You need to monitor the usage of the APP-V applications
###BeginCaseStudy###
Case Study: 2
A.Datum Corporation
Overview
A.Datum Corporation is a geological research company. The company has a main
office and a branch office. The main office is located in Seattle. The branch office is
located in Miami. Users in the research department work in the Miami office.
Existing Environment
Active Directory
The network contains a single-domain Active Directory forest named adatum.com.
Network Infrastructure. The relevant servers on the network are configured as shown
in the following table.
Content on SRV-FS1 and SRV-FS2 is replicated by using Distributed File System
(DFS) Replication. All shared content is accessible through the UNC path of
\\contoso.com\shared\data. All client computers run Windows XP. All of the client
computers have Microsoft Office 2007 installed. All applications are installed locally
on the client computers. The Miami office connects to the Seattle office by using a
site-to-site VPN connection. Research users in the Miami office use two applications
named App1 and App2. The research users are divided into two groups named
Adatum\ResearchManagers and Adatum\ResearchStaff. The IT department has a
custom install image of Windows 8. The image contains internally developed
Windows Store apps. Windows Server Update Services (WSUS) is used to deploy
patches to the client computers.
User Issues
Users report that when App1 and App2 run concurrently, the applications crash.
Requirements Planned Changes
The company plans to implement the following changes:
Deploy a Remote Desktop Services (RDS) infrastructure that runs Windows Server
2012. The infrastructure will be located in the Seattle office and will contain the
following servers:
Two Remote Desktop Virtualization Host (RD Virtualization Host) servers
Two Remote Desktop Connection Broker (RD Connection Broker) servers
Two Remote Desktop Session Host (RD Session Host) servers
Two Remote Desktop Web Access (RD Web Access) servers
Two Remote Desktop Gateway (RD Gateway) servers
Implement the desktops of the users in the Miami office by using a Virtual Desktop
Infrastructure (VDI) and replace the desktop hardware with thin client devices.
Deploy a Windows Server 2012-based Microsoft Application Virtualization (App-V)
infrastructure in the Seattle office that contains the following servers:
Two App-V management servers
Two App-V publishing servers
One App-V reporting server
Standardize the client operating system on the 64-bit version of Windows 8.
Publish an application named App3 as a RernoteApp program.
Technical Requirements
The company must meet the following technical requirements:
The disk space used by the VDI must be minimized.
The amount of administrative effort must be minimized whenever possible.
The members of Adatum\ResearchManagers must have priority to the system
resources on the RD Session Host servers.
The availability of the RemoteApps programs, the App-V apps, and the virtual
desktops must not be affected if a single server fails.
The RD Session Host server will be installed on a server that is several years old.
Only 20 percent of the sessions must be established to this server.
Application Requirements
The company must meet the following application requirements:
Several custom add-ins for Office 2010 must be deployed.
App1 and App2 must be published as Remote App programs.
Application conflicts between App1 and App2 must be eliminated.
Office 2010 must be deployed by using an existing App-V package.
Updated Windows Store apps must be included in the Windows 8 image.
The reporting server must be used to monitor the usage of the App-V apps.
Users in the human resource (HR) department must be able to use existing 16-bit
applications.
The research users must be able to launch App3 by double-clicking files that have
an .app3 extension.
###EndCaseStudy###
You need to monitor the usage of the APP-V applications. The Solution must meet the
application requirements. What should you do?
You need to ensure that access requests are unaffected when the rule is published
Your network contains an Active Directory domain named contoso.com. All servers run
Windows Server 2012 R2.
You are creating a central access rule named TestFinance that will be used to audit
members of the Authenticated users group for access failure to shared folders in the finance
department.
You need to ensure that access requests are unaffected when the rule is published. What
should you do?
Which Windows PowerShell command should you run?
You deploy an Active Directory Federation Services (AD FS) 2.1 infrastructure. The
infrastructure uses Active Directory as the attribute store.
Some users report that they fail to authenticate to the AD FS infrastructure.
You discover that only users who run third-party web browsers experience issues.
You need to ensure that all of the users can authenticate to the AD FS infrastructure
successfully.
Which Windows PowerShell command should you run?
How should you configure the certificate request?
DRAG DROP
Your network contains an Active Directory domain named contoso.com. The domain
contains a server named Server1 that runs Windows Server 2012 R2.
You plan to install the Active Directory Federation Services server role on Server1 to allow
for Workplace Join.
