Hot Area:
###BeginCaseStudy###
Case Study 6: Contoso Ltd Case D
Overview
Contoso, Ltd., is a manufacturing company that makes several different components that are used in automobile production. Contoso has a main office in Detroit, a
distribution center in Chicago, and branch offices in Dallas, Atlanta, and San Diego. The contoso.com forest and domain functional level are Windows Server 2008
R2. All servers run Windows Server 2012 R2, and all client workstations run Windows 7 or Windows 8. Contoso uses System Center 2012 Operations Manager and
Audit Collection Services (ACS) to monitor the environment. There is no certification authority (CA) in the environment.
Current Environment
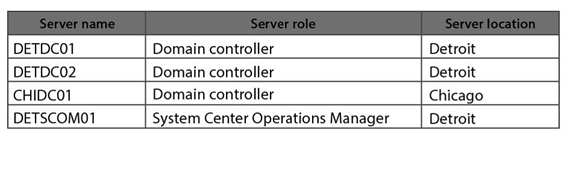
The contoso.com domain contains the servers as shown in the following table:
Contoso sales staff travel within the United States and connect to a VPN by using mobile devices to access the corporate network. Sales users authenticate to the
VPN by using their Active Directory usernames and passwords. The VPN solution also supports certification-based authentication.
Contoso uses an inventory system that requires manually counting products and entering that count into a database. Contoso purchases new inventory software
that supports wireless handheld scanners and several wireless handheld scanners. The wireless handheld scanners run a third party operating system that supports
the Network Device Enrollment Service (NDES).
Business Requirements
Security
The wireless handheld scanners must use certification-based authentication to access the wireless network.
Sales users who use mobile devices must use certification-based authentication to access the VPN. When sales users leave the company, Contoso administrators
must be able to disable their VPN access by revoking their certificates.
Monitoring
All servers must be monitored by using System Center 2012 Operating Manager. In addition to monitoring the Windows operating system, you must collect security
logs from the CA servers by using ACS, and monitor the services that run on the CA and Certificate Revocation List (CRL) servers, such as certification authority
and web services.
Technical Requirements
CA Hierarchy
Contoso requires a two-tier CA hierarchy. The CA hierarchy must include a stand-alone offline root and two Active Directory-integrated issuing CAs: one for issuing
certificates to domain-joined devices, and one for issuing certificates to non-domain-joined devices by using the NDES. CRLs must be published to two web servers:
one in Detroit and one in Chicago.
Contoso has servers that run Windows Server 2012 R2 to use for the CA hierarchy. The servers are described in the following table:
The IT security department must have the necessary permissions to manage the CA and CRL servers. A domain group named Corp-IT Security must be used for
this purpose.
The IT security department users are not domain admins.
Fault Tolerance
The servers that host the CRL must be part of a Windows Network Load Balancing (NLB) cluster. The CRL must be available to users in all locations by using the
hostname crl.contoso.com, even if one of the underlying web servers is offline.
###EndCaseStudy###
Hotspot Question
You plan to configure Windows Network Load Balancing (NLB) for a company.
You display following Network Load Balancing Manager window:
Use the drop-down menus to select the answer choice that answers each question based on the information presented in the graphic.
Hot Area:
How should you configure the access?
###BeginCaseStudy###
Case Study 6: Contoso Ltd Case D
Overview
Contoso, Ltd., is a manufacturing company that makes several different components that are used in automobile production. Contoso has a main office in Detroit, a
distribution center in Chicago, and branch offices in Dallas, Atlanta, and San Diego. The contoso.com forest and domain functional level are Windows Server 2008
R2. All servers run Windows Server 2012 R2, and all client workstations run Windows 7 or Windows 8. Contoso uses System Center 2012 Operations Manager and
Audit Collection Services (ACS) to monitor the environment. There is no certification authority (CA) in the environment.
Current Environment
The contoso.com domain contains the servers as shown in the following table:
Contoso sales staff travel within the United States and connect to a VPN by using mobile devices to access the corporate network. Sales users authenticate to the
VPN by using their Active Directory usernames and passwords. The VPN solution also supports certification-based authentication.
Contoso uses an inventory system that requires manually counting products and entering that count into a database. Contoso purchases new inventory software
that supports wireless handheld scanners and several wireless handheld scanners. The wireless handheld scanners run a third party operating system that supports
the Network Device Enrollment Service (NDES).
Business Requirements
Security
The wireless handheld scanners must use certification-based authentication to access the wireless network.
Sales users who use mobile devices must use certification-based authentication to access the VPN. When sales users leave the company, Contoso administrators
must be able to disable their VPN access by revoking their certificates.
