Which volumes should you identify?
You are evaluating the implementation of data deduplicatton on the planned Windows Server 2012 file servers.
The planned servers will have the identical disk configurations as the current servers.
You need to identify which volumes can be enabled for data deduplication.
Network Infrastructure
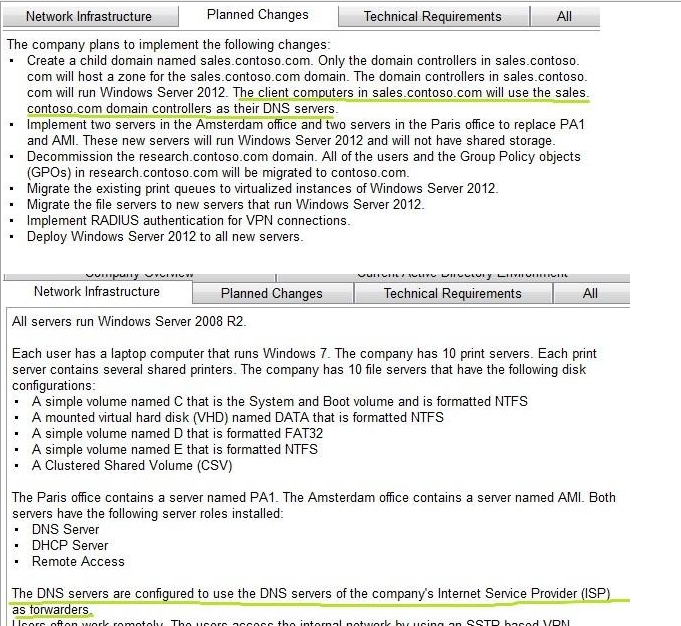
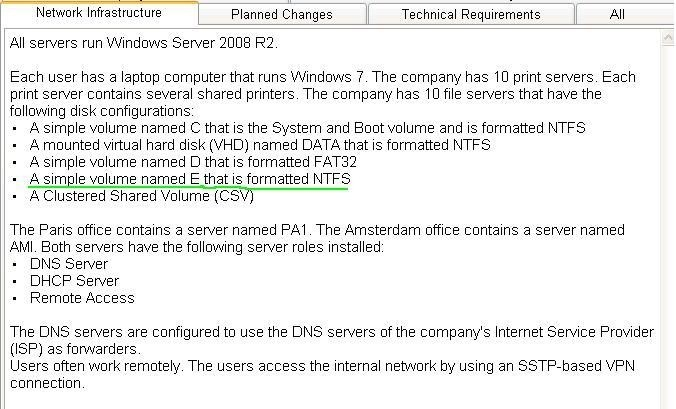
All servers run Windows Server 2008 R2.
Each user has a laptop computer that runs Windows 7. The company has 10 print servers. Each print server
contains several shared printers. The company has 10 file servers that have the following disk configurations:
· A simple volume named C that is the System and Boot volume and is formatted NTFS
· A mounted virtual hard disk (VHD) named DATA thatis formatted NTFS
· A simple volume named D that is formatted FAT32
· A simple volume named E that is formatted NTFS
· A Clustered Shared Volume (CSV)
The Paris office contains a server named PA1. The Amsterdam office contains a server named AMI. Both
servers have the following server roles installed:
· DNS Server
· DHCP Server
· Remote Access
The DNS servers are configured to use the DNS servers of the company’s Internet Service Provider (ISP)as
forwarders.
Users often work remotely. The users access the internal network by using an SSTP-based VPN connection.
Which volumes should you identify? (Each correct answer presents part of the solution. Choose all thatapply.)
What should you recommend?
Which tool should you use?
You implement a new virtualized print server that runs Windows Server 2012.
Visualization Requirements
The company identifies the following virtualizationrequirements:
– Virtualize the application servers.
– Ensure that the additional domain controllers forthe branch offices can be deployed by using domain
controller cloning.
– Automatically distribute the new virtual machinesto Hyper-V hosts based on the current resource usage of the
Hyper-V hosts.
You need to migrate the print queues.
Which tool should you use?
