which event log should you select?
HOTSPOT
You are troubleshooting communication issues on a computer that has Windows 8
Enterprise installed. The relevant portion of the computer configuration is displayed in the
exhibit. (Click the Exhibit button.)
You need to find the Windows Firewall service startup and shutdown events. In the Event
Viewer, which event log should you select? (To answer, select the appropriate log in the answer area.)
You need to transfer a 1-gigabit file from Computer1 to Computer2
You need to ensure that the computers can connect to the Internet
A company is setting up a new branch office. You deploy 10 new Windows 8.1 64-bit client
computers in the branch office. The computers cannot connect to the Internet. You run the
ipconfig command on one computer. The following output depicts a portion of the results.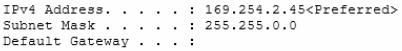
You need to ensure that the computers can connect to the Internet.
What should you do?
Which three actions should you perform in sequence?
DRAG DROP
You are preparing to deploy a new computer that runs Windows 8. You plan to copy the
user’s data from his current computer to the new computer.
You need to generate a list of data that will be copied from his existing computer to the new computer.
Which three actions should you perform in sequence? (To answer, move the appropriate
actions from the list of actions to the answer area and arrange them in the correct order.)
You need to install Windows 7 in a dual-boot configuration
Which two actions should you perform?
You have a workgroup that contains five computers. The computers run Windows 7.
A computer named Computer1 has video and audio files.
You need to share Computer1’s video and audio files on the network.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose
two.)
You need to ensure that you can manage only COMPUTER1 by using WinRS
A company has an Active Directory Domain Services (AD DS) domain. All client computers
are joined to the domain and run Window 8.1. You set up a management computer named COMPUTER1.
You plan to administer COMPUTER1 by using Windows Remote Shell (WinRS) from your
client computer.
You are unable to connect to COMPUTER1 by running the winrs command.
You need to ensure that you can manage only COMPUTER1 by using WinRS.
What should you do?
How do you configure system protection on your D: drive?
Your computer running Windows 7 Enterprise has two internal hard disks.
System protection is configured by default on the C: drive, which holds the operating system and
installed applications.
The D: drive is a 500-GB hard disk formatted with the NTFS filing system, and you use it to store your
personal files.
You want to store previous versions going back several months and therefore intend to reserve 200
GB of this disk for system protection.
You are not using either of your internal disks for backup; instead, you store your backups on a 1-TB
external USB hard disk.
How do you configure system protection on your D: drive? (Choose all that apply; each answer forms
part of the complete solution.)
Which command should you run?
You administer Windows 8.1 client computers in your company network.
A user reports that her Internet connection is slower than usual.
You need to identify the Process Identifiers (PIDs) of applications that are making
connections to the Internet.
Which command should you run?
What do you advise?
An employee who works from home telephones your help desk. A virus attack has deleted his
computer’s single internal hard disk. He carried out a System Image backup on his computer three
months ago and automatically backs up his personal files every night. He uses an external USB hard
drive formatted with the NTFS file system to hold his backups.
All his personal files are in his Documents library. What do you advise? (Choose all that apply; the
answers form a complete solution.)



