What should you modify from the port settings?
Your network contains an Active Directory domain named contoso.com.
The domain contains a Network Load Balancing (NLB) cluster named Cluster1 that contains four nodes.
Cluster1 hosts a web application named App1.
The session state information of App1 is stored in a Microsoft SQL Server 2012 database.
The network contains four subnets.
You discover that all of the users from a subnet named Subnet1 always connect to the same NLB node.
You need to ensure that all of the users from each of the subnets connect equally across all of the nodes in Cluster1.
What should you modify from the port settings? To answer, select the appropriate setting in the answer area.
Hot Area:
What should you include in the backup plan?
Your network contains five physical servers.
The servers are configured as shown in the following table.
All servers run Windows Server 2012 R2.
During the setup of VMM, you configure distributed key management.
You need to ensure that the entire VMM infrastructure can be restored.
What should you include in the backup plan? To answer, select the appropriate server to back up for each backup content type in the answer.
Hot Area:
Hot Area:
Your network contains an Active Directory domain named contoso.com.
All servers run Windows Server 2012 R2.
System Center 2012 R2 Virtual Machine Manager (VMM) is deployed to the domain.
In VMM, you create a host group named HostGroup1.
You add a 16-node Hyper-V failover cluster to HostGroup1.
From Windows PowerShell, you run the following commands:
Use the drop-down menus to select the answer choice that completes each statement.
Hot Area:
Which cmdlet should you run to achieve each requirement?
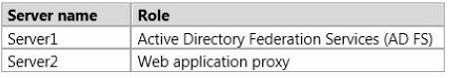
Your network contains an Active Directory forest named contoso.com.
All servers run Windows Server 2012 R2.
The forest contains two servers.
The servers are configured as shown in the following table.
You prepare the forest to support Workplace Join and you enable the Device Registration Service (DRS) on Server1.
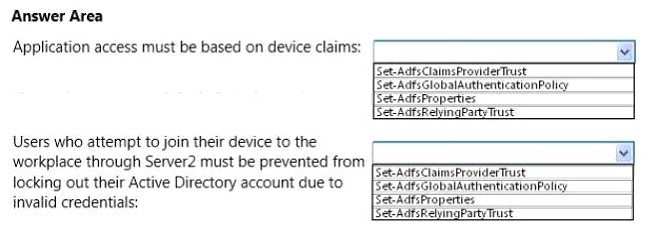
You need to ensure that Workplace Join meets the following requirements:
– Application access must be based on device claims.
– Users who attempt to join their device to the workplace through Server2 must be prevented from locking out their
Active Directory account due to invalid credentials.
Which cmdlet should you run to achieve each requirement? To answer, select the cmdlet for each requirement in the answer area.
Hot Area:
You need to recommend which actions must be performed o…
You have a failover cluster named Cluster1 that contains two Hyper-V hosts named Hyped. and Hyper2. Clusterl hosts 15 virtual machines.
You deploy a new server named Hyper3.
You plan to replicate the virtual machines from Clusterl to Hyper3.
You need to recommend which actions must be performed on Hyper3 for the planned deployment.
Select and Place:
Which three actions should you perform?
Your network contains two servers named Server1 and Server2 that run Windows Server 2012.
Server1 has the iSCSI Target Server role service installed and is configured to have five iSCSI virtual disks.
You install the Multipath I/O (MPIO) feature on Server2.
From the MPIO snap-in, you add support for iSCSI devices.
You need to ensure that Server2 can connect to the five iSCSI disks.
The solution must ensure that Server2 uses MPIO to access the disks.
Which three actions should you perform? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct
order.
Exhibit:
Select and Place:
Which four actions should you perform in sequence?
Which four actions should you perform in sequence?
Your network contains an Active Directory domain named contoso.com.
The domain contains two domain controllers named DC1 and DC2.
The domain contains a server named Server1.
Server1 is a certification authority (CA).
All servers run Windows Server 2012 R2.
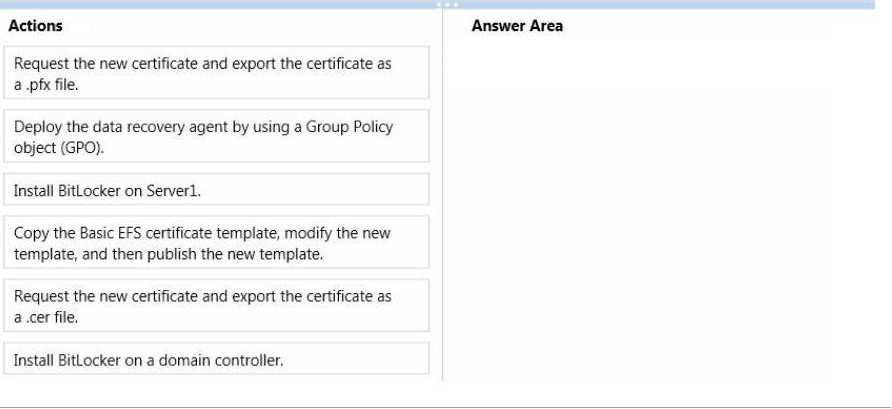
You plan to deploy BitLocker Drive Encryption (BitLocker) to all client computers.
The unique identifier for your organization is set to Contoso.
You need to ensure that you can recover the BitLocker encrypted data by using a BitLocker data recovery agent.
You must be able to perform the recovery from any administrative computer.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the
correct order.
Select and Place:
Which three actions should you recommend?
Your network contains an Active Directory domain named contoso.com.
The network has an Active Directory Certificate Services (AD CS) infrastructure.
You publish the certificate revocation list (CRL) to a farm of Web servers.
You are creating a disaster recovery plan for the AD CS infrastructure.
You need to recommend which actions must be performed to restore certificate revocation checking if a certification authority (CA) is offline for an
extended period of time.
Which three actions should you recommend? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the
correct order.
Select and Place:
Which network types should you identify?
Your network contains an Active Directory domain named contoso.com.
The domain contains multiple servers that are configured as Hyper-V hosts.
You plan to implement four virtual machines.
The virtual machines will be configured as shown in the following table.
You need to identify which network must be added to each virtual machine.
Which network types should you identify? To answer, drag the appropriate Network Type to the correct virtual machine in the answer area. Each Network Type may
be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
Select and Place: