Which protocol should you use?
HOTSPOT
You install Windows 8 Enterprise on new laptops that will be shipped to remote users in the sales department
of your company. You create new VPN connections on the laptops.
Your company security policy requires that the maximum allowed network outage time for the VPN connection
should be less than 10 minutes.
You need to configure the required timeout.
Which protocol should you use? (To answer, configure the appropriate option or options in the answer area.)
Hot Area:
Which prerequisites should you comply with for eachelement in order to configure the required picture password
DRAG DROP
You administer Windows 8 Pro computers in your company network.
A user informs you that he wants to use a picture password on his computer.
You need to configure a picture password with a custom picture for the user.
Which prerequisites should you comply with for eachelement in order to configure the required picture
password? (To answer, drag the appropriate prerequisite or prerequisites to the correct element or elements in
the answer area. Each prerequisite may be used once, more than once, or not at all. You may need to drag the
split bar between panes or scroll to view content.)
which column shouldyou add to Task Manager?
HOTSPOT
You administer Windows 8 Enterprise (64-bit) computers in your company network. For some applications,
some computers run a 32-bit version of the application, and other computers run a 64- bit version of the
application.
You want to distribute a package that contains updates for the 32-bit applications only.
You need to determine if a particular computer is running 32-bit or 64-bit versions of the applications.
From the Select columns window, which column shouldyou add to Task Manager? (To answer, select the
appropriate column name in the answer area.)
Point and Shoot:
which order should you perform the five actions?
Your network contains an Active Directory domain named contoso.com.
All file servers in the domain run Windows Server 2012.
The computer accounts of the file servers are in anorganizational unit (OU) named OU1.
A Group Policy object (GPO) named GP01 is linked toOU1.
You plan to modify the NTFS permissions for many folders on the file servers by using central access policies.
You need to identify any users who will be denied access to resources that they can currently access once the
new permissions are implemented.
In which order should you perform the five actions?To answer, move all actions from the list of actions to the
answer area and arrange them in the correct order.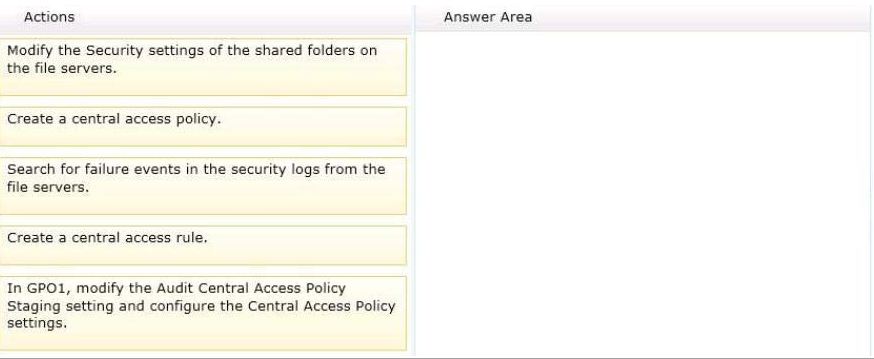
Which three actions should you perform in sequence?
You have a server named SERVER2 that runs Windows Server 2012.
You have storage provisioned on SERVER2 as shown inthe exhibit. (Click the Exhibit button.)
You need to configure the storage so that it appears in Windows Explorer as a drive letter on SERVER1.
Which three actions should you perform in sequence?To answer, move the three appropriate actions fromthe
list of actions to the answer area and arrange themin the correct order.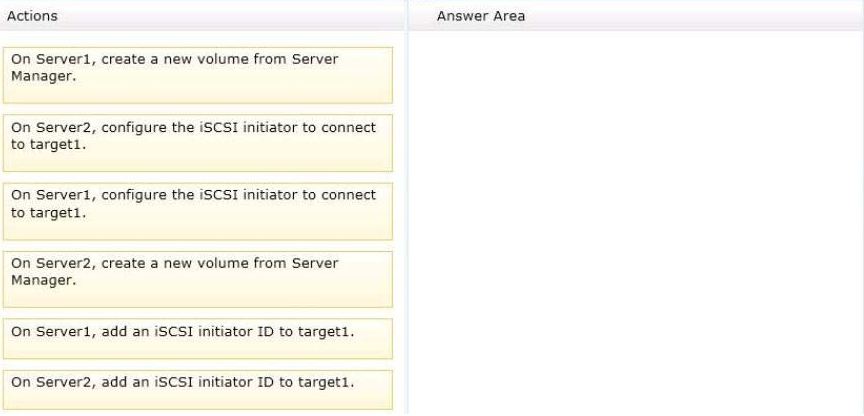
Which three actions should you perform in sequence?
Your network contains an Active Directory domain named contoso.com.
The domain contains a file server named SERVER1.
All servers run Windows Server 2012.
All domain user accounts have the Division attribute automatically populated as part of the user provisioning
process.
The Support for Dynamic Access Control and Kerberosarmoring policy is enabled for the domain.
You need to control access to the file shares on SERVER1 based on the values in the Division attributeand the
Division resource property.
