Which server or servers should you identify? (Choose all that apply
An administrator named Admin1 plans to deploy the planned VMs.
You need to identify which servers can be converted to VMs by using physical-to-virtual machine (P2V) conversion.
Which server or servers should you identify? (Choose all that apply.)
You need to ensure that BitLocker Drive Encryption is disabled on deployed computers
You have a single-domain Active Directory Domain Services (AD DS) forest. All servers run Windows Server 2008 R2. You use Microsoft Deployment Toolkit (MDT) 2010 and System Center Configuration Manager 2007 R2 to deploy Windows 7 using Zero Touch Installation (ZTI). You have a Windows 7 reference computer that is encrypted using BitLocker Drive Encryption.
You need to ensure that BitLocker Drive Encryption is disabled on deployed computers.
What should you do?
You need to configure each guest VM to meet the requirements
All client computers in your company run Windows 7 Enterprise. Users run Windows XP Mode guest virtual machines (VMs) on their computers. Each client computer runs two guest VMs. Each guest VM requires network connectivity to the other guest VM on the host computer, but must not have network connectivity to the host computer operating system or to the Internet. You need to configure each guest VM to meet the requirements. What should you do?
Then what action should you perform to achieve the goal?
You work as the network administrator at ESL, Ltd. You manage a server run Windows Server 2008 and you have installed the Hyper-V server role on the server. And you create a new virtual machine that has the following configurations:
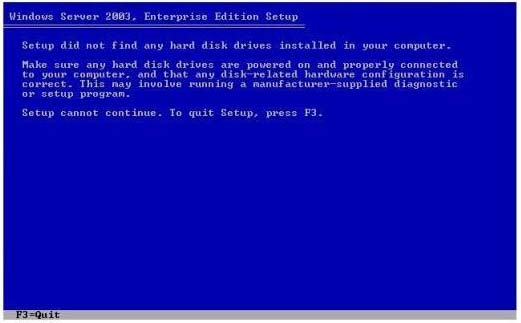
Base on the provided conditions, you try to install Windows Server 2003 on the virtual machine and receive the error message shown in the exhibit.
Now, you must ensure that you can install Windows Server 2003 on the virtual machine. Then what action should you perform to achieve the goal?
What should you include in the recommendation?
You are evaluating the use of pass-through disks for the Exchange servers.
You need to recommend a backup solution for the Exchange servers that meets the following requirements:
– Minimizes costs.
– Provides for the recovery of the Exchange databases if a hardware failure occurs.
What should you include in the recommendation?
Which protocol should you allow?
You are preparing for a Zero Touch Installation (ZTI) of Windows 7 using Windows Deployment Services (WDS) and System Center Configuration Manager 2007 R2. Your network includes branch offices that are separated by firewalls.
You need to ensure that the necessary protocol is allowed through the firewalls to support the deployment.
Which protocol should you allow?
Which should you use?
Your organization has an Active Directory Domain Services (AD DS) domain. All client computers run Windows 7. You need to create a single distribution file containing Windows Virtual PC and a virtual machine image that will be deployed to all client computers. Which should you use?
vhd as their parent disk have App 1 installed
You work as the network administrator at ESL, Ltd. You manage a virtual machine named VM1. VM1 runs Windows Server 2008 and has one dynamically expending virtual disk named VM1. vhd. Currently, you create a snapshot of VM1 named Snap 1 and install an application on Vm1 named App 1. Base on the above conditions, you are required to ensure that all newly-created virtual machines that use VM1. vhd as their parent disk have App 1 installed.
Which protocol should you recommend?
An administrator named Admin1 plans to implement the planned App-V deployment. You need to recommend which protocol to use for the App-V deployment.
Which protocol should you recommend?
You need to ensure that this client computer is successfully deployed with the modified task sequence
You are using Windows Deployment Services (WDS) and System Center Configuration Manager 2007 R2 to perform a Zero Touch Installation (ZTI) of Windows 7 on your company’s client computers. A user shuts down his computer during the deployment process. Before the computer boots, the task sequence is modified.
You need to ensure that this client computer is successfully deployed with the modified task sequence.
What should you do first?