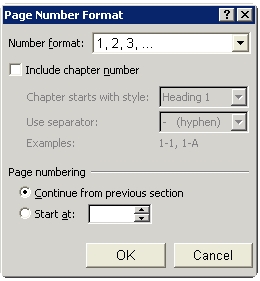
What action should he perform in the dialog box to accomplish the task?
Mark the option/button in the following image that will open the Microsoft Office Backstage view.
In Microsoft Word 2010, the Microsoft Office Backstage view helps a user to manage files and the
data about them. It also helps in creating, saving, inspecting hidden metadata or personal
information, and setting options. Mark the option/button in the following image that will open the
Microsoft Office Backstage view.
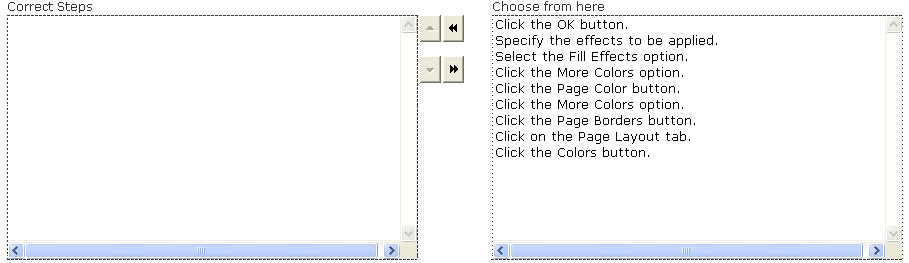
Choose and reorder the steps to apply background in the document.
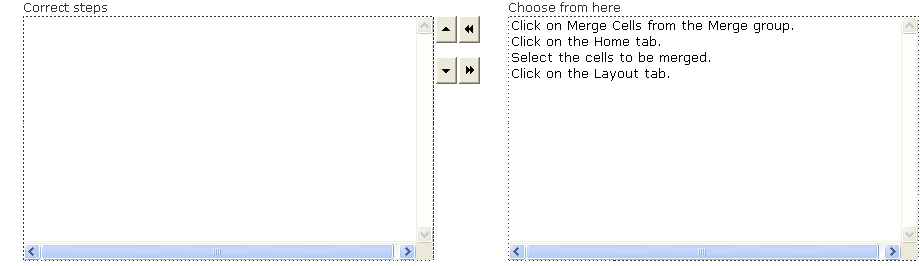
Arrange the steps in the correct order to merge the cells of a table.
which data is changed before or while it is entered into a computer system?
Which of the following is a process in which data is changed before or while it is entered into a
computer system?
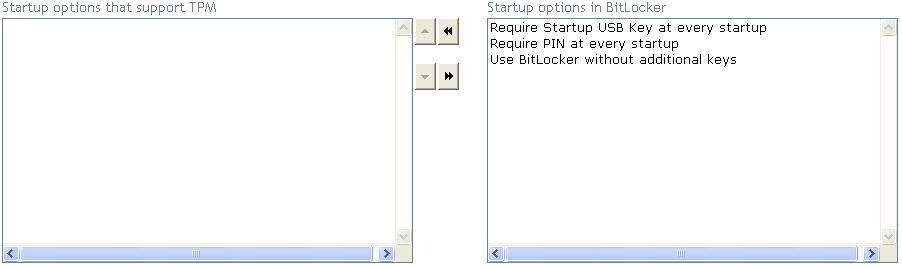
choose the startup options that can be selected if the computer has a built-in TPM chip.
Which of the following contains a tree of domain names?
Which of the following contains a tree of domain names?
Which of the following is the reason of logging by Mark when a user is successfully logged into the system as
Mark works as a Systems Administrator for TechMart Incl. The company has Windows-based
network. Mark has been assigned a project to track who tries to log into the system and the time of
the day at which the attempts occur. He is also required to create a system to track when
confidential files are opened and who is trying to open it. Now, Mark logs when someone is not able
to make a successful attempt to log into the system as Administrator but he also wants to log when
the user is successful to log into the system as Administrator. Which of the following is the reason of
logging by Mark when a user is successfully logged into the system as well as when he is failed?
Which of the following is the basic troubleshooting step that he can ask them to do?
Mark works as a Systems Administrator for TechMart Inc. The company has a Windows-based
network. The company is adding an open, high-speed, wireless access for their customers and
secured wireless for employees at all 37 branches. He wants to check the various security concerns
for ensuring that business traffic is secured. He is also in under pressure to make this new feature a
winning strategy for a company. Mark wants the employees to be free to troubleshoot their own
wireless connections before contacting him. Which of the following is the basic troubleshooting step
that he can ask them to do?
Which of the following protects against unauthorized access to confidential information via encryption and wor
Which of the following protects against unauthorized access to confidential information via
encryption and works at the network layer?