You need to verify that the client laptops and tablets support Virtual Smart Cards
You are an IT consultant for small and mid-sized businesses.
One of your clients wants to start using Virtual Smart Cards on its laptops and tablets, which
run Windows 8 Pro. Before implementing any changes, the client wants to ensure that the
laptops and tablets support Virtual Smart Cards.
You need to verify that the client laptops and tablets support Virtual Smart Cards.
What should you do?
Which three actions should you perform in sequence on the computer?
DRAG DROP
You administer computers and printers on your company network. The computers run Window 8 Pro.
An employee wants to add a separator page to her printer task on a network printer. You
create a separator page file and save it to the C:\Windows\System32 folder on her computer.
You need to configure the computer to use the separator page for the print task.
Which three actions should you perform in sequence on the computer? (To answer, move
the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)
What permission should you identify?
You have a computer that runs Windows 8.
The computer has a shared folder named C:\Marketing. The shared folder is on an NTFS volume.
The current NTFS and share permissions are configured as follows: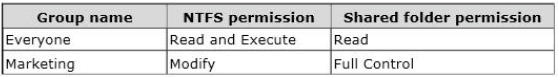
UserA is a member of both the Everyone group and the Marketing group. UserA must
access C:\Marketing from across the network.
You need to identify the effective permissions of UserA to the C:\Marketing folder.
What permission should you identify?
What should you configure on the laptops?
You administer laptops that run Windows 8 Enterprise. The laptops are members of an
Active Directory domain and are configured with IPv6 disabled.
Some users require access to the internal company database servers while traveling.
You need to configure the requested network connection to the database servers.
What should you configure on the laptops?
Which three actions should you perform in sequence?
DRAG DROP
You support a desktop computer that runs Windows 8 Pro. The computer is joined to an
Active Directory domain.
The computer has a folder named C:\Reports. The folder NTFS permissions are shown in
Exhibit 1. (Click the Exhibit button.)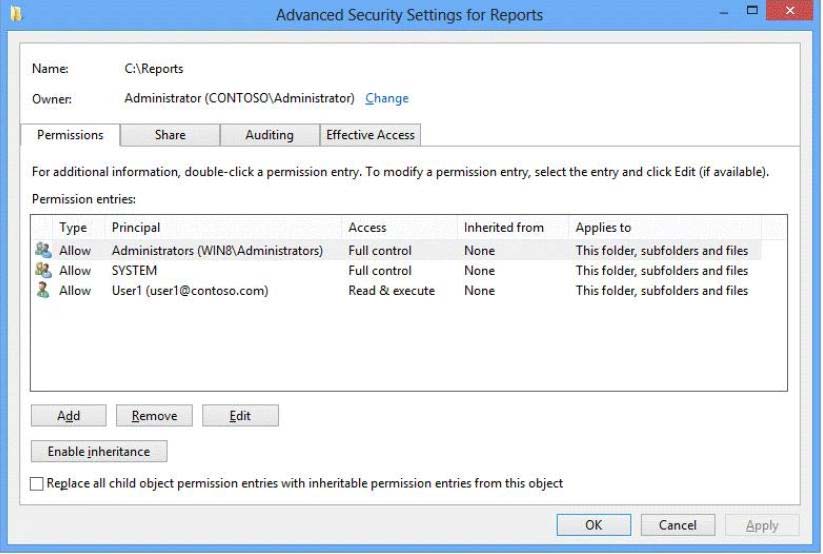
The folder is shared over the network with Read permission for a domain user account
named User1 as shown in Exhibit 2. (Click the Exhibit button.)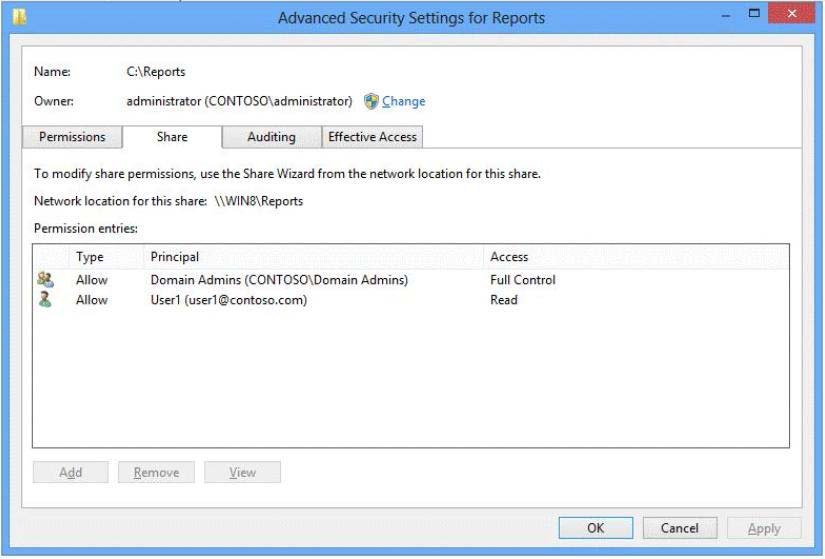
Members of the domain security group named Accountants must have access to the shared folder.