Monitoring
All servers must be monitored by using System Center 2012 Operating Manager. In addition to monitoring the Windows operating system, you must collect security
logs from the CA servers by using ACS, and monitor the services that run on the CA and Certificate Revocation List (CRL) servers, such as certification authority
and web services.
Technical Requirements
CA Hierarchy
Contoso requires a two-tier CA hierarchy. The CA hierarchy must include a stand-alone offline root and two Active Directory-integrated issuing CAs: one for issuing
certificates to domain-joined devices, and one for issuing certificates to non-domain-joined devices by using the NDES. CRLs must be published to two web servers:
one in Detroit and one in Chicago.
Contoso has servers that run Windows Server 2012 R2 to use for the CA hierarchy. The servers are described in the following table:
The IT security department must have the necessary permissions to manage the CA and CRL servers. A domain group named Corp-IT Security must be used for
this purpose.
The IT security department users are not domain admins.
Fault Tolerance
The servers that host the CRL must be part of a Windows Network Load Balancing (NLB) cluster. The CRL must be available to users in all locations by using the
hostname crl.contoso.com, even if one of the underlying web servers is offline.
###EndCaseStudy###
Drag and Drop Question
You need to configure access to the Certificate Revocation Lists (CRLs).
How should you configure the access? To answer, drag the appropriate protocol or servers to the correct network type. Each protocol or server may be used once,
more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Select and Place:
Which three actions should you perform in sequence?
###BeginCaseStudy###
Case Study 6: Contoso Ltd Case D
Overview
Contoso, Ltd., is a manufacturing company that makes several different components that are used in automobile production. Contoso has a main office in Detroit, a
distribution center in Chicago, and branch offices in Dallas, Atlanta, and San Diego. The contoso.com forest and domain functional level are Windows Server 2008
R2. All servers run Windows Server 2012 R2, and all client workstations run Windows 7 or Windows 8. Contoso uses System Center 2012 Operations Manager and
Audit Collection Services (ACS) to monitor the environment. There is no certification authority (CA) in the environment.
Current Environment
The contoso.com domain contains the servers as shown in the following table:
Contoso sales staff travel within the United States and connect to a VPN by using mobile devices to access the corporate network. Sales users authenticate to the
VPN by using their Active Directory usernames and passwords. The VPN solution also supports certification-based authentication.
Contoso uses an inventory system that requires manually counting products and entering that count into a database. Contoso purchases new inventory software
that supports wireless handheld scanners and several wireless handheld scanners. The wireless handheld scanners run a third party operating system that supports
the Network Device Enrollment Service (NDES).
Business Requirements
Security
The wireless handheld scanners must use certification-based authentication to access the wireless network.
Sales users who use mobile devices must use certification-based authentication to access the VPN. When sales users leave the company, Contoso administrators
must be able to disable their VPN access by revoking their certificates.
Monitoring
All servers must be monitored by using System Center 2012 Operating Manager. In addition to monitoring the Windows operating system, you must collect security
logs from the CA servers by using ACS, and monitor the services that run on the CA and Certificate Revocation List (CRL) servers, such as certification authority
and web services.
Technical Requirements
CA Hierarchy
Contoso requires a two-tier CA hierarchy. The CA hierarchy must include a stand-alone offline root and two Active Directory-integrated issuing CAs: one for issuing
certificates to domain-joined devices, and one for issuing certificates to non-domain-joined devices by using the NDES. CRLs must be published to two web servers:
one in Detroit and one in Chicago.
Contoso has servers that run Windows Server 2012 R2 to use for the CA hierarchy. The servers are described in the following table:
The IT security department must have the necessary permissions to manage the CA and CRL servers. A domain group named Corp-IT Security must be used for
this purpose.
The IT security department users are not domain admins.
Fault Tolerance
The servers that host the CRL must be part of a Windows Network Load Balancing (NLB) cluster. The CRL must be available to users in all locations by using the
hostname crl.contoso.com, even if one of the underlying web servers is offline.
###EndCaseStudy###
Drag and Drop Question
You need to delegate permissions for DETCA01.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the
correct order.
Select and Place:
Does this meet the goal?
###BeginCaseStudy###
Case Study 6: Contoso Ltd Case D
Overview
Contoso, Ltd., is a manufacturing company that makes several different components that are used in automobile production. Contoso has a main office in Detroit, a
distribution center in Chicago, and branch offices in Dallas, Atlanta, and San Diego. The contoso.com forest and domain functional level are Windows Server 2008
R2. All servers run Windows Server 2012 R2, and all client workstations run Windows 7 or Windows 8. Contoso uses System Center 2012 Operations Manager and
Audit Collection Services (ACS) to monitor the environment. There is no certification authority (CA) in the environment.
