answer, select the appropriate option or options in the answer
area.
Hot Area:
You need to resolve the issue
###BeginCaseStudy###
Testlet 1
Background
Contoso, Ltd. is developing a patient monitoring solution for a hospital. The solution consists of an Azure
website and a set of mobile applications that health care providers use to monitor patients remotely.
Monitoring devices that run the embedded version of Windows will be attached to patients. The devices will
collect information from patients and will transmit real-time continuous data to a service that runs on Azure. The
service collects and distributes data. The data that the service provides must be accessible by the website and
by the mobile applications.
Business Requirements
Patients
All patient data must be stored securely on Azure. Data security must meet or exceed Health Insurance
Portability and Accountability Act of 1996 (HIPAA) standards in the United States and must meet or exceed
ISO/ICE 27002 data security standards in the rest of the world.
Contractors
Third-party contractors will develop the mobile applications. All contractors must develop the applications by
using virtual machines (VMs) that are hosted on Azure. Only authorized contractors and authorized IP
addresses are permitted to access the VMs. The contractors can use Near Field Communication (NFC) tags to
launch Remote Desktop (RD) connections to the VMs from NFC-enabled devices. For testing purposes,
contractors must be able to run multiple instances of mobile applications within the VMs.
Data Collection and Distribution Service
The service must monitor the patient data and send out alerts to health care providers when specific conditions
are detected. The service must send the alerts to mobile applications and to the website in real time so that
doctors, nurses, and caregivers can attend to the patient. Partner organizations and diagnostic laboratories
must be able to securely access the data and the website from remote locations.
Current Issues
A partner that is testing a prototype of the website reports that after signing in to the website, the partner is
redirected to the settings page instead of to the home page.
The data from the patient devices is slow to appear on the website and does not always appear. All patient
devices online have active connections to the data collection service.
Technical Requirements
Contractors
All contractors will use virtual machines that are initially configured as size A3. Contractors must sign in to the
assigned VM by using IP addresses from a list of preapproved addresses.
Data Collection and Distribution Service
The service runs Node.js in a worker role.
The service must use at least 2048-bit encryption and must use port 8888.
All patient information must be encrypted and stored by using a NoSQL data store.
Data must be stored and retrieved securely by using RESTful endpoints.
Data must NOT be stored within a virtual machine.
All deployed services must send an alert email to watchguard@contoso.com when any of the following
conditions is met:
The CPU Percentage metric is at or above 85 percent for at least 10 minutes.
The Network In metric is at or above 2 KB for at least 10 minutes.
The Network Out metric is at or above 2 KB for at least 10 minutes.
The Disk Write metric is at or above 1 KB/sec for at least 30 minutes.
The Disk Read metric is at or above 1 KB/sec for at least 30 minutes.
Website and Mobile Devices
The website must be secure and must be accessible only within the hospital’s physical grounds. All mobileapplications and websites must be responsive. All websites must produce error logs that can be viewed
remotely.
Virtual Machines
All Azure instances must be deployed and tested on staging instances before they are deployed to
production instances.
All deployed instances must scale up to the next available CPU instance at a CPU usage threshold of 90
percent and scale down when the usage is below 10 percent.
Application Structure
Relevant portions of the application files are shown in the following code segments. Line numbers in the code
segments are included for reference only and include a two-character prefix that denotes the specific file to
which they belong.
###EndCaseStudy###
The website does not receive alerts quickly enough.
There is a lengthy delay between the time an alert is sent and when it is received by the Web App.
You need to resolve the issue.
What should you do?
How should you complete the relevant Windows PowerShell…
###BeginCaseStudy###
Testlet 1
Background
You are developing a web-based solution that students and teachers can use to collaborate on written
assignments. Teachers can also use the solution to detect potential plagiarism, and they can manage
assignments and data by using locally accessible network shares.
Business Requirements
The solution consists of three parts: a website where students work on assignments and where teachers view
and grade assignments, the plagiarism detection service, and a connector service to manage data by using a
network share.
The system availability agreement states that operating hours are weekdays between midnight on Sunday and
midnight on Friday.
Plagiarism Service
The plagiarism detection portion of the solution compares a new work against a repository of existing works.
The initial dataset contains a large database of existing works. Teachers upload additional works. In addition,
the service itself searches for other works and adds those works to the repository.
Technical Requirements
Website
The website for the solution must run on an Azure web role.
Plagiarism Service
The plagiarism detection service runs on an Azure worker role. The computation uses a random number
generator. Certain values can result in an infinite loop, so if a particular work item takes longer than one hour to
process, other instances of the service must be able to process the work item. Computation results are cached
in local storage resources to reduce computation time.
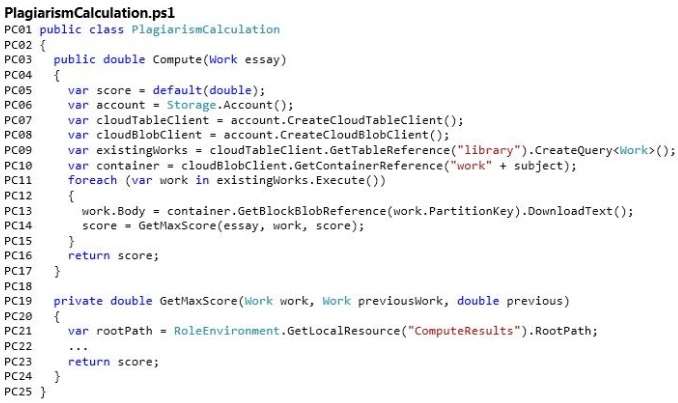
Repository of Existing Works
The plagiarism detection service works by comparing student submissions against a repository of existing
works by using a custom matching algorithm. The master copies of the works are stored in Azure blob storage.
A daily process synchronizes files between blob storage and a file share on a virtual machine (VM). As part of
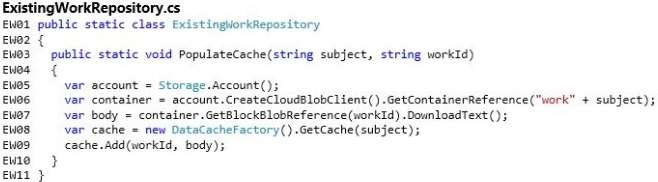
this synchronization, the ExistingWorkRepository object adds the files to Azure Cache to improve the display
performance of the website. If a student’s submission is overdue, the Late property is set to the number of days
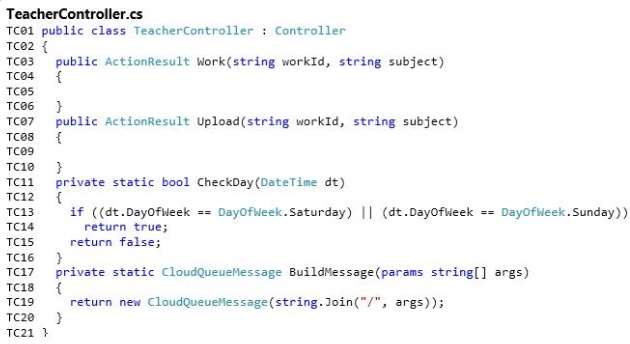
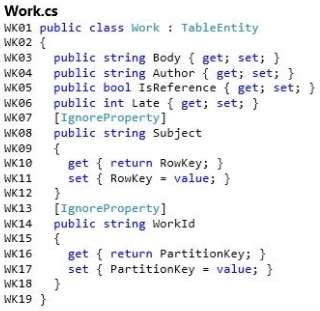
that the work is overdue. Work files can be downloaded by using the Work action of the TeacherController
object
Network Connector
Clients can interact with files that are stored on the VM by using a network share. The network permissions are
configured in a startup task in the plagiarism detection service.
