You need to ensure that the certificate used to encrypt data can be accessed by the cloud service application
You manage a cloud service that utilizes data encryption.
You need to ensure that the certificate used to encrypt data can be accessed by the cloud
service application.
What should you do?
Which four steps should you perform in sequence?
DRAG DROP
You manage an application hosted on cloud services. The development team creates a new
version of the application. The updated application has been packaged and stored in an
Azure Storage account.
You have the following requirements:
Deploy the latest version of the application to production with the least amount of downtime.
Ensure that the updated application can be tested prior to deploying to the Production site,
Ensure that the original version of the application can be restored until the new version is
verified.
Which four steps should you perform in sequence? To answer, move the appropriate actions
from the list of actions to the answer area and arrange them in the correct order.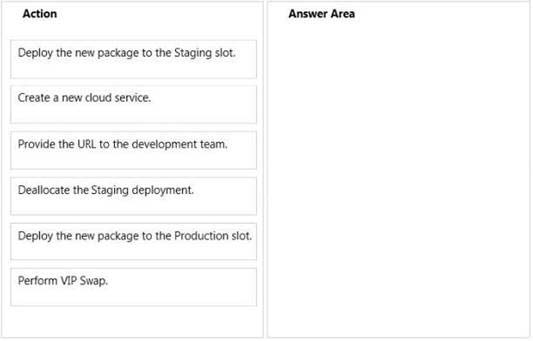
You need to ensure that you are able to deploy the BGInfo and VMAccess extensions
You administer a Windows Server virtual machine (VM).
You upload the VM to Azure.
You need to ensure that you are able to deploy the BGInfo and VMAccess extensions.
What should you do?
Which two actions should you perform?
You manage a cloud service that supports features hosted by two instances of an Azure
virtual machine (VM). You discover that occasional outages cause your service to fail. You
need to minimize the impact of outages to your cloud service. Which two actions should you
perform? Each correct answer presents part of the solution.
Which PowerShell command should you use?
You administer an Azure subscription with an existing cloud service named
contosocloudservice. Contosocloudservice contains a set of related virtual machines (VMs)
named ContosoDC, ContosoSQL and ContosoWeb1.
You want to provision a new VM within contosocloudservice.
You need to use the latest gallery image to create a new Windows Server 2012 R2 VM that
has a target IOPS of 500 for any provisioned disks.
Which PowerShell command should you use?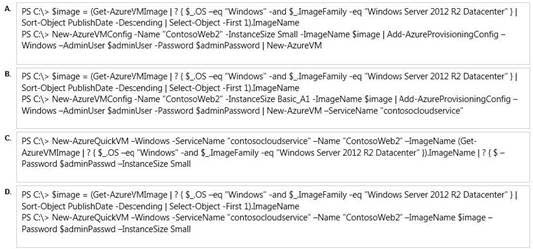
You need to ensure that users in CS01 can access the Accounts VM by using port 8080
Your company has two cloud services named CS01 and CS02. You create a virtual machine
(VM) in CS02 named Accounts.
You need to ensure that users in CS01 can access the Accounts VM by using port 8080.
What should you do?
Which Power Shell cmdlets should you use?
DRAG DROP
You administer an Azure Virtual Machine (VM) named server!. The VM is in a cloud service
named ContosoService1.
You discover that the VM is experiencing storage issues due to increased application
logging on the server.
You need to create a new 256-GB disk and attach it to the server.
Which Power Shell cmdlets should you use? To answer, drag the appropriate cmdlet to the
correct location in the Power Shell command. Each cmdlet may be used once, more than
once, or not at all. You may need to drag the split bar between panes or scroll to view content.
Which type of monitoring should you configure?
You administer a solution deployed to a virtual machine (VM) in Azure. The VM hosts a web
service that is used by several applications. You are located in the US West region and have
a worldwide user base.
Developers in Asia report that they experience significant delays when they execute the
services.
You need to verify application performance from different locations.
Which type of monitoring should you configure?
Which Power Shell command should you use?
You are the administrator for three Azure subscriptions named Dev, Test, and Prod. Your
Azure Power Shell profile is configured with the Dev subscription as the default. You need to
create a new virtual machine in the Test subscription by using the least administrative effort.
Which Power Shell command should you use?
You need to isolate the network traffic among the four VMs
You administer an Azure solution that uses a virtual network named fabVNet. FabVNet has a
single subnet named Subnet-1.
You discover a high volume of network traffic among four virtual machines (VMs) that are
part of Subnet-1.
You need to isolate the network traffic among the four VMs. You want to achieve this goal
with the least amount of downtime and impact on users.
What should you do?