You need to assign the required permissions.
Which three actions should you perform in sequence? (To answer, move the appropriate
actions from the list of actions to the answer area and arrange them in the correct order.)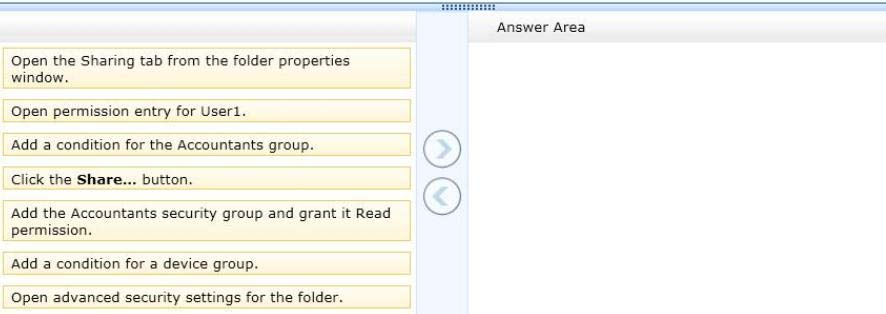
Which two actions should you perform?
You have a desktop computer that runs Windows 8 Enterprise.
You add three new 3-terabyte disks.
You need to create a new 9-terabyte volume.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
You need to configure the computers to meet this requirement
You administer laptop and desktop computers that run Windows 8 Pro. Your company uses
Active Directory Domain Services (AD DS) and Active Directory Certificate Services (AD
CS).
Your company decides that access to the company network for all users must be controlled
by two-factor authentication.
You need to configure the computers to meet this requirement.
What should you do?
Which two actions should you perform?
You administer computers that run Windows 8 Enterprise and are members of an Active
Directory domain.
Some volumes on the computers are encrypted with BitLocker. The BitLocker recovery
passwords are stored in Active Directory. A user forgets the BitLocker password to local
drive E: and is unable to access the protected volume.
You need to provide a BitLocker recovery key to unlock the protected volume.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
You need to manage Active Directory from the tablet by using a VPN connection
You administer computers that run Windows 8 Enterprise. The computers are members of
an Active Directory domain.
You have a tablet that runs Windows 8 Enterprise. You configure the tablet to access your
company network by using a virtual private network (VPN) connection.
You need to manage Active Directory from the tablet by using a VPN connection.
What should you do?
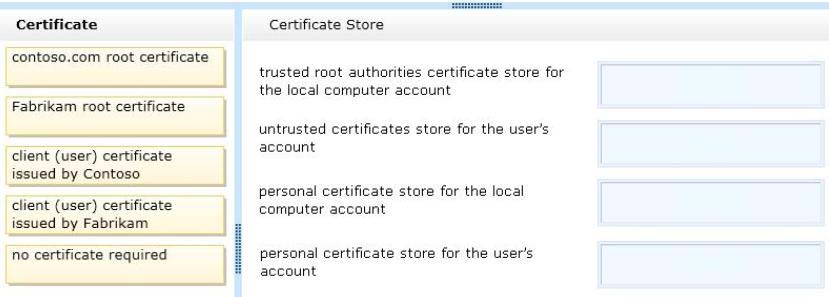
Which certificate or certificates should you use?
DRAG DROP
You support desktop computers for a company named Fabrikam, Inc. The computers are
members of the Active Directory domain named fabrikam.com.
Fabrikam works with a supplier named Contoso, Ltd. Each company has a public key
infrastructure (PKI), and no public certificate authorities (CAs) are used. Fabrikam
employees regularly use a Contoso website that is hosted on a server in the contoso.com
domain. The website requires SSL and mutual authentication.
You need to configure the computers to allow Fabrikam users to access the Contoso
website without any warning prompts. You also need to use the fewest certificates
possible.
Which certificate or certificates should you use? (To answer, drag the appropriate
certificate to the correct certificate store. Each certificate may be used once, more than
once, or not at all. You may need to drag the split bar between panes or scroll to view content.)