Current Environment
The contoso.com domain contains the servers as shown in the following table:
Contoso sales staff travel within the United States and connect to a VPN by using mobile devices to access the corporate network. Sales users authenticate to the
VPN by using their Active Directory usernames and passwords. The VPN solution also supports certification-based authentication.
Contoso uses an inventory system that requires manually counting products and entering that count into a database. Contoso purchases new inventory software
that supports wireless handheld scanners and several wireless handheld scanners. The wireless handheld scanners run a third party operating system that supports
the Network Device Enrollment Service (NDES).
Business Requirements
Security
The wireless handheld scanners must use certification-based authentication to access the wireless network.
Sales users who use mobile devices must use certification-based authentication to access the VPN. When sales users leave the company, Contoso administrators
must be able to disable their VPN access by revoking their certificates.
Monitoring
All servers must be monitored by using System Center 2012 Operating Manager. In addition to monitoring the Windows operating system, you must collect security
logs from the CA servers by using ACS, and monitor the services that run on the CA and Certificate Revocation List (CRL) servers, such as certification authority
and web services.
Technical Requirements
CA Hierarchy
Contoso requires a two-tier CA hierarchy. The CA hierarchy must include a stand-alone offline root and two Active Directory-integrated issuing CAs: one for issuing
certificates to domain-joined devices, and one for issuing certificates to non-domain-joined devices by using the NDES. CRLs must be published to two web servers:
one in Detroit and one in Chicago.
Contoso has servers that run Windows Server 2012 R2 to use for the CA hierarchy. The servers are described in the following table:
The IT security department must have the necessary permissions to manage the CA and CRL servers. A domain group named Corp-IT Security must be used for
this purpose.
The IT security department users are not domain admins.
Fault Tolerance
The servers that host the CRL must be part of a Windows Network Load Balancing (NLB) cluster. The CRL must be available to users in all locations by using the
hostname crl.contoso.com, even if one of the underlying web servers is offline.
###EndCaseStudy###
You need to automatically restart the appropriate web service on DETCRL01 and CHICRL01 if the web service is stopped.
Solution: you create a Windows Events monitor SCOM and configure it to monitor even related to the http.sys Service.
Does this meet the goal?
Does this meet the goal?
###BeginCaseStudy###
Case Study 6: Contoso Ltd Case D
Overview
Contoso, Ltd., is a manufacturing company that makes several different components that are used in automobile production. Contoso has a main office in Detroit, a
distribution center in Chicago, and branch offices in Dallas, Atlanta, and San Diego. The contoso.com forest and domain functional level are Windows Server 2008
R2. All servers run Windows Server 2012 R2, and all client workstations run Windows 7 or Windows 8. Contoso uses System Center 2012 Operations Manager and
Audit Collection Services (ACS) to monitor the environment. There is no certification authority (CA) in the environment.
Current Environment
The contoso.com domain contains the servers as shown in the following table:
Contoso sales staff travel within the United States and connect to a VPN by using mobile devices to access the corporate network. Sales users authenticate to the
VPN by using their Active Directory usernames and passwords. The VPN solution also supports certification-based authentication.
Contoso uses an inventory system that requires manually counting products and entering that count into a database. Contoso purchases new inventory software
that supports wireless handheld scanners and several wireless handheld scanners. The wireless handheld scanners run a third party operating system that supports
the Network Device Enrollment Service (NDES).
Business Requirements
Security
The wireless handheld scanners must use certification-based authentication to access the wireless network.
Sales users who use mobile devices must use certification-based authentication to access the VPN. When sales users leave the company, Contoso administrators
must be able to disable their VPN access by revoking their certificates.
Monitoring
All servers must be monitored by using System Center 2012 Operating Manager. In addition to monitoring the Windows operating system, you must collect security
logs from the CA servers by using ACS, and monitor the services that run on the CA and Certificate Revocation List (CRL) servers, such as certification authority
and web services.
Technical Requirements
CA Hierarchy
Contoso requires a two-tier CA hierarchy. The CA hierarchy must include a stand-alone offline root and two Active Directory-integrated issuing CAs: one for issuing
certificates to domain-joined devices, and one for issuing certificates to non-domain-joined devices by using the NDES. CRLs must be published to two web servers:
one in Detroit and one in Chicago.
Contoso has servers that run Windows Server 2012 R2 to use for the CA hierarchy. The servers are described in the following table:
The IT security department must have the necessary permissions to manage the CA and CRL servers. A domain group named Corp-IT Security must be used for
this purpose.
The IT security department users are not domain admins.
Fault Tolerance
The servers that host the CRL must be part of a Windows Network Load Balancing (NLB) cluster. The CRL must be available to users in all locations by using the
hostname crl.contoso.com, even if one of the underlying web servers is offline.