Service Monitoring
The CPU of the system on which the plagiarism detection service runs usually limits the plagiarism detection
service. However, certain combinations of input can cause memory issues, which results in decreased
performance. The average time for a given computation is 45 seconds. Unexpected results during
computations might cause a memory dump. Memory dump files are stored in the Windows temporary folder on
the VM that hosts the worker role.
Security
Only valid users of the solution must be able to view content that users submit. Privacy regulations require that
all content that users submit must be retained only in Azure Storage. All documents that students upload must
be signed by using a certificate named DocCert that is installed in both the worker role and the web role.
Solution Development
You use Microsoft Visual Studio 2013 and the Azure emulator to develop and test both the compute component
and the storage component. New versions of the solution must undergo testing by using production data.Scaling
During non-operating hours, the plagiarism detection service should not use more than 40 CPU cores. During
operating hours, the plagiarism detection service should automatically scale when 500 work items are waiting to
be processed. To facilitate maintenance of the system, no plagiarism detection work should occur during nonoperating hours. All ASP.NET MVC actions must support files that are up to 2 GB in size.
Biographical Information
Biographical information about students and teachers is stored in a Microsoft Azure SQL database. All services
run in the US West region. The plagiarism detection service runs on Extra Large instances. The Azure worker
role must fully utilize all available CPU cores.
Solution Structure
Relevant portions of the solution files are shown in the following code segments. Line numbers in the code
segments are included for reference only and include a two-character prefix that denotes the specific file to
which the line belongs.
###EndCaseStudy###
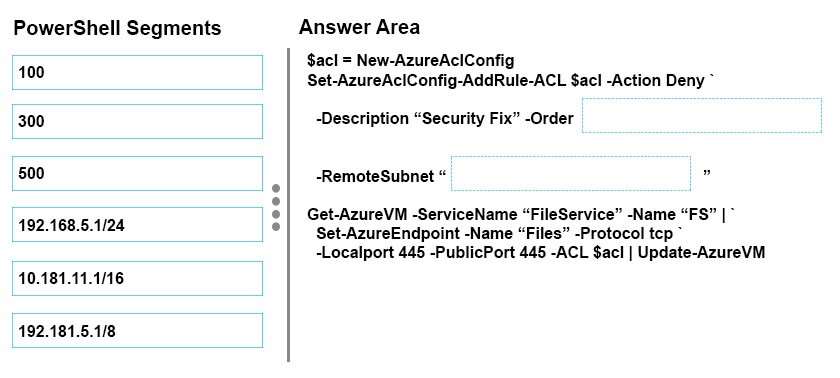
DRAG DROP
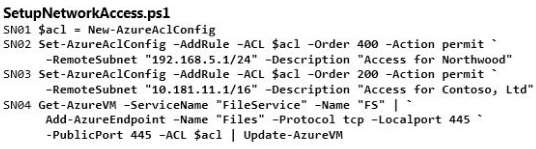
You recently started working with a client named Contoso, Ltd. The client reports that hackers have
compromised devices on its network.
You need to ensure that devices from Contoso cannot connect to your corporate network.
How should you complete the relevant Windows PowerShell script? To answer, drag the appropriate Azure
PowerShell segment to the correct location. Each Azure PowerShell segment may be used once, more than
once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Select and Place:
Which three actions should you perform in sequence?
###BeginCaseStudy###
Testlet 1
Background
Contoso, Ltd. is developing a patient monitoring solution for a hospital. The solution consists of an Azure
website and a set of mobile applications that health care providers use to monitor patients remotely.
Monitoring devices that run the embedded version of Windows will be attached to patients. The devices will
collect information from patients and will transmit real-time continuous data to a service that runs on Azure. The
service collects and distributes data. The data that the service provides must be accessible by the website and
by the mobile applications.
Business Requirements
Patients
All patient data must be stored securely on Azure. Data security must meet or exceed Health Insurance
Portability and Accountability Act of 1996 (HIPAA) standards in the United States and must meet or exceed
ISO/ICE 27002 data security standards in the rest of the world.
