Which commands should you run?
DRAG DROP
A company has client computers that run Windows 8. All client computers allow incoming
Remote Desktop connections.
You attempt to connect from COMPUTER1 to COMPUTER2 by using Remote Desktop.
Remote Desktop cannot connect to the remote computer. You establish that the firewall
settings on COMPUTER2 have not been set to allow incoming connections.
From COMPUTER1, you need to enable Remote Desktop traffic through Windows Firewall
on COMPUTER2.
Which commands should you run? (To answer, drag the appropriate command or
commands to the correct location or locations in the answer are Commands may be used
once, more than once, or not at all. You may need to drag the split bar between panes or
scroll to view content.)
Which commands should you run?
DRAG DROP
A company has an Active Directory Domain Services (AD DS) domain. All client computers
run Windows 8. Some computers have a Trusted Platform Module (TPM) chip. Members of
the ITStaff security group are part of the local Power Users group on each client computer.
You need to configure a single Group Policy object (GPO) that will allow Windows BitLocker
Drive Encryption on all client computers by using the least amount of privilege necessary.
Which commands should you run? (To answer, drag the appropriate command or
commands to the correct location or locations in the answer are Commands may be used
once, more than once, or not at all. You may need to drag the split bar between panes or
scroll to view content.)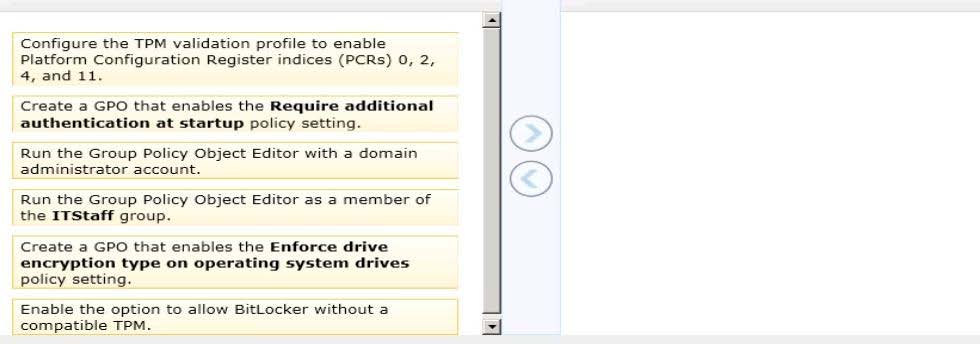
Which commands should you run?
DRAG DROP
A company has an Active Directory Domain Services (AD DS) domain. All client computers
run Windows 8. Two computers named COMPUTER1 and COMPUTER2 are connected to
one network switch and joined to the domain. Windows Firewall is turned off on both
computers.
You are planning a remote management solution. You have the following requirements:
Ensure that COMPUTER1 can run remote commands on COMPUTER2.
Test the solution by successfully running a command from COMPUTER1 that executes on
COMPUTER2.
You need to select the commands to run on COMPUTER1 and COMPUTER2 to meet the
remote management requirements.
Which commands should you run? (To answer, drag the appropriate command or
commands to the correct location or locations in the answer are Commands may be used
once, more than once, or not at all. You may need to drag the split bar between panes or
scroll to view content.)
Which three actions should you perform in sequence?
DRAG DROP
A local printer named PRINTER1 is shared from a client computer named COMPUTER1 that
run a 64-bit version of Windows 8.
The workgroup contains client computers that run a 32-bit version of Windows 8.
Computers in the workgroup can’t currently print to PRINTER1.
You need to ensure that the workgroup computers can print to PRINTER1.
Which three actions should you perform in sequence? (To answer, move the appropriate
actions to the answer area and arrange the correct order.)
Which three actions should you perform in sequence?
DRAG DROP
You have a computer that runs Windows 8, and three unused external disk drives.
You are creating a volume to store picture files. You have the following requirements:
Use all three external disk drives.
Ensure that the volume is accessible from a single drive letter.
Maximize the available space.
You need to create the volume.
Which three actions should you perform in sequence? (To answer, move the appropriate
actions from the list of actions to the answer area and arrange them in the correct order.)
You need to ensure that you can connect to all computers on the network
Your network consists of a single IPv4 subnet. The subnet contains 20 computers that run Windows
7.
You add a new computer named Computer1 to the subnet.
You discover that Computer1 has an IP address of 169.254.34.12.
You cannot connect to other computers on the network. Other computers on the network can
connect to each other.
You need to ensure that you can connect to all computers on the network.
What should you do?
What should you do?
You are employed as the network Enterprise Desktop Administrator at Company.com. The
Company.com network consists of 1,200 client workstations that are configured to run Windows 7.
At present Company.com makes use of various custom line-of-business applications that is
incompatible with Windows 7. During the course of the day you receive an instruction from the CIO
to distribute a Microsoft Enterprise Desktop Virtualization (MED-V) v2 virtual machine (VM) image.
This image encompasses the custom applications to all Windows 7 client workstations. What should you do?
Which file should you modify?
You have a single-domain Active Directory Domain Services (AD DS) forest. All servers run Windows
Server 2008 R2. All client computers run Windows Vista. A custom local security group exists on all
client computers. You are upgrading from Windows Vista to Windows 7. You will use User State
Migration Tool (USMT) 4.0 to migrate user data and settings. You need to migrate user data and
settings while Windows Vista is offline, and you must ensure that the migration includes the custom
local group membership. Which file should you modify?
You need to ensure that a third-party mass storage driver is installed when you deploy Windows 7 by using the
You plan to create an answer file to deploy Windows 7. You need to ensure that a third-party mass storage
driver is installed when you deploy Windows 7 by using the answer file. What should you do?
Which type of record should you request?
Your network consists of an Active Directory domain named contoso.com. You have a computer
named computer1.contoso.com.
Your network is configured to use only IPv6.
You need to request that a DNS record be created to enable users to connect to your computer by
using the name dev.contoso.com.
Which type of record should you request?