###EndCaseStudy###
You need to automatically restart the appropriate web service on DETCRL01 and CHICRL01 if the web service is stopped.
Solution: You create a diagnostic task in SCOM and configure it to start the Server service.
Does this meet the goal?
Does this meet the goal?
###BeginCaseStudy###
Case Study 6: Contoso Ltd Case D
Overview
Contoso, Ltd., is a manufacturing company that makes several different components that are used in automobile production. Contoso has a main office in Detroit, a
distribution center in Chicago, and branch offices in Dallas, Atlanta, and San Diego. The contoso.com forest and domain functional level are Windows Server 2008
R2. All servers run Windows Server 2012 R2, and all client workstations run Windows 7 or Windows 8. Contoso uses System Center 2012 Operations Manager and
Audit Collection Services (ACS) to monitor the environment. There is no certification authority (CA) in the environment.
Current Environment
The contoso.com domain contains the servers as shown in the following table:
Contoso sales staff travel within the United States and connect to a VPN by using mobile devices to access the corporate network. Sales users authenticate to the
VPN by using their Active Directory usernames and passwords. The VPN solution also supports certification-based authentication.
Contoso uses an inventory system that requires manually counting products and entering that count into a database. Contoso purchases new inventory software
that supports wireless handheld scanners and several wireless handheld scanners. The wireless handheld scanners run a third party operating system that supports
the Network Device Enrollment Service (NDES).
Business Requirements
Security
The wireless handheld scanners must use certification-based authentication to access the wireless network.
Sales users who use mobile devices must use certification-based authentication to access the VPN. When sales users leave the company, Contoso administrators
must be able to disable their VPN access by revoking their certificates.
Monitoring
All servers must be monitored by using System Center 2012 Operating Manager. In addition to monitoring the Windows operating system, you must collect security
logs from the CA servers by using ACS, and monitor the services that run on the CA and Certificate Revocation List (CRL) servers, such as certification authority
and web services.
Technical Requirements
CA Hierarchy
Contoso requires a two-tier CA hierarchy. The CA hierarchy must include a stand-alone offline root and two Active Directory-integrated issuing CAs: one for issuing
certificates to domain-joined devices, and one for issuing certificates to non-domain-joined devices by using the NDES. CRLs must be published to two web servers:
one in Detroit and one in Chicago.
Contoso has servers that run Windows Server 2012 R2 to use for the CA hierarchy. The servers are described in the following table:
The IT security department must have the necessary permissions to manage the CA and CRL servers. A domain group named Corp-IT Security must be used for
this purpose.
The IT security department users are not domain admins.
Fault Tolerance
The servers that host the CRL must be part of a Windows Network Load Balancing (NLB) cluster. The CRL must be available to users in all locations by using the
hostname crl.contoso.com, even if one of the underlying web servers is offline.
###EndCaseStudy###
You need to automatically restart the appropriate web service on DETCRL01 and CHICRL01 if the web service is stopped.
Solution: You create a diagnostic task in SCOM and configure it to start the World Wide Web publishing service.
Does this meet the goal?
Does this meet the goal?
###BeginCaseStudy###
Case Study 6: Contoso Ltd Case D
Overview
Contoso, Ltd., is a manufacturing company that makes several different components that are used in automobile production. Contoso has a main office in Detroit, a
distribution center in Chicago, and branch offices in Dallas, Atlanta, and San Diego. The contoso.com forest and domain functional level are Windows Server 2008
R2. All servers run Windows Server 2012 R2, and all client workstations run Windows 7 or Windows 8. Contoso uses System Center 2012 Operations Manager and
Audit Collection Services (ACS) to monitor the environment. There is no certification authority (CA) in the environment.
Current Environment
The contoso.com domain contains the servers as shown in the following table:
Contoso sales staff travel within the United States and connect to a VPN by using mobile devices to access the corporate network. Sales users authenticate to the
VPN by using their Active Directory usernames and passwords. The VPN solution also supports certification-based authentication.
Contoso uses an inventory system that requires manually counting products and entering that count into a database. Contoso purchases new inventory software
that supports wireless handheld scanners and several wireless handheld scanners. The wireless handheld scanners run a third party operating system that supports
the Network Device Enrollment Service (NDES).
Business Requirements
Security
The wireless handheld scanners must use certification-based authentication to access the wireless network.
Sales users who use mobile devices must use certification-based authentication to access the VPN. When sales users leave the company, Contoso administrators
must be able to disable their VPN access by revoking their certificates.
