You need to ensure that you can access network resources from the reference computer
You have a reference computer that runs Windows 7. You connect the computer to your deployment network.
You notice that you cannot connect to network resources. You run ipconfig as shown in the exhibit. (Click the
Exhibit button.) Other computers in the deployment network can access network resources. You need to
ensure that you can access network resources from the reference computer. What should you do?
You need to roll back the driver to the previous version
A company has client computers that run Windows 8.
You attempt to roll back a driver for a specific device on a client computer.
The Roll Back Driver button is unavailable in Device Manager.
You need to roll back the driver to the previous version.
What should you do first?
You need to ensure an alphanumeric password is required on all Windows 8 tablets
You administer Windows 8 Pro and Windows RT tablets for your company. Your company network
includes a Windows Server 2012 domain and Microsoft Exchange 2010 with ActiveSync and Outlook
Web Access. Users will be using the tablets outside of the corporate network. The Microsoft
Exchange ActiveSync policy is configured to require an alphanumeric password. You need to ensure
an alphanumeric password is required on all Windows 8 tablets. What should you do?
You need to export the user state and the settings of the custom application
You have a computer that runs Windows Vista. The computer contains a custom application.
You need to export the user state and the settings of the custom application.
What should you do?
What should you do?
You work as the network Enterprise Desktop Administrator at Company.com. The Company.com
network has an Active Directory Domain Services (AD DS) domain named Company.com. The
Company.com network client workstations currently make use of Microsoft Windows 7. During the
course of the day you receive instruction from Company.com to start planning for the deployment of
a custom application whilst scheduling the deployment to occur outside business hours with no user
intervention. What should you do?
You need to find out whether any currently installed applications or add-ins interact with Office
Your company’s client computers run Windows XP and Office 2003.
You are migrating all the client computers to Windows 7 and Office 2010.
You need to find out whether any currently installed applications or add-ins interact with Office.
What should you use?
What file should you create in the Windows PE image?
You need to ensure that multiple applications automatically run when you start a computer by using Windows
Preinstallation Environment (Windows PE). What file should you create in the Windows PE image?
You need to meet the requirements
A company has an Active Directory Domain Services (AD DS) domain with one physical
domain controller. All client computers run Windows 8.
A client computer hosts a Windows 8 virtual machine (VM) test environment. The VMs are
connected to a private virtual switch that is configured as shown in the Virtual Switch
Manager exhibit. (Click the Exhibit button.)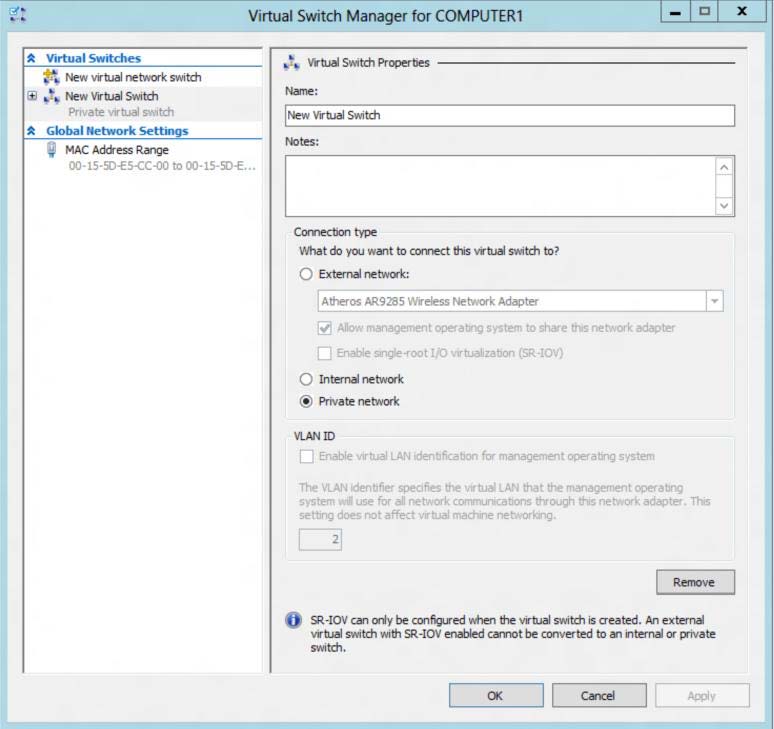
You have the following requirements:
Configure the test environment to allow VMs to communicate with the host machine.
Minimize impact on the host machine.
You need to meet the requirements.
What should you do?
You need to deploy the new application to the tablets
You support desktop computers and tablets that run Windows 8. Domain joined computers are able
to connect to your company network from the Internet by using DirectAccess. Your company wants
to deploy a new application to the tablets. The deployment solution must meet the following
requirements:
• The application is installed locally on the tablets.
• The application installation is hosted in a public cloud.
• The installation must support Windows RT.
You need to deploy the new application to the tablets.
What should you do?
You need to ensure that each access to the folder is logged
You have a computer that runs Windows 7.
Multiple users log on to your computer.
You enable auditing on a folder stored on your computer.
You need to ensure that each access to the folder is logged.
What should you do?

