Which of the following must you do to accomplish this?
Your manager has asked you to create various user objects using Windows PowerShell.
Which of the following must you do to accomplish this?
What should you include in the recommendation?
Testlet: Lucerne Publishing
You need to recommend a solution to ensure that allof the client computers that run Windows 7 meet the
company’s security requirements.
What should you include in the recommendation?\r\n
COMPANY OVERVIEW
Overview
Lucerne Publishing is a large publishing company that produces both traditional books and e- books.
Physical Location
The company has a main office and a branch office. The main office is located in New York. The branch
office is located in San Francisco. The main officehas a satellite office located in Boston. The company has
7,500 users.
EXISTING ENVIRONMENT
Active Directory Environment
The network contains an Active Directory forest. The forest contains a single domain named
lucernepublishing.com.
Network Infrastructure
Client computers in the New York office and the SanFrancisco office run either Windows Vista or Windows
XP. All client computers in the Boston office run Windows 7.
The company has a finance department. All of the client computers in the finance department run Windows
XP. The finance department uses an application named App1. App1 only runs on Windows XP.
The relevant servers in the New York office are configured as shown in the following table.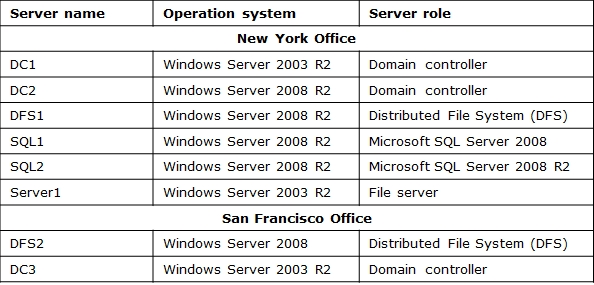
The servers have the following configurations:
Remote Desktop is enabled on all servers.
The passwords for all service accounts are set to never expire.
Server1 stores roaming user profiles for users in the Boston office.
SQL1 and SQL2 are deployed in a two-node failover cluster named Cluster1.
All servers have Pre-Boot Execution Environment (PXE)-compliant network adapters.
The servers in the San Francisco office contain neither a recovery partition nor optical media drives.
DFS1 and DFS2 are members of the same DFS Replication group. The DFS namespace is configured
to use Windows 2000 Server mode.
The Boston office has no servers. The Boston officeconnects to the New York office by using a dedicated
hardware VPN device.
The finance department publishes monthly forecast reports that are stored in DFS.
REQUIREMENTS
Business Goals
Lucerne Publishing must minimize administrative costs, hardware costs, software costs, and development
costs, whenever possible.
Planned Changes
All client computers will be upgraded to Windows 7.
A VPN server will be deployed in the main office. All VPN clients must have the latest Windows updates
before they can access the internal network.
You plan to deploy a server that has the Remote Desktop Gateway (RD Gateway) role service installed.
Technical Requirements
Lucerne Publishing must meet the following technical requirements:
Upgrade all client computers to Windows 7.
Minimize Group Policy-related replication traffic.
Ensure that App1 can be used from client computers that run Windows 7.
Ensure that users can use App1 when they are disconnected from the network.
Ensure that you can perform a bare metal recovery of the servers in the San Francisco office.
Minimize the amount of time it takes users in the Boston office to log on to their client computers.
Ensure that domain administrators can connect remotely to all computers in the domain through RD
Gateway.
Ensure that file server administrators can access DFS servers and file servers through the RD Gateway.
Prevent file server administrators from accessing other servers through the RD Gateway.
Security Requirements
Lucerne Publishing must meet the following securityrequirements:
USB storage devices must not be used on any servers.
The passwords for all user accounts must be changedevery 60 days.
Users must only be able to modify the financial forecast reports on DFS1. DFS2 must contain a read-only copy of the financial forecast reports.
All operating system drives on client computers that run Windows 7 must be encrypted.
Only approved USB storage devices must be used on client computers that run Windows 7.
Which tool should you use to correct the changes toall of the OU’s at once?
After setting up several Active Directory users fordifferent OU’s, you discover that the IT technician has miss
spelt the Office property as Londn instead of London.
Which tool should you use to correct the changes toall of the OU’s at once?
What should you include in the recommendation?
Testlet: Lucerne Publishing
You need to recommend a solution for managing the service accounts for SQL1 and SQL2. The solution must
meet the company’s security requirements.
What should you include in the recommendation?\r\n
COMPANY OVERVIEW
Overview
Lucerne Publishing is a large publishing company that produces both traditional books and e- books.
Physical Location
The company has a main office and a branch office. The main office is located in New York. The branch
office is located in San Francisco. The main officehas a satellite office located in Boston. The company has
7,500 users.
EXISTING ENVIRONMENT
Active Directory Environment
The network contains an Active Directory forest. The forest contains a single domain named
lucernepublishing.com.
Network Infrastructure
Client computers in the New York office and the SanFrancisco office run either Windows Vista or Windows
XP. All client computers in the Boston office run Windows 7.