Monitoring
All servers must be monitored by using System Center 2012 Operating Manager. In addition to monitoring the Windows operating system, you must collect security
logs from the CA servers by using ACS, and monitor the services that run on the CA and Certificate Revocation List (CRL) servers, such as certification authority
and web services.
Technical Requirements
CA Hierarchy
Contoso requires a two-tier CA hierarchy. The CA hierarchy must include a stand-alone offline root and two Active Directory-integrated issuing CAs: one for issuing
certificates to domain-joined devices, and one for issuing certificates to non-domain-joined devices by using the NDES. CRLs must be published to two web servers:
one in Detroit and one in Chicago.
Contoso has servers that run Windows Server 2012 R2 to use for the CA hierarchy. The servers are described in the following table:
The IT security department must have the necessary permissions to manage the CA and CRL servers. A domain group named Corp-IT Security must be used for
this purpose.
The IT security department users are not domain admins.
Fault Tolerance
The servers that host the CRL must be part of a Windows Network Load Balancing (NLB) cluster. The CRL must be available to users in all locations by using the
hostname crl.contoso.com, even if one of the underlying web servers is offline.
###EndCaseStudy###
You need to automatically restart the appropriate web service on DETCRL01 and CHICRL01 if the web service is stopped.
Solution: You create a recovery task in SCOM and configure it to start the World Wide Web publishing service.
Does this meet the goal?
You need to prepare the environment for APP1 Which two …
###BeginCaseStudy###
Case Study 6: Contoso Ltd Case C
Contoso, Ltd., is a manufacturing company. The company has offices in Chicago and Seattle. Each office contains two data centers. All of the data centers and
sites for the company have network connectivity to each other. The company uses a single Active Directory Domain Services (AD DS) domain.
Contoso is growing rapidly and needs to expand its computer infrastructure.
Current Environment Chicago Office
The Chicago office contains a primary data center and a backup data center. A Hyper-V cluster named Cluster1.contoso.com resides in the primary data center.
The cluster has a multiple network path configured. The cluster includes two unused SQL Server virtual machines (VMs) named SQL-SERVER1 and SQLSERVER2. The cluster also includes a Hyper-V Host group named Chi-Primary.
Clusterl.contoso.com contains the following servers:
– CHI1-HVNODE1.contoso.com
– CHI1-HVNODE2.contoso.com
– CHI1-HVNODE3.contoso.com
– CHI1-HVNODE4.contoso.com
The backup data center for the Chicago office is located on a Hyper-V cluster named Cluster2.contoso.com. The cluster has a single network path configured.
The cluster includes a Hyper-V Host group named Chi-Backup.
Cluster2.contoso.com contains the following servers:
– CHI2-HVNODEl.contoso.com
– CHI2-HVNODE2.contoso.com
– CHI2-HVNODE3.contoso.com
– CHI2-HVNODE4.contoso.com
In addition, the Chicago office contains two standalone Hyper-V servers named CHI- HVSERVER1.contoso.com and CHI-HVSERVER2.contoso.com.
There are also four newly built servers:
– CHI-SERVERl.contoso.com
– CHI-SERVER2.contoso.com
– CHI-SERVER3.contoso.com
– CHI-SERVER4.contoso.com
All the servers in the Chicago office run Windows Server 2012. Any future servers that are deployed in the Chicago office must also run Windows Server 2012.
All servers in the Chicago office use the subnet 10.20.xx.
Current Environment Seattle Office
The Seattle office contains a primary data center and a backup data center. The primary data center is located on a Hyper-V cluster named
Cluster3.contoso.com. The cluster has a multiple network path configured. The cluster includes two unused SQL Server virtual machines named SQL-SERVER3
and SQL-SERVERS The cluster includes a Hyper-V Host group named Sea-Primary.
Cluster3.contoso.com contains the following servers:
– SEA3-HVNODEl.contoso.com
– SEA3-HVNODE2.contoso.com
– SEA3-HVNODE3.contoso.com
– SEA3-HVNODE4.contoso.com
The backup data center for the Seattle office is located on a Hyper-V cluster named Cluster4.contoso.com. The cluster has a single network path configured.
The cluster includes a Hyper-V Host group named Sea-Backup.
Cluster4.contoso.com contains the following servers:
– SEA4-HVNODEl.contoso.com
– SEA4-HVNODE2.contoso.com
– SEA4-HVNODE3.contoso.com
– SEA4-HVNODE4.contoso.com
In addition, the Seattle office contains two standalone Hyper-V servers named SEA-HVSERVERl.contoso.com and SEA-HVSERVER2.contoso.com.
There are also four newly built servers:
– SEA-SERVERl.contoso.com
– SEA-SERVER2.contoso.com
– SEA-SERVER3.contoso.com
– SEA-SERVER4.contoso.com
All servers in the Seattle office run Windows Server 2012 R2. Any future servers that are deployed in the Seattle office must also run Windows Server 2012 R2.