Contractors
Third-party contractors will develop the mobile applications. All contractors must develop the applications by
using virtual machines (VMs) that are hosted on Azure. Only authorized contractors and authorized IP
addresses are permitted to access the VMs. The contractors can use Near Field Communication (NFC) tags to
launch Remote Desktop (RD) connections to the VMs from NFC-enabled devices. For testing purposes,
contractors must be able to run multiple instances of mobile applications within the VMs.
Data Collection and Distribution Service
The service must monitor the patient data and send out alerts to health care providers when specific conditions
are detected. The service must send the alerts to mobile applications and to the website in real time so that
doctors, nurses, and caregivers can attend to the patient. Partner organizations and diagnostic laboratories
must be able to securely access the data and the website from remote locations.
Current Issues
A partner that is testing a prototype of the website reports that after signing in to the website, the partner is
redirected to the settings page instead of to the home page.
The data from the patient devices is slow to appear on the website and does not always appear. All patient
devices online have active connections to the data collection service.
Technical Requirements
Contractors
All contractors will use virtual machines that are initially configured as size A3. Contractors must sign in to the
assigned VM by using IP addresses from a list of preapproved addresses.
Data Collection and Distribution Service
The service runs Node.js in a worker role.
The service must use at least 2048-bit encryption and must use port 8888.
All patient information must be encrypted and stored by using a NoSQL data store.
Data must be stored and retrieved securely by using RESTful endpoints.
Data must NOT be stored within a virtual machine.
All deployed services must send an alert email to watchguard@contoso.com when any of the following
conditions is met:
The CPU Percentage metric is at or above 85 percent for at least 10 minutes.
The Network In metric is at or above 2 KB for at least 10 minutes.
The Network Out metric is at or above 2 KB for at least 10 minutes.
The Disk Write metric is at or above 1 KB/sec for at least 30 minutes.
The Disk Read metric is at or above 1 KB/sec for at least 30 minutes.
Website and Mobile Devices
The website must be secure and must be accessible only within the hospital’s physical grounds. All mobileapplications and websites must be responsive. All websites must produce error logs that can be viewed
remotely.
Virtual Machines
All Azure instances must be deployed and tested on staging instances before they are deployed to
production instances.
All deployed instances must scale up to the next available CPU instance at a CPU usage threshold of 90
percent and scale down when the usage is below 10 percent.
Application Structure
Relevant portions of the application files are shown in the following code segments. Line numbers in the code
segments are included for reference only and include a two-character prefix that denotes the specific file to
which they belong.
###EndCaseStudy###
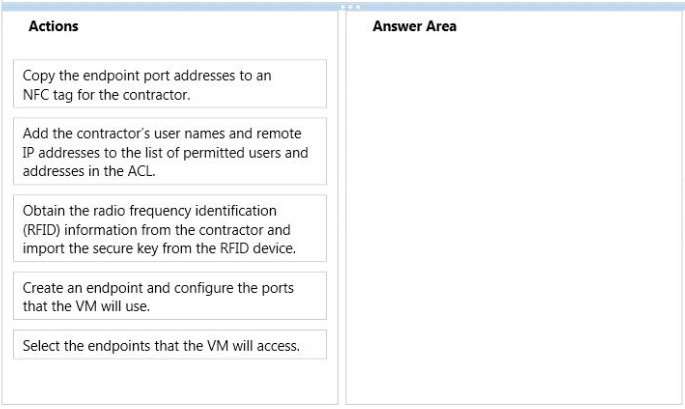
DRAG DROP
You need to configure a VM for a new contractor.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of
actions to the answer area and arrange them in the correct order.
Select and Place:
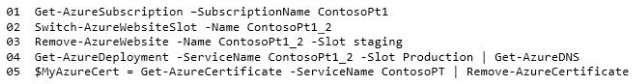
You run the following Windows PowerShell script.
