The servers are configured as shown in the following table…
Your network contains an active directory domain named contoso.com
The domain has Remote Desktop Services (RDS) deployed. The domain contains six servers
The servers are configured as shown in the following table
Server1 – Remote Desktop Session Host (RD Session Host)
Server2 – Remote Desktop Session Host (RD Session Host)
Server3 – Remote Desktop Connectin Broker (RD Connection Broker)
Server4 – Remote Desktop Web Access (RD Web Access)
Server5 – Microsoft SQL Server 2008 R2
Server6 – None
You need to ensure that the install imagee that youare testing is selected automatically during the deployment
Your network contains an Active Directory domain named contoso.com
The domain contains a server named Server1 that hasthe Windows Deployment Services server role installed
Server1 hosts multiple install images of windows8 (x64)
You are testing the automated deployment of one of the install images
You need to ensure that the install imagee that youare testing is selected automatically during the deployment
of Windows 8 (x64) to the clients
What should you do?
You need to ensure that you can use the virtual machine as the template virtual machine for the VDI deployment
Your network contains an Active Directory domain named contoso.com
The network contains two servers named Server1 and Server2 that run Windows Server 2012
Server1 has the Remote Desktop Virtualization Host role service installed
Server2 has the Remote Desktop Web Access role service installed
The network contains a Virtual Desktop Infrastructure (VDI)
You plan to use an existing virtual machine as the new pooled virtual desktop base image for Standard
Deployment
The virtual machine has the following configurations:
– Uses a static IP adress
– Is a member of a workgroup
– Runs the Windows 8 operating system
You need to ensure that you can use the virtual machine as the template virtual machine for the VDI
deployment
What should you do?
You need to recommend a solution to provide your company internal auditors with the ability to decryptany encr
Your network contains an Active Directory domain named contoso.com The domain contains an enterprise
cerfication authority (CA)
You plan to implement Encrypting File System (EFS) to encrypt data on the client computer of each user
You need to recommend a solution to provide your company internal auditors with the ability to decryptany
encrypted files on the client computers
What should you recommend?
What three actions should you perform from the Deployment Workbench?
Your network contains an Active Directory domain named contoso.com
The domain contains two servers named Server1 and Server2 that have Microsoft Deployment Toolkit (MDT)
2012 installed
Server1 is used for testing and Server2 is used to deploy images to production computers
On Server1, you have several deployments of Window 7 and Windows 8
You need to replicate only the content related to the Windows 8 deployments from Server1 to Server2
What three actions should you perform from the Deployment Workbench?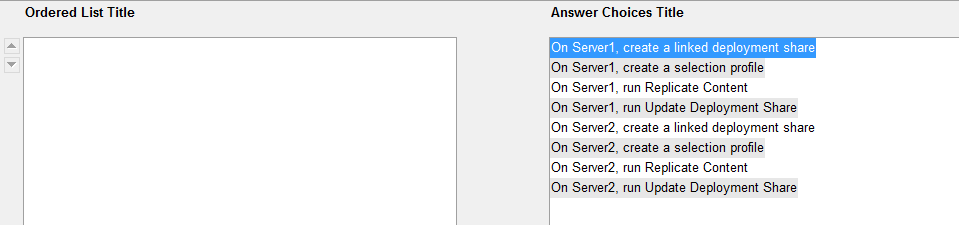
Build List and Reorder:
You need to prepare be downloaded to the users the environment to meet the new security plolicy…?
Your company has a main office and multiple brach offices. The network contains an Active Directory domain
named contoso.com
All servers run Windows Server 2008 R2. All client computers run Windows 7. All users are configured to use
roaming profiles and Folder Redirection
Each user has a personal laptop computer and a personal desktop computer. User occasionally log on to other
computers
The compny intrduces a new security policy, which requires that roaming profiles and redirected folders only
personal laptop computer and desktop computer
You need to prepare be downloaded to the users the environment to meet the new security plolicy
You want to achieve this goal by using the minimum amount of administrative effort
What should you do?
You need to implement a solution to ensure that users can access RD Web Access if a single RD Web Access serve
Your network contains an Active Directory domain named contoso.com. The domain has Remote Desktop
Services (RDS) deployes
The deployment contains two Remote Desktop Web Access (RD Web Access) servers named Server1 and
Server2
You need to implement a solution to ensure that users can access RD Web Access if a single RD Web Access
server fails
Which solution should you implement?
What imaging strategy should you recommend?
Your company has multiple departments. The departments are configured as shown in the following table
Department name User characteristic Requirement
Sales always work outside of the corporate office and cannot access the internal network. All softwaremust be
preinstalled on the users client computer
Human resources always work from inside the internal network and are connected to the LAN. Users must
have core line-of-business applications preinstalled on their computer and must be allowed to install additional
productivity applications as needed
Developers always work from inside the internal network and are connected to the LAN. Users must have all
software deployed by using Group Policy software assignment
You plan to deploy Windows 8 to the client computers. You need to recommend an imaging strategy for each
department
The solution must minimize the amount of time required to deploy the images to the client computers
What imaging strategy should you recommend?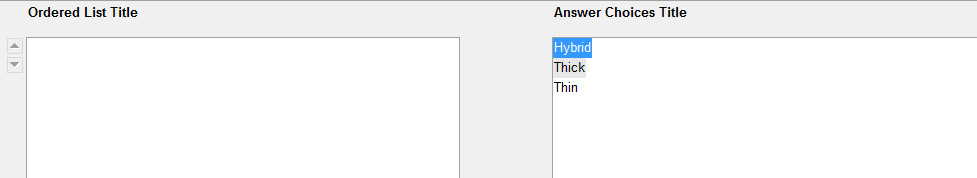
Build List and Reorder:
You need to recommend which task must be performed before you capture the image What should you recommend?
Your network contains an Active Directory domain named contoso.com
The domain contains a server named Server1 that hasMicrosoft System Center 2012 Configuration Manager
installed
You have a client computer named computer1 that runs Windows 8. Computer1 is a Configuration Manager
client
You plan to use Computer1 as a reference computer, and then to deploy an image of the reference computer to
the network
You need to recommend which task must be performed before you capture the image
What should you recommend?
What should you include in the recommendation?
Your network contains an Active Directory domain named contoso.com
You plan to deploy personal virtual desktops
You create a standard desktop that contains multiple desktop shortcuts to line-of-business applications
Administrators frequently update the desktop shortcuts
You need to recommend a solution to prevent users from modifying the desktop shortcuts and from adding
additional files to the desktop
What should you include in the recommendation?