All servers in the Seattle office use the subnet 10.10.x.x.
Business Requirements
Apps
Contoso plans to deploy new applications to make its departments more efficient.
App1
Contoso must create a new application named App1 for the human resources (HR) department. The infrastructure for App1 must reside in a virtual environment
and the data files for App1 must reside on a single shared disk.
In addition, the infrastructure for App1 must meet the following requirements:
– maximize data protection
– withstand the loss of a single guest virtual machine
– withstand the loss of a single physical server
To support App1, Contoso must deploy a new cluster named Applcluster.contoso.com.
The cluster has the following requirements:
– It must span multiple sites.
– It must support dynamic quorums.
– It must prevent failures caused by a 50% split.
App2
Contoso must create a new application named App2. To support App2, Contoso must deploy a new SQL Server cluster. The cluster must not be part of the
domain.
The server deployment team that will install the cluster has limited permissions. The server deployment team does not have the ability to create objects in Active
Directory.
Virtualization and Storage
New VMs
Any new VMs that are deployed to the Hyper-V cluster in Cluster3.contoso.com have the following requirements:
– New SQL Server VMs must be deployed only to odd-numbered servers in the cluster.
– All other new VM guests must be deployed to any available server in the cluster.
New VDE
The company needs a highly available file share cluster for a new Virtual Desktop Environment (VDE). It has the following requirements:
– The file share cluster must withstand the loss of a single server.
– The file share cluster must withstand the loss of a single network path.
– The file share cluster must use the least amount of disk space.
New virtualized SQL Server cluster
Contoso must create a new application for manufacturing. The company needs a new virtualized SQL Server cluster named VM-SQLclusterl.contoso.com.
It has the following requirements:
– The cluster must use a shared virtual hard disk.
– The cluster must have two nodes named VM-SQL-NODE1.contoso.com and VM-SQL-NODE2.contoso.com.
Highly available storage solution
The company is deploying new hardware that will replace the existing Hyper-V clusters.
The new file share cluster must have a highly available storage solution for a Hyper-V environment.
It has the following requirements:
– The new file share cluster must support guest VM clusters.
– The storage cannot reside on any of the physical Hyper-V hosts.
###EndCaseStudy###
You need to prepare the environment for APP1
Which two actions should you perform?
Each correct answer presents a part of the solution.
You need to deploy the new SQL Server virtual machines
###BeginCaseStudy###
Case Study 6: Contoso Ltd Case C
Contoso, Ltd., is a manufacturing company. The company has offices in Chicago and Seattle. Each office contains two data centers. All of the data centers and
sites for the company have network connectivity to each other. The company uses a single Active Directory Domain Services (AD DS) domain.
Contoso is growing rapidly and needs to expand its computer infrastructure.
Current Environment Chicago Office
The Chicago office contains a primary data center and a backup data center. A Hyper-V cluster named Cluster1.contoso.com resides in the primary data center.
The cluster has a multiple network path configured. The cluster includes two unused SQL Server virtual machines (VMs) named SQL-SERVER1 and SQLSERVER2. The cluster also includes a Hyper-V Host group named Chi-Primary.
Clusterl.contoso.com contains the following servers:
– CHI1-HVNODE1.contoso.com
– CHI1-HVNODE2.contoso.com
– CHI1-HVNODE3.contoso.com
– CHI1-HVNODE4.contoso.com
The backup data center for the Chicago office is located on a Hyper-V cluster named Cluster2.contoso.com. The cluster has a single network path configured.
The cluster includes a Hyper-V Host group named Chi-Backup.
Cluster2.contoso.com contains the following servers:
– CHI2-HVNODEl.contoso.com
– CHI2-HVNODE2.contoso.com
– CHI2-HVNODE3.contoso.com
– CHI2-HVNODE4.contoso.com
In addition, the Chicago office contains two standalone Hyper-V servers named CHI- HVSERVER1.contoso.com and CHI-HVSERVER2.contoso.com.
There are also four newly built servers:
– CHI-SERVERl.contoso.com
– CHI-SERVER2.contoso.com
– CHI-SERVER3.contoso.com
– CHI-SERVER4.contoso.com
All the servers in the Chicago office run Windows Server 2012. Any future servers that are deployed in the Chicago office must also run Windows Server 2012.
All servers in the Chicago office use the subnet 10.20.xx.
Current Environment Seattle Office
The Seattle office contains a primary data center and a backup data center. The primary data center is located on a Hyper-V cluster named
Cluster3.contoso.com. The cluster has a multiple network path configured. The cluster includes two unused SQL Server virtual machines named SQL-SERVER3
and SQL-SERVERS The cluster includes a Hyper-V Host group named Sea-Primary.