###BeginCaseStudy###
Testlet 1
Background
Contoso, Ltd. is developing a patient monitoring solution for a hospital. The solution consists of an Azure
website and a set of mobile applications that health care providers use to monitor patients remotely.
Monitoring devices that run the embedded version of Windows will be attached to patients. The devices will
collect information from patients and will transmit real-time continuous data to a service that runs on Azure. The
service collects and distributes data. The data that the service provides must be accessible by the website and
by the mobile applications.
Business Requirements
Patients
All patient data must be stored securely on Azure. Data security must meet or exceed Health Insurance
Portability and Accountability Act of 1996 (HIPAA) standards in the United States and must meet or exceed
ISO/ICE 27002 data security standards in the rest of the world.
Contractors
Third-party contractors will develop the mobile applications. All contractors must develop the applications by
using virtual machines (VMs) that are hosted on Azure. Only authorized contractors and authorized IP
addresses are permitted to access the VMs. The contractors can use Near Field Communication (NFC) tags to
launch Remote Desktop (RD) connections to the VMs from NFC-enabled devices. For testing purposes,
contractors must be able to run multiple instances of mobile applications within the VMs.
Data Collection and Distribution Service
The service must monitor the patient data and send out alerts to health care providers when specific conditions
are detected. The service must send the alerts to mobile applications and to the website in real time so that
doctors, nurses, and caregivers can attend to the patient. Partner organizations and diagnostic laboratories
must be able to securely access the data and the website from remote locations.
Current Issues
A partner that is testing a prototype of the website reports that after signing in to the website, the partner is
redirected to the settings page instead of to the home page.
The data from the patient devices is slow to appear on the website and does not always appear. All patient
devices online have active connections to the data collection service.
Technical Requirements
Contractors
All contractors will use virtual machines that are initially configured as size A3. Contractors must sign in to the
assigned VM by using IP addresses from a list of preapproved addresses.
Data Collection and Distribution Service
The service runs Node.js in a worker role.
The service must use at least 2048-bit encryption and must use port 8888.
All patient information must be encrypted and stored by using a NoSQL data store.
Data must be stored and retrieved securely by using RESTful endpoints.
Data must NOT be stored within a virtual machine.
All deployed services must send an alert email to watchguard@contoso.com when any of the following
conditions is met:
The CPU Percentage metric is at or above 85 percent for at least 10 minutes.
The Network In metric is at or above 2 KB for at least 10 minutes.
The Network Out metric is at or above 2 KB for at least 10 minutes.
The Disk Write metric is at or above 1 KB/sec for at least 30 minutes.
The Disk Read metric is at or above 1 KB/sec for at least 30 minutes.
Website and Mobile Devices
The website must be secure and must be accessible only within the hospital’s physical grounds. All mobileapplications and websites must be responsive. All websites must produce error logs that can be viewed
remotely.
Virtual Machines
All Azure instances must be deployed and tested on staging instances before they are deployed to
production instances.
All deployed instances must scale up to the next available CPU instance at a CPU usage threshold of 90
percent and scale down when the usage is below 10 percent.
Application Structure
Relevant portions of the application files are shown in the following code segments. Line numbers in the code
segments are included for reference only and include a two-character prefix that denotes the specific file to
which they belong.
###EndCaseStudy###
HOTSPOT
You run the following Windows PowerShell script. Line numbers are included for reference only.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Hot Area:
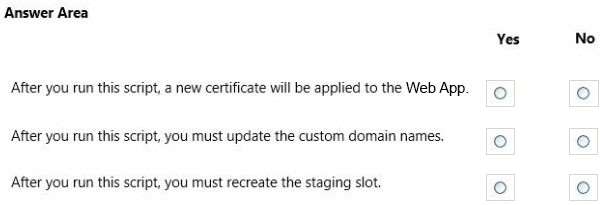
How should you complete the relevant code?