The company has a finance department. All of the client computers in the finance department run Windows
XP. The finance department uses an application named App1. App1 only runs on Windows XP.
The relevant servers in the New York office are configured as shown in the following table.
The servers have the following configurations:
Remote Desktop is enabled on all servers.
The passwords for all service accounts are set to never expire.
Server1 stores roaming user profiles for users in the Boston office.
SQL1 and SQL2 are deployed in a two-node failover cluster named Cluster1.
All servers have Pre-Boot Execution Environment (PXE)-compliant network adapters.
The servers in the San Francisco office contain neither a recovery partition nor optical media drives.
DFS1 and DFS2 are members of the same DFS Replication group. The DFS namespace is configured
to use Windows 2000 Server mode.
The Boston office has no servers. The Boston officeconnects to the New York office by using a dedicated
hardware VPN device.
The finance department publishes monthly forecast reports that are stored in DFS.
REQUIREMENTS
Business Goals
Lucerne Publishing must minimize administrative costs, hardware costs, software costs, and development
costs, whenever possible.
Planned Changes
All client computers will be upgraded to Windows 7.
A VPN server will be deployed in the main office. All VPN clients must have the latest Windows updates
before they can access the internal network.
You plan to deploy a server that has the Remote Desktop Gateway (RD Gateway) role service installed.
Technical Requirements
Lucerne Publishing must meet the following technical requirements:
Upgrade all client computers to Windows 7.
Minimize Group Policy-related replication traffic.
Ensure that App1 can be used from client computers that run Windows 7.
Ensure that users can use App1 when they are disconnected from the network.
Ensure that you can perform a bare metal recovery of the servers in the San Francisco office.
Minimize the amount of time it takes users in the Boston office to log on to their client computers.
Ensure that domain administrators can connect remotely to all computers in the domain through RD
Gateway.
Ensure that file server administrators can access DFS servers and file servers through the RD Gateway.
Prevent file server administrators from accessing other servers through the RD Gateway.
Security Requirements
Lucerne Publishing must meet the following securityrequirements:
USB storage devices must not be used on any servers.
The passwords for all user accounts must be changedevery 60 days.
Users must only be able to modify the financial forecast reports on DFS1. DFS2 must contain a read-only copy of the financial forecast reports.
All operating system drives on client computers that run Windows 7 must be encrypted.
Only approved USB storage devices must be used on client computers that run Windows 7.
Which command can be used to delete user accounts?
Your IT company is constantly changing, with new users coming and going throughout the year.
One of your common tasks requires the deletion of user accounts for employees who have left the company.
Which command can be used to delete user accounts?
What should you include in the recommendations?
Testlet: Graphic Design Institute, Case A
You need to recommend a solution for configuring the Web servers. The solution must meet the company’s
technical requirements.
What should you include in the recommendations?\r\n
COMPANY OVERVIEW
Graphic Design Institute is a training company thathas a main office and 10 branch offices. The main office
is located in Bangalore.
PLANNED CHANGES
Graphic Design Institute plans to implement the following changes:
Deploy a new two-node failover cluster that runs the Hyper-V server role on each node. Ensure that
intra-cluster network traffic is isolated from all other network traffic.
Implement Network Access Protection (NAP) for all of the client computers on the internal network and
for all of the client computers that connect remotely.
EXISTING ENVIRONMENT
The relevant servers in the main office are configured as shown in the following table.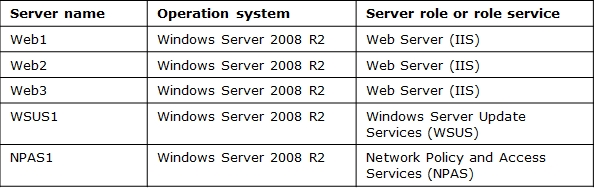
NPAS1 contains a static IP address pool.
Web1, Web2, and Web3 host a copy of the corporate Web site.
Web1, Web2, and Web3 are located in the perimeter network and belong to a workgroup.
All client computers run Windows XP Professional, Windows Vista Enterprise, or Windows 7 Enterprise, All
client computers are members of the domain.
Some users work remotely. To access the company’s internal resources, the remote users use a VPN
connection to NPAS1.
Existing Active Directors/Directory Services
The network contains a single-domain Active Directory forest named graphicdesigninstitute.com.
The Active Directory Recycle Bin is enabled.
Existing Network Infrastructure
Graphic Design Institute has an internal network and a perimeter network.
The network contains network switches and wireless access points (WAPs) from multiple vendors. Some of
the network devices are more than 10 years old and do not support port-based authentication.
TECHNICAL REQUIREMENTS
All of the accounts used for administration must beassigned the minimum amount of permissions.
Web1, Web2, and Web3 must have the identical configurations for the corporate Web site.
The Web servers must contain a local copy of all the Web pages in the Web site. When a Web page is
modified on any of the Web servers, the modifications must be copied automatically to all of the Web
servers.
A user named Admin1 must be responsible for performing the following tasks:
Restarting all of the Web servers.
Backing up and restoring the files on all of the Web servers.