Which three actions should you perform in sequence?To answer, move the three appropriate actions fromthe
list of actions to the answer area and arrange themin the correct order.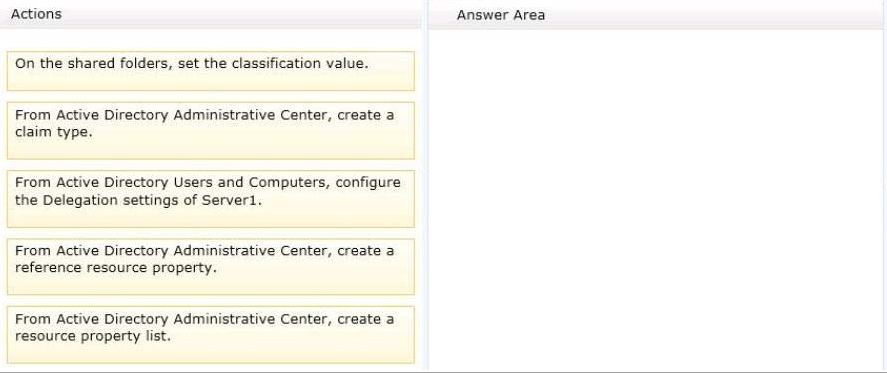
What should you identify?
You have a file server named Server1 that runs Windows Server 2012.
The folders on Server1 are configured as shown in the following table.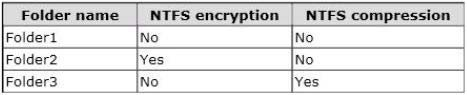
A new corporate policy states that backups must useMicrosoft Online Backup whenever possible.
You need to identify which technology you must use to back up Server1.
The solution must use Microsoft Online Backup whenever possible.
What should you identify? To answer, drag the appropriate backup type to the correct location or locations.
Each backup type may be used once, more than once, or not at all.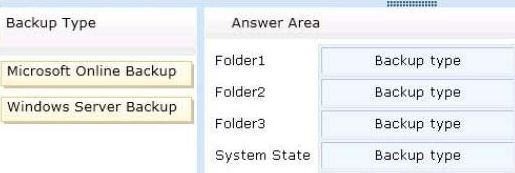
which group on SERVER2 should you add Tech1?
Your network contains an Active Directory domain named contoso.com.
The domain contains two servers named SERVER1 and SERVER2.
Both servers have the IP Address Management (IPAM) Server feature installed.
You have a support technician named Tech1.
Tech1 is a member of the IPAM Administrators group on SERVER1 and SERVER2.
You need to ensure that Tech1 can use Server Manager on SERVER1 to manage IPAM on SERVER2.
To which group on SERVER2 should you add Tech1? To answer, select the appropriate group in the answer
area.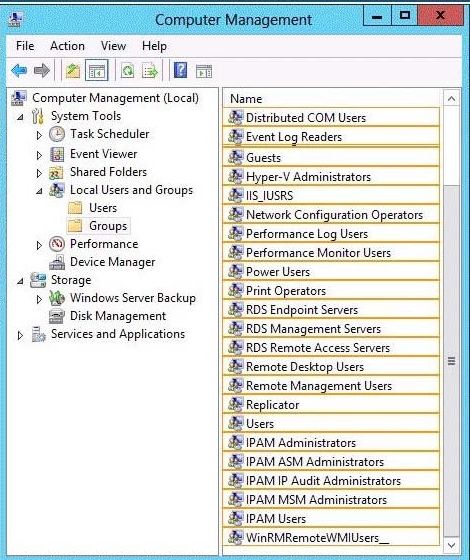
Which attribute should you modify?
Your network contains an Active Directory domain named contoso.com.
The domain contains two Active Directory sites named Site1 and Site2.
You discover that when the account of a user in Site1 is locked out, the user can still log on to the servers in
Site2 for up to 15 minutes by using Remote Desktop Services (RDS).
You need to reduce the amount of time it takes to synchronize account lockout information across the domain.
Which attribute should you modify? To answer, select the appropriate attribute in the answer area.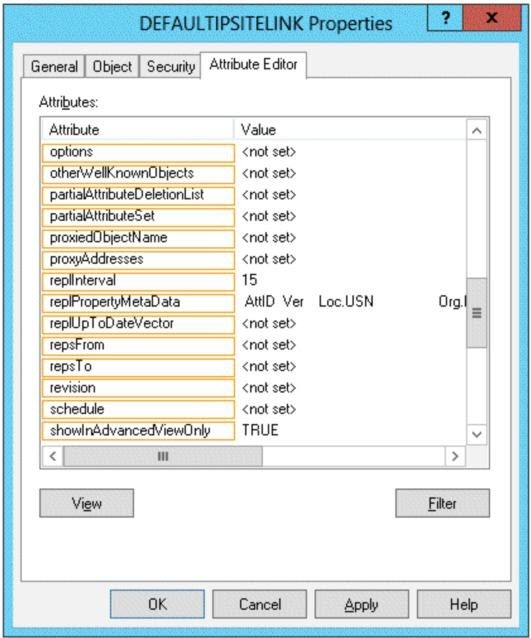
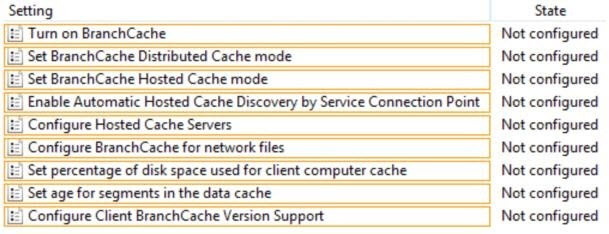
Which two settings should you configure in GPO1?
Your network contains an Active Directory domain named contoso.com.
All client computers run Windows 8 Enterprise.
You have a remote site that only contains client computers.
All of the client computer accounts are located in an organizational unit (OU) named Remote1.
A Group Policy object (GPO) named GPO1 is linked tothe Remote1 OU.
You need to configure BranchCache for the remote site.
Which two settings should you configure in GPO1? (To answer, select the two appropriate settings in the
answer area)