What should you recommend?
Your company has an Exchange Server 2016 organization named contoso.com.
You need to recommend a solution that meets following requirements:
A user named User1 must be able to send email messages by using an alias of sales@contoso.com in the
From field.
Recipients of the messages must be prevented from the identifying the actual sender of the message.
User1 and a user named User2 must each receive a copy of replies to sales@contoso.com
What should you recommend?
Which cmdlet should you run first?
You have a file server named Server1 that runs Windows Server 2012 R2. Server1 has following hardware
configurations:
16 GB of RAM
A single quad-core CPU
Three network teams that have two network adapters each
You add additional CPUs and RAM to Server1. You repurpose Server1 as a virtualization host. You install the
Hyper-V server role on Server1. You need to create four external virtual switches in Hyper-V.
Which cmdlet should you run first?
What command should you run next?
HOTSPOT
You have a hybrid Exchange Server 2016 organization.
Users use Outlook on the web. All mailboxes currently reside on-premises.
You have an internal public key infrastructure (PKI) that uses a certification authority (CA) named CA1.
Certificates are issued to users to sign and encrypted email messages.
You move a mailbox to Exchange Online and you discover that the mailbox fails to exchange signed or
encrypted email messages from the on-premises mailbox users.
You need to ensure that all of the mailboxes that were moved to Exchange Online can send encrypted email
messages to the on-premises mailboxes. The mailboxes must also be able to receive encrypted email
messages from the on-premises mailboxes.
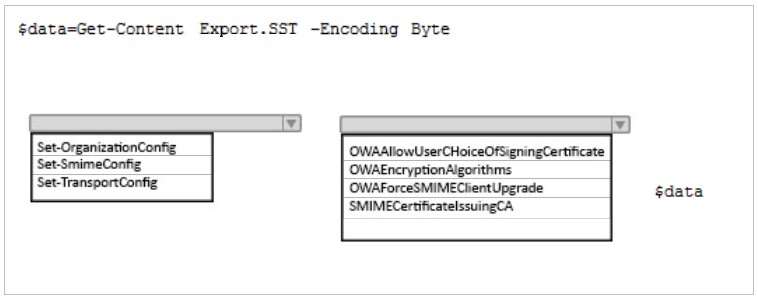
You export the required certificates to a file named Export.sst.
What command should you run next? To answer, select appropriate options in the answer area.
Hot Area:
Which tool should you use?
Your network contains an Active Directory domain named contoso.com. The domain contains a server named
Server1. Server1 runs Windows Server 2012 R2.
You need to create 3-TB virtual hard disk (VHD) on Server1.
Which tool should you use?
What should you identify?
HOTSPOT
You are designing an Exchange Server 2016 organization. The organization will use a single namespace of
mail.contoso.com for all client access protocols.
You plan to use load balancers.
You identify the following requirements for the load balancing solution:
The Edge Transport server log files must contain the original IP address of the SMTP hosts.
Clients must be able to connect only when they use the approved hostnames and the approved virtual
directories.
You need to identify which type of load balancer meets each requirement.
What should you identify? To answer, select the appropriate options in the answer area.
Hot Area:
You need to manage DHCP on Server2 by using the DHCP co…
Your network contains an Active Directory domain named contoso.com. The domain contains two servers
named Server1 and Server2. Server1 runs Windows Server 2012 R2. Server2 runs Windows Server 2008 R2
Service Pack 1 (SP1) and has the DHCP Server server role installed. You need to manage DHCP on Server2
by using the DHCP console on Server1.
What should you do first?
Which three actions should you perform?
You have an Exchange Server 2016 organization.
You need to ensure that users in each department download an Offline Address Book (OAB) that only contains
the users in their department. The solution must ensure that all of the users can continue to see all the other
users in the organization.
Which three actions should you perform? Each correct answer presents part of the solution.
You need to restore the membership of Group1.What shoul…
Your network contains an Active Directory forest named contoso.com. The forest contains a single domain. All
domain controllers run Windows Server 2012 R2. The domain contains two domain controllers. The domain
controllers are configured as shown in the following table.
Active Directory Recycle Bin is enabled. You discover that a support technician accidentally removed 100 users
from an Active Directory group named Group1 an hour ago. You need to restore the membership of Group1.What should you do?
How is the IBM Content Template Catalog delivered for i…
How is the IBM Content Template Catalog delivered for installation?
You need to provide the members of RODC_Admins with the…
Your network contains an Active Directory domain named contoso.com. The domain contains a read-only
domain controller (RODC) named RODC1.
You create a global group named RODC_Admins.
You need to provide the members of RODC_Admins with the ability to manage the hardware and the software
on RODC1.
The solution must not provide RODC_Admins with the ability to manage Active Directory objects.
What should you do?