You need to ensure that clients can obtain DHCP address assignments after you shut down PA1 and AMI
Topic 2, Litware, Inc
Overview
Litware, Inc. is a manufacturing company. The company has a main office and two branch offices. The main
office is located in Seattle. The branch offices are located in Los Angeles and Boston.
Existing Environment
Active Directory
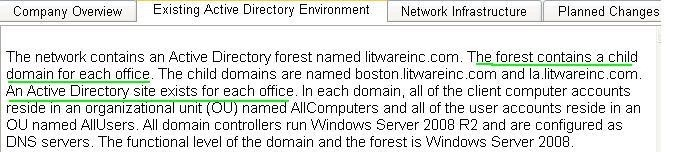
The network contains an Active Directory forest named litwareinc.com. The forest contains a child domain for
each office. The child domains are named boston.litwareinc.com and la.litwareinc.com.
An Active Directory site exists for each office.
In each domain, all of the client computer accountsreside in an organizational unit (OU) named AllComputers
and all of the user accounts reside in an OU named AllUsers.
All domain controllers run Windows Server 2008 R2 and are configured as DNS servers.
The functional level of the domain and the forest is Windows Server 2008.
Network Infrastructure
The main office has the following servers:
– Five physical Hyper-V hosts that run Windows Server 2012
– Three virtual file servers that run Windows Server 2008 R2
– One physical DHCP server that runs Windows Server2008 R2
– Ten physical application servers that run WindowsServer 2012
– One virtual IP Address Management (IPAM) server that runs Windows Server 2012
– One virtual Windows Server Update Services (WSUS)server that runs Windows Server 2008 R2
– One physical domain controller and two virtual domain controllers that run Windows Server 2008 R2
Each branch office has following servers:
– One virtual file server that runs Windows Server 2008 R2
– Two physical Hyper-V hosts that run Windows Server 2012
– One physical DHCP server that runs Windows Server2008 R2
– One physical domain controller and two virtual domain controllers that run Windows Server 2008 R2
All of the offices have a high-speed connection to the Internet. The offices connect to each other by using T1
leased lines.
The IPAM server in the main office gathers data from the DNS servers and the DHCP servers in all of the
offices.
Requirements Planned Changes
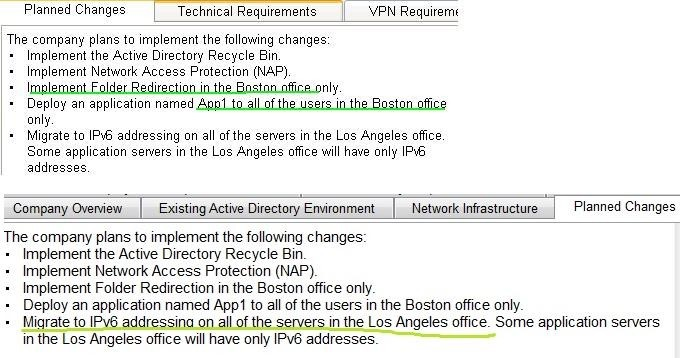
The company plans to implement the following changes:
– Implement the Active Directory Recycle Bin.
– Implement Network Access Protection (NAP).
– Implement Folder Redirection in the Boston officeonly.
– Deploy an application named App1 to all of the users in the Boston office only.
– Migrate to IPv6 addressing on all of the servers in the Los Angeles office. Some application serversin the Los
Angeles office will have only IPv6 addresses.
Technical Requirements
The company identifies the following technical requirements:
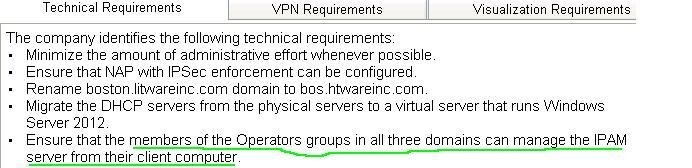
– Minimize the amount of administrative effort whenever possible.
– Ensure that NAP with IPSec enforcement can be configured.
– Rename boston.litwareinc.com domain to bos.htwareinc.com.
– Migrate the DHCP servers from the physical servers to a virtual server that runs Windows Server 2012.
– Ensure that the members of the Operators groups in all three domains can manage the IPAM server from
their client computer.
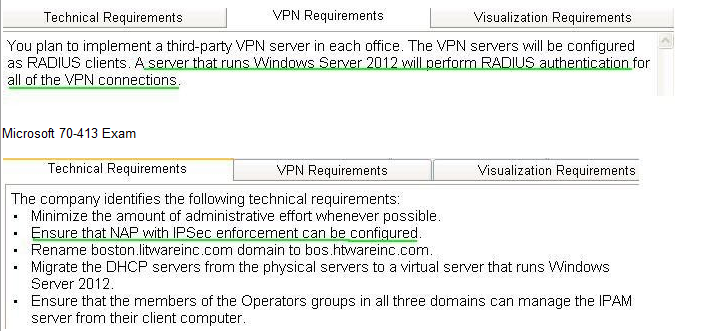
VPN Requirements
You plan to implement a third-party VPN server in each office. The VPN servers will be configured as RADIUS
clients. A server that runs Windows Server 2012 will perform RADIUS authentication for all of the VPN
connections.
Visualization Requirements
The company identifies the following virtualizationrequirements:
– Virtualize the application servers.
– Ensure that the additional domain controllers forthe branch offices can be deployed by using domain
controller cloning.
– Automatically distribute the new virtual machinesto Hyper-V hosts based on the current resource usage of the
Hyper-V hosts.
Server Deployment Requirements
The company identifies the following requirements for the deployment of new servers on the network:
– Deploy the new servers over the network.
– Ensure that all of the server deployments are done by using multicast.
Security Requirements
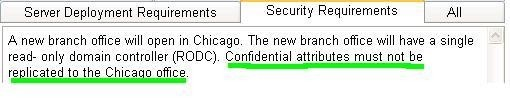
A new branch office will open in Chicago. The new branch office will have a single read-only domain controller
(RODC). Confidential attributes must not be replicated to the Chicago office.
*******************************************************************************************
You implement and authorize the new DHCP servers. You import the server configurations and the scope
configurations from PA1 and AM1.
You need to ensure that clients can obtain DHCP address assignments after you shut down PA1 and AMI. The
solution must meet the technical requirements.
Technical Requirements
The company identifies following technical requirements:
· All changes to Group Policies must be logged.
· Network Access Protection (NAP) policies must be managed centrally.
· Core networking services in each office must be redundant if a server fails.
· The possibility of IP address conflicts during the DHCP migration must be minimized.
· A central log of the IP address leases and the users associated to those leases must be created.
· All of the client computers must be able to resolve internal names and internet names.
· Administrators in the Paris office need to deploya series of desktop restrictions to the entire company by
using Group Policy.
· The new sales.contoso.com domain will contain a web application that will access data from a Microsoft SQL
Server located in the contoso.com domain. The web application must use integrated Windows authentication.
Users’ credentials must be passed from the web applications to the SQL Server.
What should you do?
Which role service should you include in the recommendation?
You need to recommend a remote access solution thatmeets the VPN requirements.
VPN Requirements
You plan to implement a third-party VPN server in each office. The VPN servers will be configured as RADIUS
clients. A server that runs Windows Server 2012 will perform RADIUS authentication for all of the VPN
connections.
Which role service should you include in the recommendation?
What should you include in the recommendation?
Sites overview
Sites in AD DS represent the physical structure, ortopology, of your network. AD DS uses network topology
information, which is stored in the directory as site, subnet, and site link objects, to build the most efficient
replication topology. The replication topology itself consists of the set of connection objects that enable inbound
replication from a source domain controller to the destination domain controller that stores the connection
object. The Knowledge Consistency Checker (KCC) creates these connection objects automatically on each
domain controller. http://technet.microsoft.com/en-us/library/cc754697.aspx
********************************************************************************
You need to recommend changes to the Active Directory site topology to support on the company’s planned
changes.
