Which three actions should you perform?
Your network contains an Active Directory forest named contoso.com. The forest contains an
enterprise root certification authority (CA) named CA1. The network contains a server named EX1
that has Exchange Server 2013 installed. A partner company named A . Datum Corporation has an
Active Directory domain named adatum.com. The domain contains a server named EX5 that has
Exchange Server 2010 Service Pack 2 (SP2) installed. EX5 has a Receive connector that is configured
for mutual TLS. Users in contoso.com plan to send email messages that contain sensitive data to
users in adatum.com. You need to ensure that all of the email messages sent from contoso.com to
adatum.com are encrypted by using TLS. The solution must ensure that EX1 and EX5 validate server
certificates. Which three actions should you perform? (Each correct answer presents part of the
solution. Choose three.)
Which cmdlet should you use?
You have an Exchange Server 2013 organization that contains five servers. Your company has a
finance department, a marketing department, and a research department. Users in the marketing
department are prevented from creating more than two Exchange ActiveSync device associations.
You have a user named User5 in the finance department. You need to prevent User5 from creating
more than two Exchange ActiveSync device associations. Which cmdlet should you use?
Which three commands should you run?
You have an Exchange Server organization that contains three servers that have Exchange Server
2013 installed and one server that has Exchange Server 2010 installed. You create the custom RBAC
roles shown in the following table.
The Seattle help desk manages all of the users in an organizational unit (OU) named Seattle. The
Miami help desk manages all of the users in an OU named Miami. The IT Administrators manage all
of the users in the forest. You need to recommend which commands must be run to prevent only
the members of both help desks from modifying the properties of users who have a department
attribute value of Manager. Which three commands should you run? (Each correct answer presents
part of the solution. Choose three.)
Which three actions should you perform?
You have an Exchange Server 2007 organization.
You recently deployed a server that has Exchange Server 2013 installed.
The Exchange Server organization contains three servers. The servers are configured as shown in the following table.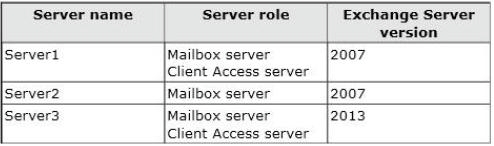
Server2 contains a mailbox for a user named User1. You move the mailbox of User1 to Server3. After
the move, User1 fails to access his mailbox by using Outlook Web App. Users who have mailboxes on
Server1 and Server2 can access their mailboxes by using Outlook Web Access. You need to ensure
that User1 can access his mailbox from the Internet by using Outlook Web App at
https://mail.contoso.com. The solution must ensure that users who have mailboxes on Server1 and
Server2 can continue to use Outlook Web Access. Which three actions should you perform? (Each
correct answer presents part of the solution. Choose three.)
Which cmdlet should you run?
You host Exchange Server 2013 organizations for several hundred tenants. The infrastructure
contains several custom transport agents. You need to prevent the transport agents from
overloading the processors on one of the Exchange servers. Which cmdlet should you run?
Which cmdlet should you run?
You have an Exchange Server 2013 organization that contains two servers named EX1 and EX2. EX1
and EX2 are members of a database availability group (DAG) named DAG1. DAG1 contains four
mailbox databases. All databases are active on EX1 and replicate to EX2. You start an unplanned
maintenance on EX1 and shut down EX1. You discover that the databases do not mount on EX2. You
restart EX1 and the databases mount automatically on EX1. You need to identify what prevents the
databases from switching over successfully to EX2. Which cmdlet should you run?
Which three actions should you perform?
DRAG DROP
You have an Exchange Server 2013 organization that contains four servers named EX1, EX2, EX3, and
EX4. All of the servers are members of a database availability group (DAG) named DAG1.
Each server has a copy of a mailbox database named DB1. DB1 has the following characteristics:
• The replay lag time on Ex4 is set to 14 days.
• Single item recovery on all of the servers is set to 14 days.
• None of the servers have Volume Shadow Copy Service (VSS) backups.
Ex4 has a folder named F:\RDB that is used to store database files during restore operations.
Twenty days ago, a user named User1 deleted an email message that had a subject of “Sales
Report”.
You need to restore the deleted email message to the mailbox of User1.
You copy the lagged database and the log files that are older than 20 days to F:\RDB.
Which three actions should you perform?
To answer, move the three appropriate actions from the list of actions to the answer area and
arrange them in the correct order.
Which three commands should you run?
DRAG DROP
You have an Exchange Server 2013 organization that contains a server named EX1. You have a user
named User1 in the marketing department. You need to prevent User1 from submitting more than
50 email messages per minute to the Exchange Server organization by using Microsoft Outlook.
Which three commands should you run?
To answer, move the three appropriate commands from the list of commands to the answer area
and arrange them in the correct order.
You need to ensure that the email messages are sent to Site C as quickly as possible
Your company has three offices. Each office is configured as an Active Directory site. You have three
servers that have Exchange Server 2013 installed named EX1, EX2 and EX3. All three servers have the
Client Access server role and the Mailbox server role installed. The Active Directory site links and
costs are configured as shown in the exhibit. (Click the Exhibit button.)
Site B is designated as a hub site. EX2 fails. You discover that all email messages sent from the users
in Site A to the users in Site C are queued on a server in Site A. You need to ensure that the email
messages are sent to Site C as quickly as possible. What should you do first?
Which WAN link or links should you identify?
Your network contains an internal network and a perimeter network. The internal network contains
four offices. The perimeter network is located in a separate office. Each internal office has a direct
WAN link to all other internal offices. Each of the four offices that make up the internal network is
configured as an Active Directory site. The Active Directory sites and site links are configured as
shown in the exhibit. (Click the Exhibit button.)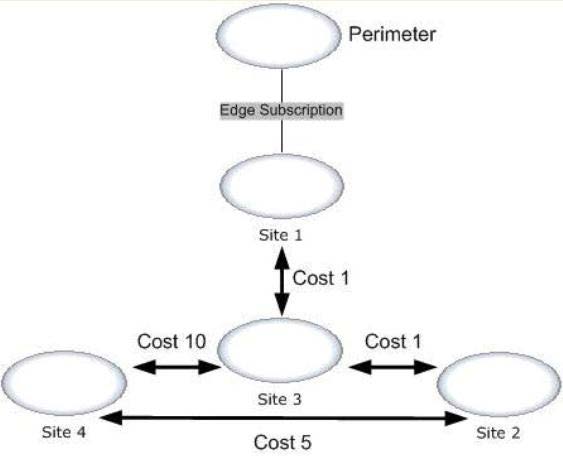
Your company has an Exchange Server 2013 organization. Each site contains two servers that have
the Mailbox server role and the Client Access server role installed. To the perimeter network, you
deploy two servers that have Exchange Server 2010 Service Pack 2 (SP2) and the Edge Transport
server role installed. You configure an Edge Subscription to Site1. You deploy a new email
notification application to Site4. The application will send 25,000 email messages daily to external
recipients. You need to identify which WAN links will have increased traffic from the new email
application. Which WAN link or links should you identify? (Each answer presents part of the solution.
Choose all that apply.)

