What are two possible ways to achieve this goal? (Each correct answer presents a complete solution
You are the network administrator for your company. The network consists of a single Active Directory domain. All servers run Windows Server 2003. All client computers run either Windows XP Professional or Windows 2000 Professional. All client computer accounts are located in an organizational unit (OU) named Workstation. A written company policy states that the Windows 2000 Professional computers must not use offline folders. You create a Group Policy object (GPO) to enforce this requirement. The settings in the GPO exist for both Windows 2000 Professional computers and Windows XP Professional computers. You need to configure the GPO to apply only to Windows 2000 Professional computers. What are two possible ways to achieve this goal? (Each correct answer presents a complete solution. Choose two.)
You need to configure the Application group to remain on Server2 while you research the problem on Server1
You are a network administrator for your company. You install Windows Server 2003 on two servers named Server1 and Server2. You configure Server1 and Server2 as a two-node cluster. You configure a custom application on the cluster by using the Generic Application resource, and you put all resources in the Application group.
You test the cluster and verify that it fails over properly and that you can move the Applications group from one node to the other and back again. The application and the cluster run successfully for several weeks.
Users then report that they cannot access the application. You investigate and discover that Server1 and Server2 are running but the Application group is in a failed state. You restart the Cluster service and attempt to bring the Application group online on Server1.
The Application group fails. You discover that Server1 fails, restarts automatically, and fails again soon after restarting. Server1 continues to fail and restart until the Application group reports that it is in a failed state and stops attempting to bring itself back online.
You need to configure the Application group to remain on Server2 while you research the problem on Server1.
What should you do?
You need to specify the list of applications that users are permitted to run
You have a single Active Directory directory service domain. All servers run Windows Server 2003. You need to specify the list of applications that users are permitted to run. You create a new Group Policy object (GPO) and link it to the domain. What should you do next?
You need to allow the user on Server2 to use the script to transfer files to Server5
You are a network administrator for Woodgrove Bank. All servers run Windows Server 2003. The company uses WINS and DNS for name resolution.
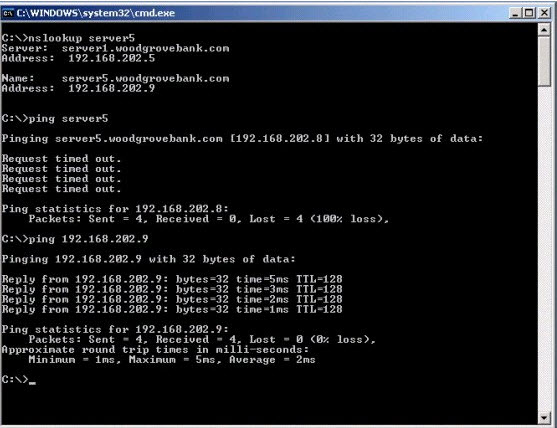
The LMHosts and Hosts files are not used. A user on a server named Server2 reports that when she runs a script to transfer files to a server named Server5, she receives the following error messag* “Unknown host Server5.”
You use Server2 to troubleshoot the problem. The results of your troubleshooting are shown in the exhibit.
You need to allow the user on Server2 to use the script to transfer files to Server5.
What should you do?
Exhibit:
Which two actions should you perform? (Each correct answer presents part of the solution
You have two Active Directory directory service forests named contoso.com and fabrikam.com. All users log on to the contoso.com domain. All servers run Windows Server 2003 and are members of the fabrikam.com domain. You create a one-way forest trust in which fabrikam.com is trusting contoso.com. Forest-wide authentication is enabled. You need to provide only selected users with access to a server in the fabrikam.com domain. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
What should you do?
You are the network administrator for your company. The network consists of a single Active Directory domain. All computers on the network are members of the domain. You administer a three-node Network Load Balancing cluster. Each cluster node runs Windows Server 2003 and has a single network adapter.
The cluster has converged successfully. You notice that the nodes in the cluster run at almost full capacity most of the time. You want to add a fourth node to the cluster. You enable and configure Network Load Balancing on the fourth node. However, the cluster does not converge to a four-node cluster. In the System log on the existing three nodes, you find the exact same TCP/IP error event.
The event has the following description: “The system detected an address conflict for IP address 10.50.8.70 with the system having network hardware address 02:BF:0*32:08:46.” In the System log on the new fourth node, you find a similar TCP/error event with the following description: “The system detected an address conflict for IP address 10.50.8.70 with the system having network hardware address 03:BF:0*32:08:46.” Only the hardware address is different in the two descriptions. You verify that IP address 10.50.8.70 is configured as the cluster IP address on all four nodes.
You want to configure a four-node Network Load Balancing cluster.
What should you do?
You need to allow the Server Access Team group to grant permissions for the application servers without granti
You are the network administrator for your company. Your network consists of a single Active Directory domain. The functional level of the domain is Windows Server 2003. You add eight servers for a new application. You create an organizational unit (OU) named Application to hold the servers and other resources for the application. Users and groups in the domain will need varied permissions on the application servers. The members of a global group named Server Access Team need to be able to grant access to the servers. The Server Access Team group does not need to be able to perform any other tasks on the servers. You need to allow the Server Access Team group to grant permissions for the application servers without granting the Server Access Team group unnecessary permissions. What should you do?
You need to choose the appropriate predefined security template to apply to the domain controllers
You are the network administrator for your company. The network consists of a single Active Directory domain. All domain controllers run Windows Server 2003. All client computers run Windows XP Professional. The company has legacy applications that run on UNIX servers.
The legacy applications use the LDAP protocol to query Active Directory for employee information. The domain controllers are currently configured with the default security settings. You need to configure enhanced security for the domain controllers. In particular, you want to configure stronger password settings, audit settings, and lockout settings.
You want to minimize interference with the proper functioning of the legacy applications. You decide to use the predefined security templates.
You need to choose the appropriate predefined security template to apply to the domain controllers.
What should you do?
What are two possible ways to achieve this goal? (Each correct answer presents a complete solution
You are the network administrator for your company. The network consists of a single Active Directory domain with three sites named Site1, Site2, and Site3. The sites and site links are configured to use Site2 to connect Site1 and Site3. Each site contains three Windows Server 2003 domain controllers. A domain controller in each site is configured as a preferred bridgehead server. All user and group accounts are created in Site1. Several new users start work in Site2. When they attempt to log on to the network, the logon fails. You confirm that the user accounts are created and are visible in Site1 and Site2. You discover that the preferred IP bridgehead server in Site2 failed. You repair the server and confirm that replication is successful to Site2. You need to ensure that the failure of a single domain controller in any site will not interfere with Active Directory replication between sites. What are two possible ways to achieve this goal? (Each correct answer presents a complete solution. Choose two.)
Which two actions should you take? (Each correct answer presents part of the solution
You are a network administrator for your company. The network consists of multiple physical segments. The network contains two Windows Server 2003 computers named Server1 and Server2, and several Windows 2000 Server computers. Server1 is configured with a single DHCP scope for the 10.250.100.0/24 network with an IP address range of 10.250.100.10 to 10.250.100.100. Several users on the network report that they cannot connect to file and print servers, but they can connect to each other’s client computers. All other users on the network are able to connect to all network resources. You run the ipconfig.exe /all command on one of the affected client computers and observe the information in the following table.
You need to configure all affected client computers so that they can communicate with all other hosts on the network.
Which two actions should you take? (Each correct answer presents part of the solution. Choose two.)