which fixed database role or roles should you add the users?
DRAG DROP
You administer a database named SalesDb that has users named UserA, userB, and UserC. You need
to ensure that the following requirements are met:
• UserA must be able to provide Windows logins access to the database.
• UserB must be able to select, update, delete, and insert data to the database tables.
• UserC must be able to create new tables and stored procedures.
You need to achieve this goal by granting only the minimum permissions required. To which fixed
database role or roles should you add the users? (To answer, drag the appropriate use role or roles.
Answer choices may be used once, more than once, or not at all. Answer targets may be
additionally, you may need to drag the split bar between panes or scroll to view content.)
Which three actions should you perform in sequence?
DRAG DROP
You administer a Microsoft SQL Server 2012 database. All database traffic to the SQL Server must be
encrypted by using secure socket layer (SSL) certificates or the connection must be refused. Network
administrators have deployed server certificates to the Windows store of all Windows servers on the
network from a trusted Certificate Authority. This is the only Certificate Authority allowed to
distribute certificates on the network.
You enable the Force Encryption flag for the MSSQLServer protocols, but client computers are
unable to connect. They receive the following error message:
“A connection was successfully established with the server, but then an error occurred during the
pre-login handshake, (provider: SSL Provider, error: 0 – The certificate chain was issued by an
authority that is not trusted.) (Microsoft SQL Server)”
You notice the following entry in the SQL Server log:
“A self-generated certificate was successfully loaded for encryption.”
You need to configure SQL Server to encrypt all client traffic across the network. You also need to
ensure that client computers are able to connect to the server by using a trusted certificate. Which
three actions should you perform in sequence? (To answer, move the appropriate actions from the
list of actions to the answer area and arrange them in the correct order.)
Which three actions should you perform?
DRAG DROP
Your network contains an Active Directory domain named contoso.com. The domain
contains a server named Server1 that runs Windows Server 2012. Server1 resides in the
perimeter network and has the Remote Access server role installed.
Some users have laptop computers that run Windows 7 and are joined to the domain. Some
users work from home by using their home computers. The home computers run either
Windows XP, Windows Vista/ Windows 7, or Windows 8.
You need to configure the computers for remote access.
Which three actions should you perform?
To answer, move the three appropriate actions from the list of actions to the answer area
and arrange them in the correct order.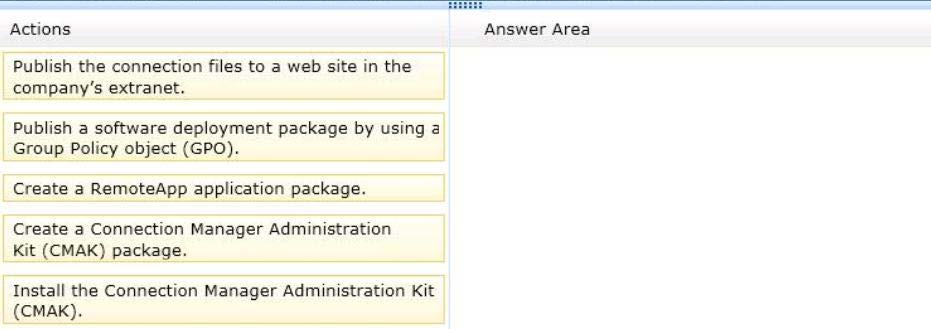
Which servers should you identify?
DRAG DROP
Your network contains an Active Directory domain named contoso.com. The domain
contains five servers. The servers are configured as shown in the following table.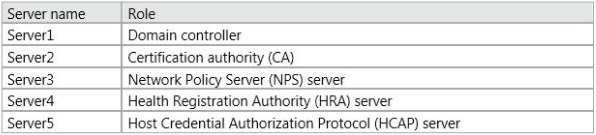
You plan to implement Network Access Protection (NAP) with IPSec enforcement on all client computers.
You need to identify on which servers you must perform the configurations for the NAP deployment.
Which servers should you identify? To answer, drag the appropriate servers to the correct
actions. Each server may be used once, more than once, or not at all. You may need to drag
the split bar between panes or scroll to view content.)
Which solutions should you identify?
DRAG DROP
Your company plans to deploy a remote access solution to meet the following requirements:
Ensure that client computers that are connected to the Internet can be managed remotely
without requiring that the user log on.
Ensure that client computers that run Windows Vista or earlier can connect remotely.
Ensure that non-domain-joined computers can connect remotely by using TCP port 443.