A user named Admin2 must be responsible for performing the following tasks;
Backing up the Active Directory database.
Recovering deleted objects from the Active Directory Recycle Bin.
Which of the following is a possible way to unlock a User Account?
A user has locked his account (again!) and you needto unlock it so they can continue working normally.
Which of the following is a possible way to unlock a User Account? (Choose three)
You need to ensure that Web1, Web2, and Web3 download updates from WSUS1
Testlet: Graphic Design Institute, Case A
You need to ensure that Web1, Web2, and Web3 download updates from WSUS1.
What should you do?\r\n
COMPANY OVERVIEW
Graphic Design Institute is a training company thathas a main office and 10 branch offices. The main office
is located in Bangalore.
PLANNED CHANGES
Graphic Design Institute plans to implement the following changes:
Deploy a new two-node failover cluster that runs the Hyper-V server role on each node. Ensure that
intra-cluster network traffic is isolated from all other network traffic.
Implement Network Access Protection (NAP) for all of the client computers on the internal network and
for all of the client computers that connect remotely.
EXISTING ENVIRONMENT
The relevant servers in the main office are configured as shown in the following table.
NPAS1 contains a static IP address pool.
Web1, Web2, and Web3 host a copy of the corporate Web site.
Web1, Web2, and Web3 are located in the perimeter network and belong to a workgroup.
All client computers run Windows XP Professional, Windows Vista Enterprise, or Windows 7 Enterprise, All
client computers are members of the domain.
Some users work remotely. To access the company’s internal resources, the remote users use a VPN
connection to NPAS1.
Existing Active Directors/Directory Services
The network contains a single-domain Active Directory forest named graphicdesigninstitute.com.
The Active Directory Recycle Bin is enabled.
Existing Network Infrastructure
Graphic Design Institute has an internal network and a perimeter network.
The network contains network switches and wireless access points (WAPs) from multiple vendors. Some of
the network devices are more than 10 years old and do not support port-based authentication.
TECHNICAL REQUIREMENTS
All of the accounts used for administration must beassigned the minimum amount of permissions.
Web1, Web2, and Web3 must have the identical configurations for the corporate Web site.
The Web servers must contain a local copy of all the Web pages in the Web site. When a Web page is
modified on any of the Web servers, the modifications must be copied automatically to all of the Web
servers.
A user named Admin1 must be responsible for performing the following tasks:
Restarting all of the Web servers.
Backing up and restoring the files on all of the Web servers.
A user named Admin2 must be responsible for performing the following tasks;
Backing up the Active Directory database.
Recovering deleted objects from the Active Directory Recycle Bin.
What should you do to enable them to lo on to theircomputer?
A user from your organisation has reported to the IT helpdesk that they are receiving the following message :
“Your account is configured to prevent you from using the computer. Please try another computer.”
What should you do to enable them to lo on to theircomputer?
Which NAP enforcement method should you recommend?
Testlet: Graphic Design Institute, Case A
Which NAP enforcement method should you recommend?\r\n
COMPANY OVERVIEW
Graphic Design Institute is a training company thathas a main office and 10 branch offices. The main office
is located in Bangalore.
PLANNED CHANGES
Graphic Design Institute plans to implement the following changes:
Deploy a new two-node failover cluster that runs the Hyper-V server role on each node. Ensure that
intra-cluster network traffic is isolated from all other network traffic.
Implement Network Access Protection (NAP) for all of the client computers on the internal network and
for all of the client computers that connect remotely.
EXISTING ENVIRONMENT
The relevant servers in the main office are configured as shown in the following table.
NPAS1 contains a static IP address pool.
Web1, Web2, and Web3 host a copy of the corporate Web site.
Web1, Web2, and Web3 are located in the perimeter network and belong to a workgroup.
All client computers run Windows XP Professional, Windows Vista Enterprise, or Windows 7 Enterprise, All
client computers are members of the domain.
Some users work remotely. To access the company’s internal resources, the remote users use a VPN
connection to NPAS1.
Existing Active Directors/Directory Services
The network contains a single-domain Active Directory forest named graphicdesigninstitute.com.
The Active Directory Recycle Bin is enabled.
Existing Network Infrastructure
Graphic Design Institute has an internal network and a perimeter network.
The network contains network switches and wireless access points (WAPs) from multiple vendors. Some of
the network devices are more than 10 years old and do not support port-based authentication.
TECHNICAL REQUIREMENTS
All of the accounts used for administration must beassigned the minimum amount of permissions.
Web1, Web2, and Web3 must have the identical configurations for the corporate Web site.
The Web servers must contain a local copy of all the Web pages in the Web site. When a Web page is
modified on any of the Web servers, the modifications must be copied automatically to all of the Web
servers.
A user named Admin1 must be responsible for performing the following tasks:
Restarting all of the Web servers.
Backing up and restoring the files on all of the Web servers.
A user named Admin2 must be responsible for performing the following tasks;
Backing up the Active Directory database.
Recovering deleted objects from the Active Directory Recycle Bin.

