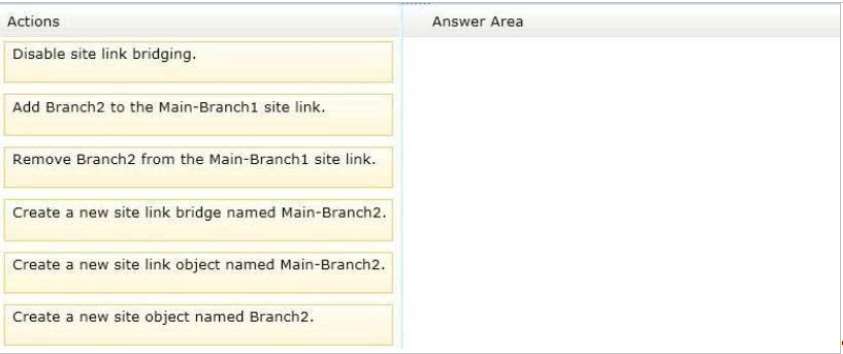
Which three actions should you perform?
DRAG DROP
Your network contains an Active Directory forest. The forest contains a single domain named contoso.com.
The forest contains two Active Directory sites named Main and Branch1. The sites connect to each other by
using a site link named Main-Branch1. There are no other site links.
Each site contains several domain controllers. All domain controllers run Windows Server 2012 R2. Your
company plans to open a new branch site named Branch2. The new site will have a WAN link that connects to
the Main site only. The site will contain two domain controllers that run Windows Server 2012 R2.
You need to create a new site and a new site link for Branch2. The solution must ensure that the domain
controllers in Branch2 only replicate to the domain controllers in Branch1 if all of the domain controllers in Main
are unavailable.
Which three actions should you perform?
To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in
the correct order.
Select and Place:
How should you configure the witness disk?
DRAG DROP
Your network contains an Active Directory domain named contoso.com. The domain contains two member
servers named Server1 and Server2 that run Windows Server 2012 R2.
You configure a new failover cluster named Cluster1. Server1 and Server2 are nodes in Cluster1. You need to
configure the disk that will be used as a witness disk for Cluster1.
How should you configure the witness disk?
To answer, drag the appropriate configurations to the correct location or locations. Each configuration may be
used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view
content.
Select and Place:
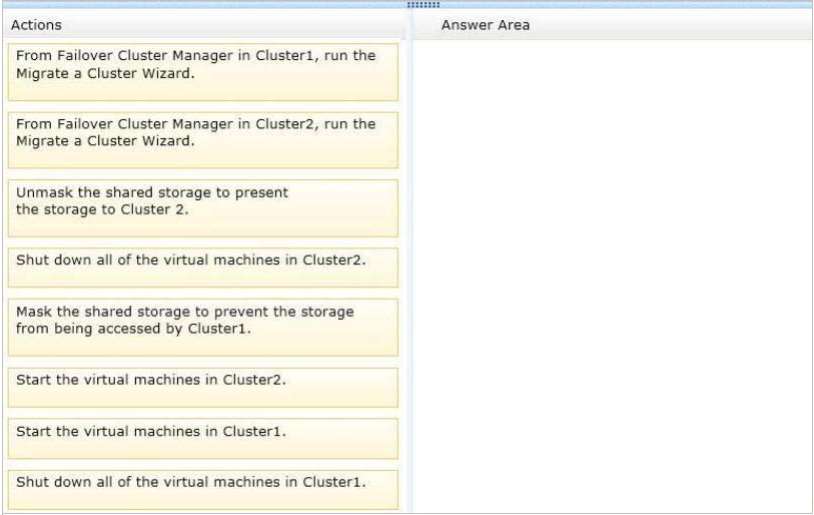
Which five actions should you perform?
DRAG DROP
Your network contains an Active Directory domain named contoso.com. The domain contains four member
servers named Server1, Server2, Server3, and Server4. Server1 and Server2 run Windows Server 2008 R2.
Server1 and Server2 have the Hyper-V server role and the Failover Clustering feature installed. Failover
Clustering is configured to provide highly available virtual machines by using a cluster named Cluster1.
Cluster1 hosts 10 virtual machines.
Server3 and Server4 run Windows Server 2012 R2.
You install the Hyper-V server role and the Failover Clustering feature on Server3 and Server4. You create a
cluster named Cluster2.
You need to migrate cluster resources from Cluster1 to Cluster2. The solution must minimize downtime on the
virtual machines.Which five actions should you perform?
To answer, move the appropriate five actions from the list of actions to the answer area and arrange them in
the correct order.