You need to identify which remote access solutions meet the requirements.
Which solutions should you identify?
To answer, drag the appropriate solution to the correct requirement in the answer area. Each
solution may be used once, more than once, or not at all. Additionally, you may need to drag
the split bar between panes or scroll to view content.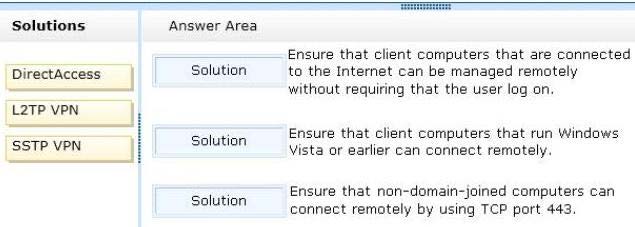
Which three actions should you identify?
DRAG DROP
Your network contains an Active Directory domain named contoso.com. The domain
contains a server named Server1 that runs Windows Server 2008. Server1 is configured as
an enterprise certification authority (CA).
You back up all of the data on Server1, and then export the private and public keys of the CA,
You plan to replace Server1 with a new member server that was purchased recently.
You need to identify which actions must be performed on the new server to restore the
certificate services of Server1.
Which three actions should you identify?
To answer, move the three appropriate actions from the list of actions to the answer area
and arrange them in the correct order.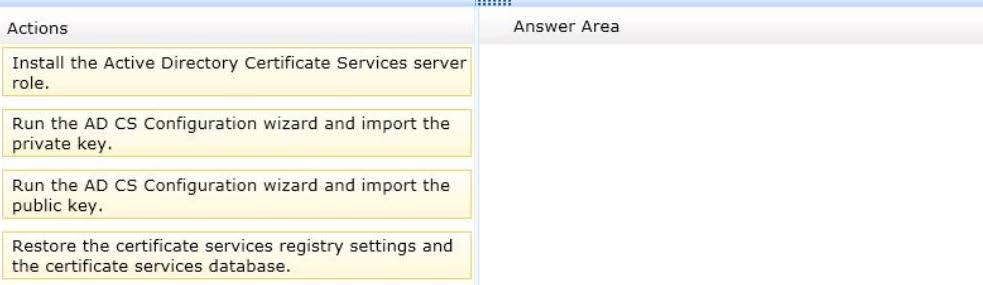
Which five actions should you identify?
DRAG DROP
Your network contains an Active Directory domain named contoso.com. The domain
contains a server named Server1 that runs Windows Server 2008 R2. Server1 is a file
server.
You deploy a new member server named Server2 that runs Windows Server 2012.
You plan to migrate file shares from Server1 to Server2. File share and NTFS permissions
are assigned only to domain local groups.
You need to identify which actions are required to perform the migration.
Which five actions should you identify?
To answer, move the five appropriate actions from the list of actions to the answer area and
arrange them in the correct order.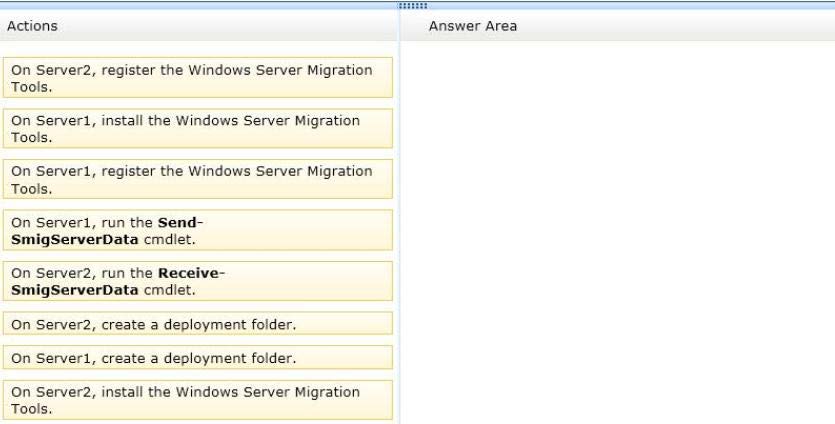
You need to design the Active Directory site topology to meet the following requirements:
Your network contains an Active Directory domain named contoso.com. The domain
contains three Active Directory sites. The Active Directory sites are configured as shown in
the following table.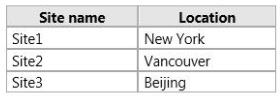
The sites connect to each other by using the site links shown in the following table.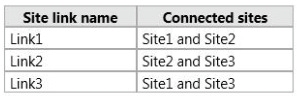
You need to design the Active Directory site topology to meet the following requirements:
+ Ensure that all replication traffic between Site2 and Site3 replicates through Site1 if a domain
controller in Site1 is available.