Cluster3.contoso.com contains the following servers:
– SEA3-HVNODEl.contoso.com
– SEA3-HVNODE2.contoso.com
– SEA3-HVNODE3.contoso.com
– SEA3-HVNODE4.contoso.com
The backup data center for the Seattle office is located on a Hyper-V cluster named Cluster4.contoso.com. The cluster has a single network path configured.
The cluster includes a Hyper-V Host group named Sea-Backup.
Cluster4.contoso.com contains the following servers:
– SEA4-HVNODEl.contoso.com
– SEA4-HVNODE2.contoso.com
– SEA4-HVNODE3.contoso.com
– SEA4-HVNODE4.contoso.com
In addition, the Seattle office contains two standalone Hyper-V servers named SEA-HVSERVERl.contoso.com and SEA-HVSERVER2.contoso.com.
There are also four newly built servers:
– SEA-SERVERl.contoso.com
– SEA-SERVER2.contoso.com
– SEA-SERVER3.contoso.com
– SEA-SERVER4.contoso.com
All servers in the Seattle office run Windows Server 2012 R2. Any future servers that are deployed in the Seattle office must also run Windows Server 2012 R2.
All servers in the Seattle office use the subnet 10.10.x.x.
Business Requirements
Apps
Contoso plans to deploy new applications to make its departments more efficient.
App1
Contoso must create a new application named App1 for the human resources (HR) department. The infrastructure for App1 must reside in a virtual environment
and the data files for App1 must reside on a single shared disk.
In addition, the infrastructure for App1 must meet the following requirements:
– maximize data protection
– withstand the loss of a single guest virtual machine
– withstand the loss of a single physical server
To support App1, Contoso must deploy a new cluster named Applcluster.contoso.com.
The cluster has the following requirements:
– It must span multiple sites.
– It must support dynamic quorums.
– It must prevent failures caused by a 50% split.
App2
Contoso must create a new application named App2. To support App2, Contoso must deploy a new SQL Server cluster. The cluster must not be part of the
domain.
The server deployment team that will install the cluster has limited permissions. The server deployment team does not have the ability to create objects in Active
Directory.
Virtualization and Storage
New VMs
Any new VMs that are deployed to the Hyper-V cluster in Cluster3.contoso.com have the following requirements:
– New SQL Server VMs must be deployed only to odd-numbered servers in the cluster.
– All other new VM guests must be deployed to any available server in the cluster.
New VDE
The company needs a highly available file share cluster for a new Virtual Desktop Environment (VDE). It has the following requirements:
– The file share cluster must withstand the loss of a single server.
– The file share cluster must withstand the loss of a single network path.
– The file share cluster must use the least amount of disk space.
New virtualized SQL Server cluster
Contoso must create a new application for manufacturing. The company needs a new virtualized SQL Server cluster named VM-SQLclusterl.contoso.com.
It has the following requirements:
– The cluster must use a shared virtual hard disk.
– The cluster must have two nodes named VM-SQL-NODE1.contoso.com and VM-SQL-NODE2.contoso.com.
Highly available storage solution
The company is deploying new hardware that will replace the existing Hyper-V clusters.
The new file share cluster must have a highly available storage solution for a Hyper-V environment.
It has the following requirements:
– The new file share cluster must support guest VM clusters.
– The storage cannot reside on any of the physical Hyper-V hosts.
###EndCaseStudy###
You need to deploy the new SQL Server virtual machines.
What should you do?
You need to configure migration for HV-CLUSTER1
###BeginCaseStudy###
Case Study 6: Contoso Ltd Case C
Contoso, Ltd., is a manufacturing company. The company has offices in Chicago and Seattle. Each office contains two data centers. All of the data centers and
sites for the company have network connectivity to each other. The company uses a single Active Directory Domain Services (AD DS) domain.
Contoso is growing rapidly and needs to expand its computer infrastructure.
Current Environment Chicago Office
The Chicago office contains a primary data center and a backup data center. A Hyper-V cluster named Cluster1.contoso.com resides in the primary data center.
The cluster has a multiple network path configured. The cluster includes two unused SQL Server virtual machines (VMs) named SQL-SERVER1 and SQLSERVER2. The cluster also includes a Hyper-V Host group named Chi-Primary.
Clusterl.contoso.com contains the following servers:
– CHI1-HVNODE1.contoso.com
– CHI1-HVNODE2.contoso.com
– CHI1-HVNODE3.contoso.com
– CHI1-HVNODE4.contoso.com
The backup data center for the Chicago office is located on a Hyper-V cluster named Cluster2.contoso.com. The cluster has a single network path configured.
