Which permissions should you set?
Your computer runs Windows 8 and is connected to an Active Directory Domain Services
(AD DS) domain.
You create a folder and share the folder with everyone in your organization.
You need to modify the NTFS permissions of the folder to meet the following criteria:
Users from the Supervisors AD security group must be able to open files, but not modify
them.
Users from the Marketing AD security group must be able to create, modify, and delete files.
Users from both groups must not be able to delete the folder.
Which permissions should you set?
You need to verify that the client laptops and tablets support Virtual Smart Cards
You are an IT consultant for small and mid-sized businesses. One of your clients wants to start using
Virtual Smart Cards on its laptops and tablets, which run Windows 8 Pro. Before implementing any
changes, the client wants to ensure that the laptops and tablets support Virtual Smart Cards. You
need to verify that the client laptops and tablets support Virtual Smart Cards. What should you do?
Which command should you run before you capture the image?
You have a reference computer that runs Windows 7.
You plan to deploy an image of the computer. You create an answer file named answer.xml.
You need to ensure that the installation applies the answer file after you deploy the image.
Which command should you run before you capture the image?
What should you do?
You are the newly appointed enterprise administrator at Company.com. The Company.com network
consists of two Active Directory domains. These domains have a two-way trust relationship. The
users in the domain can only log onto their client workstations in their respective domains. However,
during a routine monitoring you notice that the domain controllers display the following error
message stating that the clock skew is too great. You check and discover that it occur when the users
in one domain log on to the client workstations in the other domain. You have received instructions
from the CIO to make sure that the users in both domains is able to log onto each other’s client
workstations in any domain at Company.com. What should you do?
Which command should you run?
You have a single-domain Active Directory Domain Services (AD DS) forest. All servers run Windows
Server 2008. All client computers run Windows 7. You use Microsoft Deployment Toolkit (MDT) 2010
for your deployment infrastructure. You need to configure your deployment infrastructure to use
single-instance storage. Which command should you run?
You need to ensure that every time you capture an image by using ImageX, all ISO files are excluded from the W
You need to ensure that every time you capture an image by using ImageX, all ISO files are excluded from the
Windows Image (WIM) file. What should you do?
You need to ensure that only approved apps can be installed from Windows Store
You support computers that run Windows 8 Enterprise and are members of a workgroup. Users are
able to download and install any app from Windows Store. You need to ensure that only approved
apps can be installed from Windows Store. What should you do?
You need to start the computer from the VHD
You have a Virtual Hard Disk (VHD) and a computer that runs Windows 7. The VHD has Windows 7 installed.
You need to start the computer from the VHD.
What should you do?
You need to ensure that the application is blocked from running on all computers and the AppLocker rule is app
A company has an Active Directory Domain Services (AD DS) domain. All client computers
run Windows Vista and are members of the domain. A Group Policy object (GPO)
configuring a software restriction policy is implemented in the domain to block a specific
application.
You upgrade a computer to Windows 8 and implement a GPO that configures an AppLocker
rule in the domain. The blocked application runs on the Windows 8 computer but not on the
Windows Vista computers.
You need to ensure that the application is blocked from running on all computers and the
AppLocker rule is applied to the computers in the domain.
What should you do?
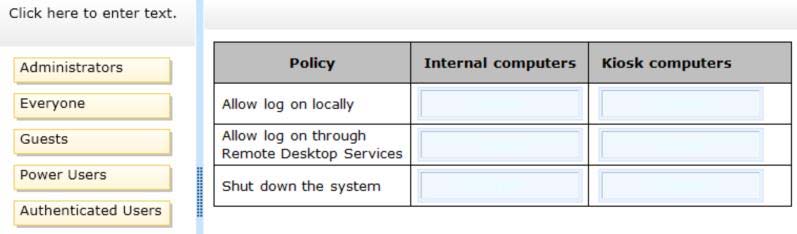
You need to assign security groups to local security policies to meet the requirements
DRAG DROP
A company has 50 client computers that run Windows 8. Forty client computers are
connected to a secure internal network, and 10 client computers are located in public kiosks.
A new company security policy includes the following requirements:
Visitors can access only kiosk computers.
Employees can access and shut down only internal computers.
Only administrators can access all computers remotely.
Only administrators can shut down kiosk computers.
You need to assign security groups to local security policies to meet the requirements.
What should you do? (To answer, drag the appropriate security group or groups to the
correct location or locations in the answer area. Security groups may be used once, more
than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)