+ Ensure that the domain controllers between Site2 and Site3 can replicate if all of the domain
controllers in Site1 are unavailable.
What should you do?
Which changes should you recommend?
DRAG DROP
Your network contains an Active Directory forest named contoso.com.
Your company merges with another company that has an Active Directory forest named
litwareinc.com.
Each forest has one domain.
You establish a two-way forest trust between the forests.
The network contains three servers. The servers are configured as shown in the following table.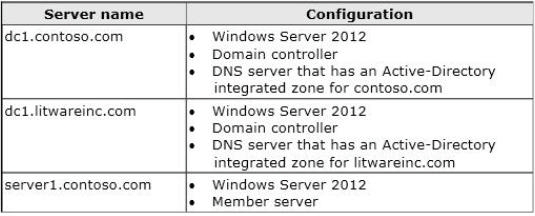
You confirm that the client computers in each forest can resolve the names of the client
computers in both forests.
On dc1.litwareinc.com, you create a zone named GlobalNames.
You need to recommend changes in both forests to ensure that the users in both forests can
resolve single-label names by using the GlobalNames zone in litwareinc.com.
Which changes should you recommend?
To answer, drag the appropriate configuration to the correct server in the answer area. Each
configuration may be used once, more than once, or not at all. Additionally, you may need to
drag the split bar between panes or scroll to view content.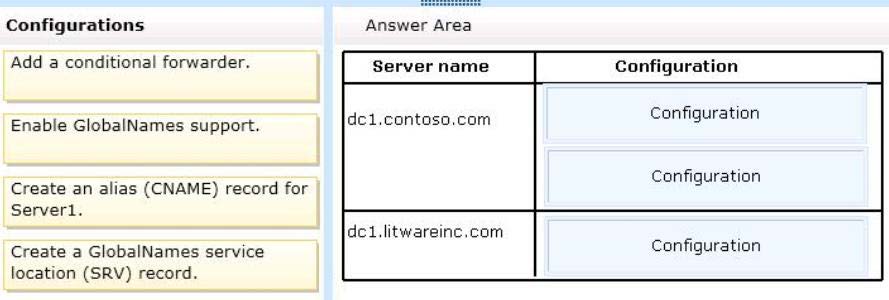
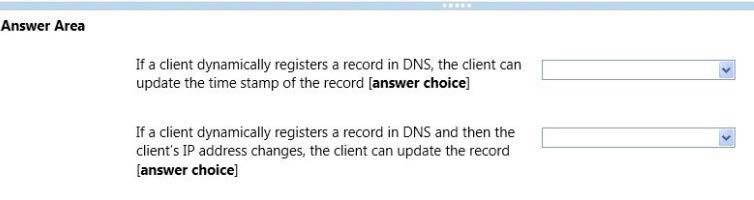
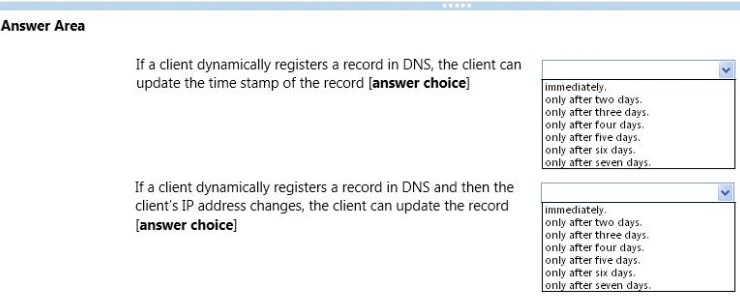
Use the drop-down menus to select the answer choice that completes each statement.
HOTSPOT
You have a domain controller that hosts an Active Directory-integrated zone. On the domain
controller, you run the following cmdlet:
PS C:\> Get-DnsServerScavenging
NoRefreshlnterval:2.00:00:00
Refreshlnterval:3.00:00:00
Scavenginglnterval:4.00:00:00
ScavengingState:True
LastScavengeTime:1/30/2014 9:10:36 AM
Use the drop-down menus to select the answer choice that completes each statement.