What should you recommend?
Your network consists of a single Active Directory forest. The sales department in your company has 600
Windows Server 2008 R2 servers.
You need to recommend a solution to monitor the performance of the 600 servers.
Your solution must meet the following requirements:
Generate alerts when the average processor usage ishigher than 90 percent for 20 minutes.
Automatically adjust the processor monitoring threshold to allow for temporary changes in the workload.
What should you recommend?
You need to promote Server1 to a domain controller by using install from media (IFM)
Your network contains an Active Directory domain named contoso.com.
All domain controllers run Windows Server 2008 R2.
One of the domain controllers is named DC1.
The network contains a member server named Server1 that runs Windows Server 2012.
You need to promote Server1 to a domain controller by using install from media (IFM). What should you do
first?
You need to prevent users from consuming more than 15 percent of the CPU resources
Your network consists of a single Active Directory domain.
All servers run Windows Server 2008 R2.
A server named Server1 has the Remote Desktop Services server role installed.
You notice that several users consume more than 30 percent of the CPU resources throughout the day.
You need to prevent users from consuming more than 15 percent of the CPU resources. Administrators must
not be limited by the amount of CPU resources that they can consume.
What should you do?
Which tool should you use?
Your network contains an Active Directory domain named contoso.com.
The domain contains two domain controllers named DC1 and DC2.
You install Windows Server 2012 on a new computer named DC3.
You need to manually configure DC3 as a domain controller. Which tool should you use?
What should you recommend?
Your network contains a standalone root certification authority (CA).
You have a server named Server1 that runs Windows Server 2008 R2. You issue a server certificate to
Server1. You deploy Secure Socket Tunneling Protocol (SSTP) on Server1.
You need to recommend a solution that allows external partner computers to access internal network resources
by using SSTP.
What should you recommend?
Which two configurations should you identify?
Your network contains an Active Directory forest named contoso.com.
All domain controllers currently run Windows Server2008 R2.
You plan to install a new domain controller named DC4 that runs Windows Server 2012.
The new domain controller will have the following configurations:
Schema master
Global catalog server
DNS Server server role
Active Directory Certificate Services server role
You need to identify which configurations cannot befulfilled by using the Active Directory Installation Wizard.
Which two configurations should you identify? (Eachcorrect answer presents part of the solution. Choose two.)
What should you include in your plan?
Your network consists of a single Active Directory domain. All domain controllers run Windows Server 2008 R2.
You need to plan an auditing strategy that meets the following requirements:
Audits all changes to Active Directory Domain Services (AD DS).
Stores all auditing data in a central location.
What should you include in your plan?
Which domain controller should you identify?
Your network contains an Active Directory forest.
The forest contains two domains named contoso.com and corp.contoso.com.
The forest contains four domain controllers.
The domain controllers are configured as shown in the following table.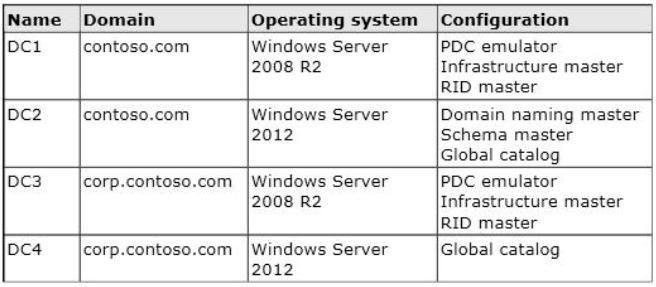
All domain controllers are DNS servers.
In the corp.contoso.com domain, you plan to deploy a new domain controller named DC5.
You need to identify which domain controller must be online to ensure that DC5 can be promoted successfully
to a domain controller. Which domain controller should you identify?
What should you recommend?
Your network contains a single Active Directory domain.
All domain controllers run Windows Server 2008 R2.
There are 1,000 client computers that run Windows 7and that are connected to managed switches.
You need to recommend a strategy for network accessthat meets the following requirements:
Users are unable to bypass network access restrictions.
Only client computers that have up-to-date service packs installed can access the network.
Only client computers that have up-to-date anti-malware software installed can access the network.
What should you recommend?
You need to manage IPAM from Server2
Your network contains an Active Directory domain named contoso.com.
The domain contains servers named Server1 and Server2 that run Windows Server 2012.
Server1 has the IP Address Management (IPAM) Serverfeature installed.
You install the IPAM client on Server2.
You open Server Manager on Server2 as shown in the exhibit. 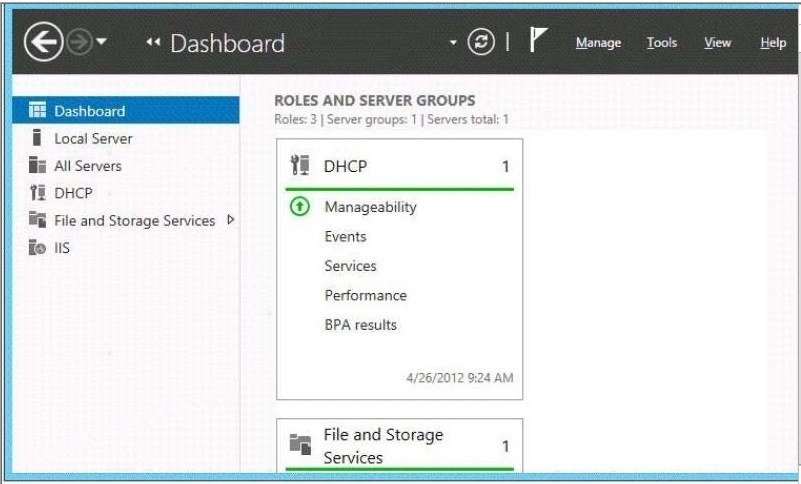
You need to manage IPAM from Server2. What should you do first?