You run nslookupenterpriseregistration and you receive the following results:
You need to create a certificate request for Server1 to support the Active Directory
Federation Services (AD FS) installation.
How should you configure the certificate request? To answer, drag the appropriate names to
the correct locations. Each name may be used once, more than once, or not at all. You may
need to drag the split bar between panes or scroll to view content.
You need to ensure that all users from the Internet are pre-authenticated before they can access App1
DRAG DROP
Your network contains an Active Directory domain named contoso.com. The domain
contains two servers named Server1 and Server3. The network contains a standalone
server named Server2. All servers run Windows Server 2012 R2. The servers are configured
as shown in the following table.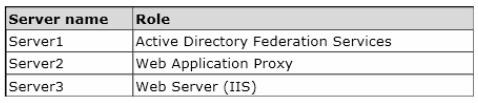
Server3 hosts an application named App1. App1 is accessible internally by using the URL
https://app1.contoso.com. App1 only supports Integrated Windows authentication.
You need to ensure that all users from the Internet are pre-authenticated before they can
access App1.
What should you do? To answer, drag the appropriate servers to the correct actions. Each
server may be used once, more than once, or not at all. You may need to drag the split bar
between panes or scroll to view content.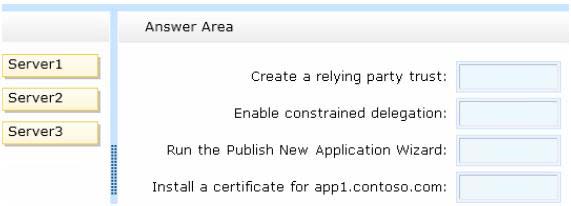
Which rule types should you configure on each side of the federated trust?
DRAG DROP
Your network contains two Active Directory forests named contoso.com and adatum.com. All
domain controllers run Windows Server 2012 R2.
A federated trust exists between adatum.com and contoso.com. The trust provides
adatum.com users with access to contoso.com resources.
You need to configure Active Directory Federation Services (AD FS) claim rules for the
federated trust.
The solution must meet the following requirements:
• In contoso.com, replace an incoming claim type named Group with an outgoing claim
type named Role.
• In adatum.com, allow users to receive their tokens for the relying party by using their
Active Directory group membership as the claim type.
The AD FS claim rules must use predefined templates.
Which rule types should you configure on each side of the federated trust?
To answer, drag the appropriate rule types to the correct location or locations. Each rule type
may be used once, more than once, or not at all. You may need to drag the split bar
between panes or scroll to view content.
What should you identify?
Your network contains a perimeter network and an internal network. The internal network
contains an Active Directory Federation Services (AD FS) 2.1 infrastructure. The
infrastructure uses Active Directory as the attribute store.
You plan to deploy a federation server proxy to a server named Server2 in the perimeter
network.
You need to identify which value must be included in the certificate that is deployed to
Server2.
What should you identify?
Which two actions should you perform?
Your network contains an Active Directory domain named contoso.com. The domain
contains servers named Server1 and Server2 that run Windows Server 2012 R2. Server1
has the Active Directory Federation Services server role installed. Server2 is a file server.
Your company introduces a Bring Your Own Device (BYOD) policy.
You need to ensure that users can use a personal device to access domain resources by
using Single Sign-On (SSO) while they are connected to the internal network.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
You need to move all of the applications and the services from Cluster1 to Cluster2
Your network contains two servers named Server1 and Server2 that run Windows Server
2008 R2. Server1 and Server2 are nodes in a failover cluster named Cluster1. The network
contains two servers named Server3 and Server4 that run Windows Server 2012 R2.
Server3 and Server4 are nodes in a failover cluster named Cluster2.
You need to move all of the applications and the services from Cluster1 to Cluster2.
What should you do first from Failover Cluster Manager?
What should you run from Windows PowerShell?
DRAG DROP
Your network contains an Active Directory domain named contoso.com. The domain
contains four member servers named Server 1, Server2, Server3, and Server4. All servers
run Windows Server 2012 R2.
Server1 and Server2 are located in a site named Site1. Server3 and Server4 are located in a
site named Site2. The servers are configured as nodes in a failover cluster named Cluster1.
Cluster1 is configured to use the Node Majority quorum configuration.
You need to ensure that Server1 is the only server in Site1 that can vote to maintain quorum.
What should you run from Windows PowerShell?
To answer, drag the appropriate commands to the correct location. Each command may be
used once, more than once, or not at all. You may need to drag the split bar between panes
or scroll to view content.