###BeginCaseStudy###
Testlet 1
Background
You are developing a web-based solution that students and teachers can use to collaborate on written
assignments. Teachers can also use the solution to detect potential plagiarism, and they can manage
assignments and data by using locally accessible network shares.
Business Requirements
The solution consists of three parts: a website where students work on assignments and where teachers view
and grade assignments, the plagiarism detection service, and a connector service to manage data by using a
network share.
The system availability agreement states that operating hours are weekdays between midnight on Sunday and
midnight on Friday.
Plagiarism Service
The plagiarism detection portion of the solution compares a new work against a repository of existing works.
The initial dataset contains a large database of existing works. Teachers upload additional works. In addition,
the service itself searches for other works and adds those works to the repository.
Technical Requirements
Website
The website for the solution must run on an Azure web role.
Plagiarism Service
The plagiarism detection service runs on an Azure worker role. The computation uses a random number
generator. Certain values can result in an infinite loop, so if a particular work item takes longer than one hour to
process, other instances of the service must be able to process the work item. Computation results are cached
in local storage resources to reduce computation time.
Repository of Existing Works
The plagiarism detection service works by comparing student submissions against a repository of existing
works by using a custom matching algorithm. The master copies of the works are stored in Azure blob storage.
A daily process synchronizes files between blob storage and a file share on a virtual machine (VM). As part of
this synchronization, the ExistingWorkRepository object adds the files to Azure Cache to improve the display
performance of the website. If a student’s submission is overdue, the Late property is set to the number of days
that the work is overdue. Work files can be downloaded by using the Work action of the TeacherController
object
Network Connector
Clients can interact with files that are stored on the VM by using a network share. The network permissions are
configured in a startup task in the plagiarism detection service.
Service Monitoring
The CPU of the system on which the plagiarism detection service runs usually limits the plagiarism detection
service. However, certain combinations of input can cause memory issues, which results in decreased
performance. The average time for a given computation is 45 seconds. Unexpected results during
computations might cause a memory dump. Memory dump files are stored in the Windows temporary folder on
the VM that hosts the worker role.
Security
Only valid users of the solution must be able to view content that users submit. Privacy regulations require that
all content that users submit must be retained only in Azure Storage. All documents that students upload must
be signed by using a certificate named DocCert that is installed in both the worker role and the web role.
Solution Development
You use Microsoft Visual Studio 2013 and the Azure emulator to develop and test both the compute component
and the storage component. New versions of the solution must undergo testing by using production data.Scaling
During non-operating hours, the plagiarism detection service should not use more than 40 CPU cores. During
operating hours, the plagiarism detection service should automatically scale when 500 work items are waiting to
be processed. To facilitate maintenance of the system, no plagiarism detection work should occur during nonoperating hours. All ASP.NET MVC actions must support files that are up to 2 GB in size.
Biographical Information
Biographical information about students and teachers is stored in a Microsoft Azure SQL database. All services
run in the US West region. The plagiarism detection service runs on Extra Large instances. The Azure worker
role must fully utilize all available CPU cores.
Solution Structure
Relevant portions of the solution files are shown in the following code segments. Line numbers in the code
segments are included for reference only and include a two-character prefix that denotes the specific file to
which the line belongs.
###EndCaseStudy###
HOTSPOT
You need to implement the Work action on the TeacherController object.
How should you complete the relevant code? To answer, select the appropriate options in the answer area.
