You need to identify whether the GPO has been applied
Your company has an Active Directory forest that contains eight linked Group Policy Objects (GPOs). One of these GPOs publishes applications to user objects. A user reports that the application is not available for installation. You need to identify whether the GPO has been applied. What should you do?
You need to configure the client computers in the North America office to improve the name resolution response
Your company has a single Active Directory forest that has a domain in North America named na.contoso.com and a domain in South America named sa.contoso.com. The client computers run Windows 7.
You need to configure the client computers in the North America office to improve the name resolution response time for resources in the South America office.
What should you do?
You need to prepare the target computers for the application
Your company purchases a new application to deploy on 200 computers. The application requires that you modify the registry on each target computer before you install the application. The registry modifications are in a file that has an .adm extension. You need to prepare the target computers for the application. What should you do?
You need to edit the ad
Your company has an Active Directory domain named ad.contoso.com. All client computers run Windows 7.
The company has recently acquired a company that has an Active Directory domain named ad.fabrikam.com. A two-way forest trust is established between the ad.fabrikam.com domain and the ad.contoso.com domain.
You need to edit the ad.contoso.com domain Group Policy object (GPO) to enable users in the ad.contoso.com domain to access resources in the ad.fabrikam.com domain.
What should you do?
You need to reduce the time required to authenticate users from the labs
Your company, Contoso Ltd, has offices in North America and Europe. Contoso has an Active Directory forest that has three domains. You need to reduce the time required to authenticate users from the labs.eu.contoso.com domain when they access resources in the eng.na.contoso.com domain. What should you do?
Which event delivery optimization option should you enable?
You have a perimeter network that contains 20 servers. All of the servers run Windows Server 2008 R2 and are members of a workgroup. You add an additional server named Server21 to the perimeter network. You plan to configure Server21 to collect events forwarded from the other servers. You need to ensure that the events are available on Server21 as quickly as possible. Which event delivery optimization option should you enable?
You need to ensure users in the fabrikam
Your company has two Active Directory forests named contoso.com and fabrikam.com.
The company network has three DNS servers named DNS1, DNS2, and DNS3. The DNS servers are configured as shown in the following table.
All computers that belong to the fabrikam.com domain have DNS3 configured as the preferred DNS server. All other computers use DNS1 as the preferred DNS server.
Users from the fabrikam.com domain are unable to connect to the servers that belong to the contoso.com domain.
You need to ensure users in the fabrikam.com domain are able to resolve all contoso.com queries.
What should you do?
You need to ensure that updates for the new application are available to all of the client computers
Your network contains a Windows Server Update Services (WSUS) server named Server1. All client computers are configured to download updates from Server1. Server1 is configured only to synchronize manually to Microsoft Update. Your company deploys a new Microsoft application. You discover that the new application is not listed on the Products and Classifications list. You need to ensure that updates for the new application are available to all of the client computers.
What should you do first?
Which three actions should you perform to configure IPSec? (Each correct answer presents part of the solution
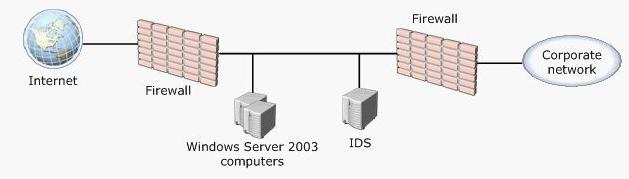
You are a security administrator for your company. The network consists of a perimeter network that is configured as shown in the exhibit. (Refer to the Exhibit.)
All computers in the perimeter network run Windows Server 2003. The company’s written security policy states the following: All computers must pass a security inspection before they are placed in the perimeter network. Only computers that pass inspection are permitted to communicate with firewalls or other computers that pass inspection. All communication in the perimeter network is inspected by a networ based intrusion-detection system (IDS). Communication between computers in the perimeter network must use the strongest possible authentication methods.You decide to deploy IPSec in the perimeter network to enforce the written security policy. You enable IPSec on the firewall computers.
You need to plan IPSec configuration for the Windows Server 2003 computers so that it meets the written security policy. Which three actions should you perform to configure IPSec? (Each correct answer presents part of the solution. Choose three.)
You need to create a single group named Help Desk that contains all help desk department user accounts …
You are a security administrator for your company. The network consists of an Active Directory forest that contains two domains. The domains are named treyresearch.com and litwareinc.com. All Active Directory domains are running at a Windows Server 2000 mixed mode functionality level.
Employees in the help desk department need to modify certain attributes of employee user accounts that reside in the treyresearch.com domain. The help desk department user accounts reside in the litwareinc.com domain.
You need to create a single group named Help Desk that contains all help desk department user accounts and that can be granted access to modify the employee user accounts in the treyresearch.com domain. What should you do?