The cluster includes a Hyper-V Host group named Chi-Backup.
Cluster2.contoso.com contains the following servers:
– CHI2-HVNODEl.contoso.com
– CHI2-HVNODE2.contoso.com
– CHI2-HVNODE3.contoso.com
– CHI2-HVNODE4.contoso.com
In addition, the Chicago office contains two standalone Hyper-V servers named CHI- HVSERVER1.contoso.com and CHI-HVSERVER2.contoso.com.
There are also four newly built servers:
– CHI-SERVERl.contoso.com
– CHI-SERVER2.contoso.com
– CHI-SERVER3.contoso.com
– CHI-SERVER4.contoso.com
All the servers in the Chicago office run Windows Server 2012. Any future servers that are deployed in the Chicago office must also run Windows Server 2012.
All servers in the Chicago office use the subnet 10.20.xx.
Current Environment Seattle Office
The Seattle office contains a primary data center and a backup data center. The primary data center is located on a Hyper-V cluster named
Cluster3.contoso.com. The cluster has a multiple network path configured. The cluster includes two unused SQL Server virtual machines named SQL-SERVER3
and SQL-SERVERS The cluster includes a Hyper-V Host group named Sea-Primary.
Cluster3.contoso.com contains the following servers:
– SEA3-HVNODEl.contoso.com
– SEA3-HVNODE2.contoso.com
– SEA3-HVNODE3.contoso.com
– SEA3-HVNODE4.contoso.com
The backup data center for the Seattle office is located on a Hyper-V cluster named Cluster4.contoso.com. The cluster has a single network path configured.
The cluster includes a Hyper-V Host group named Sea-Backup.
Cluster4.contoso.com contains the following servers:
– SEA4-HVNODEl.contoso.com
– SEA4-HVNODE2.contoso.com
– SEA4-HVNODE3.contoso.com
– SEA4-HVNODE4.contoso.com
In addition, the Seattle office contains two standalone Hyper-V servers named SEA-HVSERVERl.contoso.com and SEA-HVSERVER2.contoso.com.
There are also four newly built servers:
– SEA-SERVERl.contoso.com
– SEA-SERVER2.contoso.com
– SEA-SERVER3.contoso.com
– SEA-SERVER4.contoso.com
All servers in the Seattle office run Windows Server 2012 R2. Any future servers that are deployed in the Seattle office must also run Windows Server 2012 R2.
All servers in the Seattle office use the subnet 10.10.x.x.
Business Requirements
Apps
Contoso plans to deploy new applications to make its departments more efficient.
App1
Contoso must create a new application named App1 for the human resources (HR) department. The infrastructure for App1 must reside in a virtual environment
and the data files for App1 must reside on a single shared disk.
In addition, the infrastructure for App1 must meet the following requirements:
– maximize data protection
– withstand the loss of a single guest virtual machine
– withstand the loss of a single physical server
To support App1, Contoso must deploy a new cluster named Applcluster.contoso.com.
The cluster has the following requirements:
– It must span multiple sites.
– It must support dynamic quorums.
– It must prevent failures caused by a 50% split.
App2
Contoso must create a new application named App2. To support App2, Contoso must deploy a new SQL Server cluster. The cluster must not be part of the
domain.
The server deployment team that will install the cluster has limited permissions. The server deployment team does not have the ability to create objects in Active
Directory.
Virtualization and Storage
New VMs
Any new VMs that are deployed to the Hyper-V cluster in Cluster3.contoso.com have the following requirements:
– New SQL Server VMs must be deployed only to odd-numbered servers in the cluster.
– All other new VM guests must be deployed to any available server in the cluster.
New VDE
The company needs a highly available file share cluster for a new Virtual Desktop Environment (VDE). It has the following requirements:
– The file share cluster must withstand the loss of a single server.
– The file share cluster must withstand the loss of a single network path.
– The file share cluster must use the least amount of disk space.
New virtualized SQL Server cluster
Contoso must create a new application for manufacturing. The company needs a new virtualized SQL Server cluster named VM-SQLclusterl.contoso.com.
It has the following requirements:
– The cluster must use a shared virtual hard disk.
– The cluster must have two nodes named VM-SQL-NODE1.contoso.com and VM-SQL-NODE2.contoso.com.
Highly available storage solution
The company is deploying new hardware that will replace the existing Hyper-V clusters.
The new file share cluster must have a highly available storage solution for a Hyper-V environment.
It has the following requirements:
– The new file share cluster must support guest VM clusters.
– The storage cannot reside on any of the physical Hyper-V hosts.
###EndCaseStudy###
You need to configure migration for HV-CLUSTER1. What should you do?