Planned Changes
The company plans to implement the following changes:
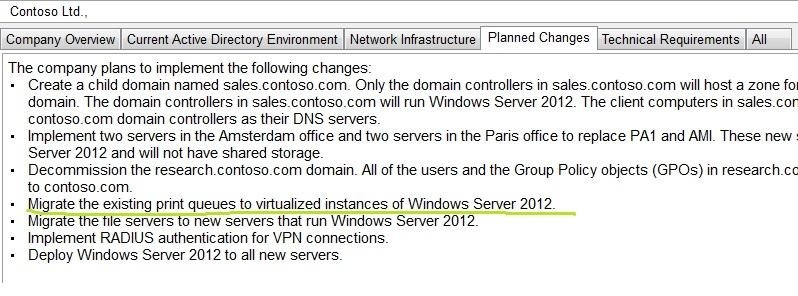
· Create a child domain named sales.contoso.com. Only the domain controllers in sales.contoso.com willhost a
zone for the sales.contoso.com domain. The domain controllers in sales.contoso.com will run Windows Server
2012. The client computers in sales.contoso.com will use the sales.contoso.com domain controllers as their
DNS servers.
· Implement two servers in the Amsterdam office andtwo servers in the Paris office to replace PA1 andAMI.
These new servers will run Windows Server 2012 and will not have shared storage.
· Decommission the research.contoso.com domain. Allof the users and the Group Policy objects (GPOs) in
research.contoso.com will be migrated to contoso.com.
· Migrate the existing print queues to virtualized instances of Windows Server 2012.
· Migrate the file servers to new servers that run Windows Server 2012.
· Implement RADIUS authentication for VPN connections.
· Deploy Windows Server 2012 to all new servers.
What should you include in the recommendation?
What should you include in the recommendation?
You need to recommend an IPAM management solution for the Operators groups. The solution must meet the
technical requirements.
Technical Requirements
The company identifies following technical requirements:
· All changes to Group Policies must be logged.
· Network Access Protection (NAP) policies must be managed centrally.
· Core networking services in each office must be redundant if a server fails.
· The possibility of IP address conflicts during the DHCP migration must be minimized.
· A central log of the IP address leases and the users associated to those leases must be created.
· All of the client computers must be able to resolve internal names and internet names.
· Administrators in the Paris office need to deploya series of desktop restrictions to the entire company by
using Group Policy.
· The new sales.contoso.com domain will contain a web application that will access data from a Microsoft SQL
Server located in the contoso.com domain. The web application must use integrated Windows authentication.
Users’ credentials must be passed from the web applications to the SQL Server.
What should you include in the recommendation?
Which schema attribute properties should you recommend modifying?
You need to recommend a solution that meets the security requirements.
Security Requirements
A new branch office will open in Chicago. The new branch office will have a single read-only domain controller
(RODC). Confidential attributes must not be replicated to the Chicago office.
Which schema attribute properties should you recommend modifying?
What should you include in the recommendation?
You need to recommend a Group Policy strategy to support the company’s planned changes.
Planned Changes
The company plans to implement the following changes:
· Create a child domain named sales.contoso.com. Only the domain controllers in sales.contoso.com willhost a
zone for the sales.contoso.com domain. The domain controllers in sales.contoso.com will run Windows Server
2012. The client computers in sales.contoso.com will use the sales.contoso.com domain controllers as their
DNS servers.
· Implement two servers in the Amsterdam office andtwo servers in the Paris office to replace PA1 andAMI.
These new servers will run Windows Server 2012 and will not have shared storage.
· Decommission the research.contoso.com domain. Allof the users and the Group Policy objects (GPOs) in
research.contoso.com will be migrated to contoso.com.
· Migrate the existing print queues to virtualized instances of Windows Server 2012.
· Migrate the file servers to new servers that run Windows Server 2012.
· Implement RADIUS authentication for VPN connections.
· Deploy Windows Server 2012 to all new servers.
What should you include in the recommendation?
What should you include in the recommendation?
You have a server named Server1 that runs Windows Server 2012.
You have a 3-TB database that will be moved to Server1.
Server1 has the following physical disks:
– Three 2-TB SATA disks that are attached to a single IDE controller
– One 1-TB SATA disk that is attached to a single IDE controller
You need to recommend a solution to ensure that thedatabase can be moved to Server1. The
solution must ensure that the database is availableif a single disk fails.
What should you include in the recommendation?