Select and Place:
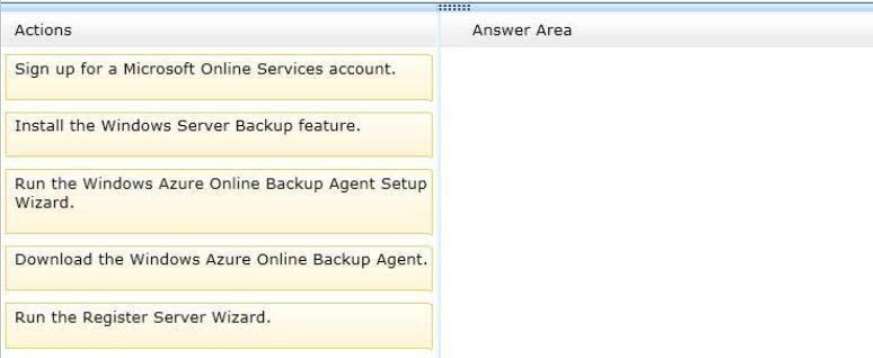
Which four actions should you perform in sequence?
DRAG DROP
You have 3 server named Server1 that runs Windows Server 2012 R2.
You are asked to test Windows Azure Online Backup to back up Server1.
You need to back up Server1 by using Windows Azure Online Backup.
Which four actions should you perform in sequence?
To answer, move the appropriate four actions from the list of actions to the answer area and arrange them in
the correct order.
Select and Place:
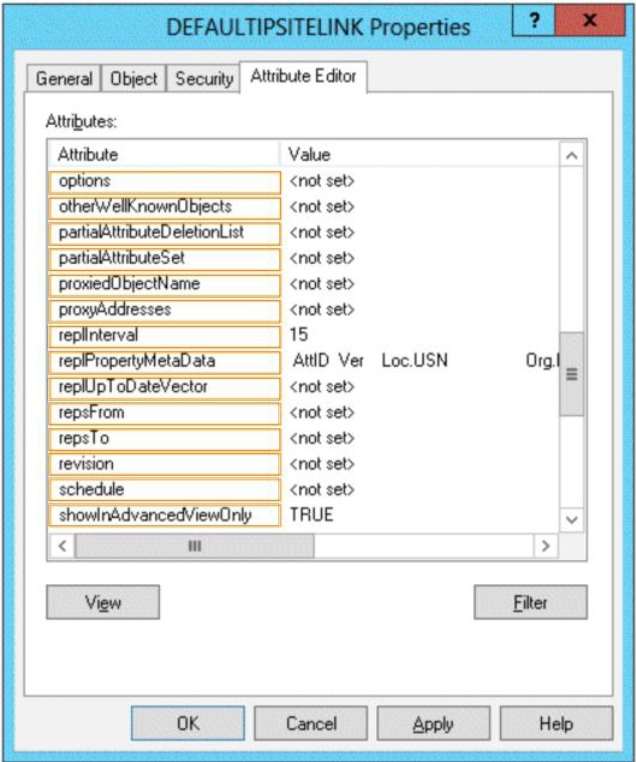
Which attribute should you modify?
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains two Active
Directory sites named Site1 and Site2.
You discover that when the account of a user in Site1 is locked out, the user can still log on to the servers in
Site2 for up to 15 minutes by using Remote Desktop Services (RDS).
You need to reduce the amount of time it takes to synchronize account lockout information across the domain.
Which attribute should you modify?
To answer, select the appropriate attribute in the answer area.
Hot Area:
Each correct selection is worth one point.Hot Area:
HOTSPOT
Your network contains an Active Directory forest.
You implement Dynamic Access Control in the forest.
You have the claim types shown in the Claim Types exhibit. (Click the Exhibit button.)
The properties of a user named User1 are configured as shown in the User1 exhibit. (Click the Exhibit button.)
The output of Whoami /claims for a user named User2 is shown in the Whoami exhibit. (Click the Exhibit
button.)
Select Yes if the statement can be shown to be true based on the available information; otherwise select No.
Each correct selection is worth one point.Hot Area:
What should you configure?
Your network contains an Active Directory domain named adatum.com. The domain contains a file server
named FS1 that runs Windows Server 2012 R2 and has the File Server Resource Manager role service
installed. All client computers run Windows 8.
File classification and Access-Denied Assistance are enabled on FS1.
You need to ensure that if users receive an Access Denied message, they can request assistance by email
from the Access Denied dialog box.
What should you configure?
Which two actions should you perform?
Your network contains an Active Directory domain named contoso.com. The domain contains a server named
Server1 that runs Windows Server 2012 R2.
Server1 is an enterprise root certification authority (CA) for contoso.com.
You need to ensure that the members of a group named Group1 can request code signing certificates. The
certificates must be issued automatically to the members.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
You need to ensure that a user named User1 can decrypt …
Your network contains an Active Directory domain named adatum.com. The domain contains a server named
CA1 that runs Windows Server 2012 R2. CA1 has the Active Directory Certificate Services server role installed
and is configured to support key archival and recovery.
You need to ensure that a user named User1 can decrypt private keys archived in the Active Directory
Certificate Services (AD CS) database. The solution must prevent User1 from retrieving the private keys from
the AD CS database.
What should you do?
Which two actions should you perform?
Your network contains an Active Directory domain named contoso.com. The domain contains a certification
authority (CA).
You suspect that a certificate issued to a Web server is compromised.
You need to minimize the likelihood that users will trust the compromised certificate.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)