Hot Area:
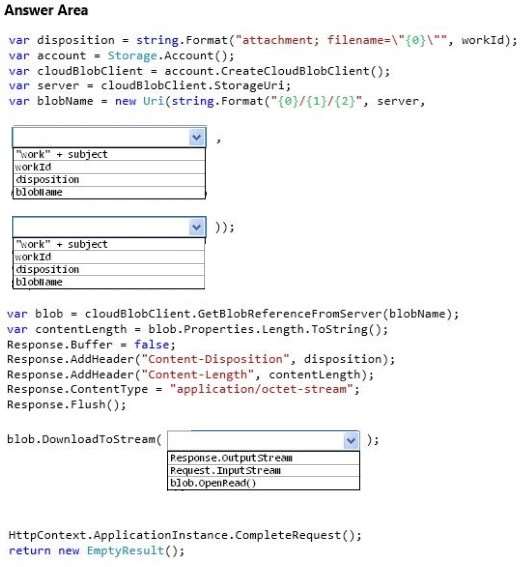
You need to configure scaling for the plagiarism detect…
###BeginCaseStudy###
Testlet 1
Background
You are developing a web-based solution that students and teachers can use to collaborate on written
assignments. Teachers can also use the solution to detect potential plagiarism, and they can manage
assignments and data by using locally accessible network shares.
Business Requirements
The solution consists of three parts: a website where students work on assignments and where teachers view
and grade assignments, the plagiarism detection service, and a connector service to manage data by using a
network share.
The system availability agreement states that operating hours are weekdays between midnight on Sunday and
midnight on Friday.
Plagiarism Service
The plagiarism detection portion of the solution compares a new work against a repository of existing works.
The initial dataset contains a large database of existing works. Teachers upload additional works. In addition,
the service itself searches for other works and adds those works to the repository.
Technical Requirements
Website
The website for the solution must run on an Azure web role.
Plagiarism Service
The plagiarism detection service runs on an Azure worker role. The computation uses a random number
generator. Certain values can result in an infinite loop, so if a particular work item takes longer than one hour to
process, other instances of the service must be able to process the work item. Computation results are cached
in local storage resources to reduce computation time.
Repository of Existing Works
The plagiarism detection service works by comparing student submissions against a repository of existing
works by using a custom matching algorithm. The master copies of the works are stored in Azure blob storage.
A daily process synchronizes files between blob storage and a file share on a virtual machine (VM). As part of
this synchronization, the ExistingWorkRepository object adds the files to Azure Cache to improve the display
performance of the website. If a student’s submission is overdue, the Late property is set to the number of days
that the work is overdue. Work files can be downloaded by using the Work action of the TeacherController
object
Network Connector
Clients can interact with files that are stored on the VM by using a network share. The network permissions are
configured in a startup task in the plagiarism detection service.
Service Monitoring
The CPU of the system on which the plagiarism detection service runs usually limits the plagiarism detection
service. However, certain combinations of input can cause memory issues, which results in decreased
performance. The average time for a given computation is 45 seconds. Unexpected results during
computations might cause a memory dump. Memory dump files are stored in the Windows temporary folder on
the VM that hosts the worker role.
Security
Only valid users of the solution must be able to view content that users submit. Privacy regulations require that
all content that users submit must be retained only in Azure Storage. All documents that students upload must
be signed by using a certificate named DocCert that is installed in both the worker role and the web role.
Solution Development
You use Microsoft Visual Studio 2013 and the Azure emulator to develop and test both the compute component
and the storage component. New versions of the solution must undergo testing by using production data.Scaling
During non-operating hours, the plagiarism detection service should not use more than 40 CPU cores. During
operating hours, the plagiarism detection service should automatically scale when 500 work items are waiting to
be processed. To facilitate maintenance of the system, no plagiarism detection work should occur during nonoperating hours. All ASP.NET MVC actions must support files that are up to 2 GB in size.
Biographical Information
Biographical information about students and teachers is stored in a Microsoft Azure SQL database. All services
run in the US West region. The plagiarism detection service runs on Extra Large instances. The Azure worker
role must fully utilize all available CPU cores.
Solution Structure
Relevant portions of the solution files are shown in the following code segments. Line numbers in the code
segments are included for reference only and include a two-character prefix that denotes the specific file to
which the line belongs.
###EndCaseStudy###
HOTSPOT
You need to configure scaling for the plagiarism detection service.
What should you do? To answer, select the appropriate values in the dialog box in the answer area.
Hot Area: