Which kind of dynamic volume should you create?
A company has client computers that run Windows 8. Each computer has two hard drives.
You need to create a dynamic volume on each computer that maximizes write performance
with data fault tolerance. Which kind of dynamic volume should you create?
What should you do?
You are the newly appointed network Enterprise Desktop Administrator at Company.com. The
Company.com network client workstations are configured to run Windows 7. The Company.com
network contains a Sales department. Employees in this department share the computers. The
computers are located in an organizational unit (OU) named KingSales. The exhibit below illustrates
the network design of Company.com: You are in the process of planning the deployment of an
application that is packaged as a Microsoft Windows Installer package (MSI). You receive notification
from management to only deploy the application to the computers located in the Sales department.
What should you do? (Choose all that apply.)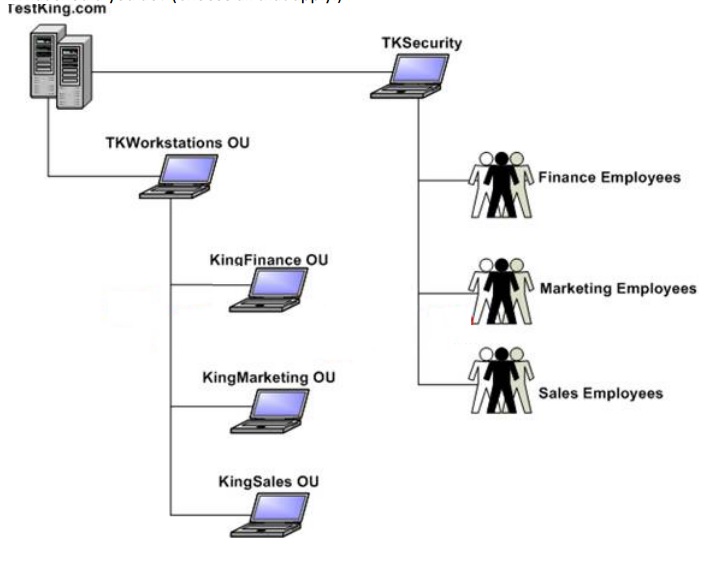
You need to ensure that all computers can locate the LTI deployment shares
You will use Microsoft Deployment Toolkit (MDT) 2010 to perform a Lite Touch Installation (LTI) of
Windows 7 on client computers. You need to ensure that all computers can locate the LTI
deployment shares. What should you do?
You need to add a device driver in the image
You have a Windows Image (WIM) file that contains an image of Windows 7. You need to add a device driver
in the image. You must achieve this goal by using the minimum amount of administrative effort. What should
you do?
You need to minimize the amount of time it takes for branch office users to open files located in the main off
Your network has a main office and a branch office. The branch office has five client computers that
run Windows 7. All servers are located in the main office. All servers have BranchCache enabled.
Users at the branch office report that it takes several minutes to open large files located in the main
office.
You need to minimize the amount of time it takes for branch office users to open files located in the
main office.
The solution must also reduce the amount of bandwidth used between the two offices.
What should you do?
You need to ensure that the application is deployed to all computers in the HRComputers OU as well as ensuring
Company.com has employed you as a network Enterprise Desktop Administrator. The Company.com
network client workstations are configured to run Windows 7. Company.com has its headquarters in
Chicago and branch offices around the globe. A number of users in the Human Resources
department share computers. The computers in this department are located in the HRComputers
organizational unit. You receive an instruction from the CIO to deploy a new application that is not
packaged. You need to ensure that the application is deployed to all computers in the HRComputers
OU as well as ensuring that the application is executed from a central location. You thus need to
propose a plan that will comply with the set requirements. What should you do? (Choose all that
apply.)
You need to create a computer association between the Windows Vista computer and the new computer
Your company uses System Center Configuration Manager 2007 R2 for operating system
deployment. You have a client computer that has Windows Vista installed. You also have a new
computer that does not have an operating system installed. You need to create a computer
association between the Windows Vista computer and the new computer. What should you do first?
You need to ensure that a script runs after the first user logon
You have an image that contains a Windows 7 installation. You need to ensure that a script runs after the first
user logon. What should you do?
Which two authentication methods should you choose?
A company has client computers that run Windows 8.
The company implements the following security requirements:
· All client computers must use two-factor authentication.
· At least one authentication method must include more than four characters or gestures.
You need to choose authentication methods that comply with the security requirements.
Which two authentication methods should you choose? (Each correct answer presents part
of the solution. Choose two.)
You need to ensure that your user account can decrypt all EFS files on the computer
You have a computer that runs Windows 7. You create an Encrypting File System (EFS) recovery key
and certificate.
You need to ensure that your user account can decrypt all EFS files on the computer.
What should you do?

