Which three actions should you perform in sequence?
DRAG DROP
A company has a branch office with client computers that run Windows 8. Files are saved
locally on the client computers and are not backed up regularly.
You need to ensure that you can retrieve previous versions of locally saved files from each
client computer.
Which three actions should you perform in sequence? (To answer, move the appropriate
actions from the list of actions to the answer area and arrange them in the correct order.)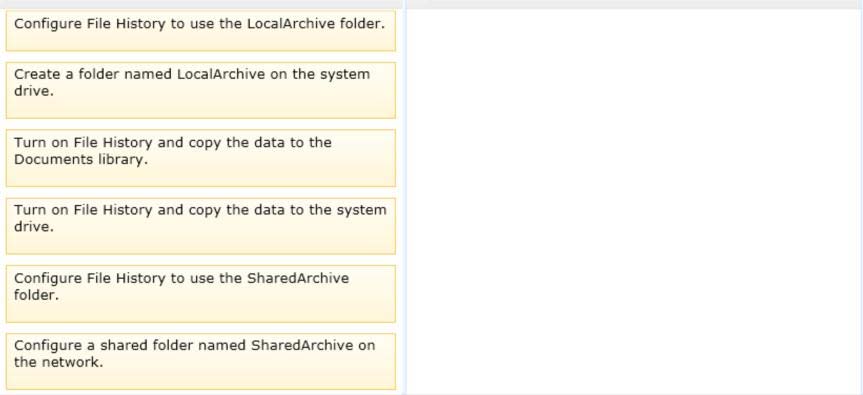
Which two actions should you perform?
You administer computers that run Windows 8 Enterprise and are members of an Active Directory
domain. Some volumes on the computers are encrypted with BitLOcker. The BitLocker recovery
passwords are stored in Active Directory. A user forgets the BitLocker password to local drive E: and
is unable to access the protected volume. You need to provide a BitLocker recovery key to unlock the
protected volume. Which two actions should you perform? (Each correct answer presents part of
the solution. Choose two.)
Which three actions should you perform in sequence?
DRAG DROP
You administer desktop computers in your company’s research department. The computers run
Windows 8 Enterprise and are members of a workgroup. A new security policy states that all traffic
between computers in the research department must be encrypted and authenticated. You need to
configure the requested traffic authentication settings by using Windows Firewall with Advanced
Security. Which three actions should you perform in sequence? (To answer, move the appropriate
actions from the list of actions to the answer area and arrange them in the correct order.)
You need to identify how much space is required to complete the migration
You have a computer named Computer1 that runs Windows Vista and a computer named
Computer2 that runs Windows 7. You plan to migrate all profiles and user files from Computer1 to Computer2.
You need to identify how much space is required to complete the migration.
What should you do?
What should you do?
You work as the network Enterprise Desktop Administrator at Company.com. The Company.com
network has an Active Directory Domain Services (AD DS) domain named Company.com. The
Company.com network client workstations currently make use of Microsoft Windows Vista. The
Company.com client workstations hardware configuration is shown in the table below: During the
course of the day you receive instruction from Company.com to have Microsoft Windows 7
deployed to the client workstations using the least amount of images. What should you do?
You need to ensure that the .wxv files are migrated with all NTFS permissions intact.What should you do?
Your company has a single-domain Active Directory Domain Services (AD DS) forest. All client
computers run Windows Vista. You are migrating all client computers to Windows 7 by using User
State Migration Tool (USMT) 4.0. You perform several test migrations. You discover that a set of files
with the extension .wxv, which should be restricted by NTFS permissions, were accessible to all users
after the test migrations were completed. You need to ensure that the .wxv files are migrated with
all NTFS permissions intact.What should you do?
Which tool should you use?
You deploy an image to a computer. You start the computer. You notice that it takes longer than expected to
access the user desktop. You need to identify the cause of the delay. Which tool should you use?
Which two actions should you perform?
You have a desktop computer that runs Windows 8 Enterprise. You add three new 3-terabyte disks.
You need to create a new 9-terabyte volume. Which two actions should you perform? (Each correct
answer presents part of the solution. Choose two.)
What should you do?
You work in an international company which is named Wiikigo. Before entering this company, you
have two years of experience in the IT field, as well as experience implementing and administering
any Windows client operating system in a networked environment.
You are professional in installing, upgrading and migrating to Windows 7, deploying Windows 7, and
configuring Hardware and Applications and son on.
You have a workgroup which contains five computers. Windows 7 is run by the computers. A
computer named C01 has video and audio files.
You have to share C01s video and audio files on the network.
What should you do? (Choose more than one)
Which two command-line tools should you use?
A company has client computers that run Windows 8. Each employee has one client
computer at the office. Some employees also have personal computers at home.
The company has applications that run only on Windows 8.
You need to deploy Windows To Go so that employees can run the applications on their
home computers.
Which two command-line tools should you use? (Each correct answer presents part of the
solution. Choose two.)

