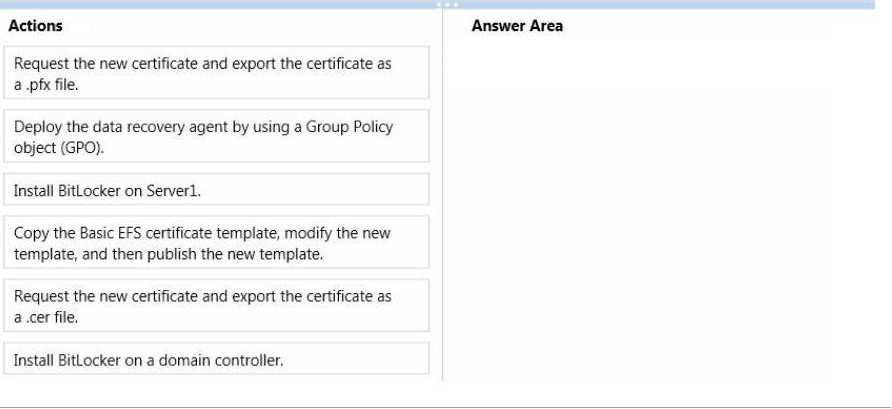
Which four actions should you perform in sequence?
Your network contains an Active Directory domain named contoso.com.
The domain contains two domain controllers named DC1 and DC2.
The domain contains a server named Server1.
Server1 is a certification authority (CA).
All servers run Windows Server 2012 R2.
You plan to deploy BitLocker Drive Encryption (BitLocker) to all client computers.
The unique identifier for your organization is set to Contoso.
You need to ensure that you can recover the BitLocker encrypted data by using a BitLocker data recovery agent.
You must be able to perform the recovery from any administrative computer.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the
correct order.
Select and Place:
Which three actions should you recommend?
Your network contains an Active Directory domain named contoso.com.
The network has an Active Directory Certificate Services (AD CS) infrastructure.
You publish the certificate revocation list (CRL) to a farm of Web servers.
You are creating a disaster recovery plan for the AD CS infrastructure.
You need to recommend which actions must be performed to restore certificate revocation checking if a certification authority (CA) is offline for an
extended period of time.
Which three actions should you recommend? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the
correct order.
Select and Place:
Which network types should you identify?
Your network contains an Active Directory domain named contoso.com.
The domain contains multiple servers that are configured as Hyper-V hosts.
You plan to implement four virtual machines.
The virtual machines will be configured as shown in the following table.
You need to identify which network must be added to each virtual machine.
Which network types should you identify? To answer, drag the appropriate Network Type to the correct virtual machine in the answer area. Each Network Type may
be used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
Select and Place:
Which three actions should you perform?
Your network contains an Active Directory domain named contoso.com.
The domain contains four servers named Server1, Server2, Server3, and Server4 that run Windows Server 2012.
Server1 and Server2 are configured as file servers and are part of a failover cluster named Cluster1.
Server3 and Server4 have Microsoft SQL Server 2012 installed and are part of a failover cluster named Cluster2.
You add a disk named Disk1 to the nodes in Cluster1.
Disk1 will be used to store the data files and log files used by SQL Server 2012.
You need to configure the environment so that access to Disk1 remains available when a node on Cluster1 fails over or fails back.
Which three actions should you perform? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct
order.
Select and Place:
You need to configure the environment
Drag and Drop Question
You use the entire System Center suite.
You integrate Service Manager with Operations Manager. Virtual Machine Manager, Orchestrator, and Active Directory.
You perform all remediation by using Orchestrator runbooks. An application experiences performance problems on a periodic basis.
You have the following requirements:
A new incident must be opened when System Center Operations Manager (SCOM) detects a performance problem.
The incident must be closed when the performance problem is resolved.
The incident must be associated with the HR performance problem in Service Manager.
You need to configure the environment.
Select and Place:
Which five actions should you perform?
Your network contains servers that run Windows Server 2012.
The network contains two servers named Server1 and Server2 that are connected to a SAS storage device.
The device only supports two connected computers.
Server1 has the iSCSI Target Server role service installed.
Ten application servers use their iSCSI Initiator to connect to virtual disks in the SAS storage device via iSCSI targets on Server1.
Currently, Server2 is used only to run backup software.
You install the iSCSI Target Server role service on Server2.
You need to ensure that the iSCSItargets are available if Server1 fails.
Which five actions should you perform? To answer, move the five appropriate actions from the list of actions to the answer area and arrange them in the correct
order.
Select and Place:
Which three actions should you recommend?
You have a failover cluster named Cluster1 that contains four Hyper-V hosts.
Cluster1 hosts 20 virtual machines.
You deploy a new failover cluster named Cluster2.
You plan to replicate the virtual machines from Cluster1 to Cluster2.
You need to recommend which actions must be performed on Cluster2 for the planned deployment.
Which three actions should you recommend? To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the
correct order.
Select and Place:
Which three actions should you perform?
Your network contains two servers named Server1 and Server2 that run Windows Server 2012.
Server1 and Server2 have the Hyper-V server role installed and are members of a failover cluster.
The network contains a Storage Area Network (SAN) that has a LUN named LUN1.
LUN1 is connected to a 12-TB disk on the SAN.
You plan to host three new virtual machines on the failover cluster. Each virtual machine will store up to 4 TB of data on a single disk.
The virtual machines will be backed up from the hosts by using the Volume Shadow Copy Service (VSS).
You need to ensure that Server1 and Server2 can store the new virtual machines on the SAN.
Which three actions should you perform?
To answer, move the three appropriate actions from the list of actions to the answer area and arrange them in the correct order
Select and Place:
How many disks should you identify?
Your network contains multiple servers that run Windows Server 2012.
You plan to implement three virtual disks.
The virtual disks will be configured as shown in the following table.
You need to identify the minimum number of physical disks required for each virtual disk.
How many disks should you identify? To answer, drag the appropriate number of disks to the correct virtual disk in the answer area. Each number of disks may be
used once, more than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
Select and Place:
Which user roles should you identify?
You plan to delegate the management of virtual machines to five groups by using Microsoft System Center 2012 Virtual Machine Manager (VMM).
The network contains 20 Hyper-V hosts in a host group named HostGroup1.
You identify the requirements for each group as shown in the following table.
You need to identify which user role must be assigned to each group.
Which user roles should you identify? To answer, drag the appropriate user role to the correct group in the answer area. Each user role may be used once, more
than once, or not at all. Additionally, you may need to drag the split bar between panes or scroll to view content.
Select and Place: