Which two audit policies should you configure in GPO1?
HOTSPOT
Your network contains an Active Directory domain named contoso.com.
You create an organizational unit (OU) named OU1 and a Group Policy object (GPO) named GPO1. You link
GPO1 to OU1.
You move several file servers that store sensitive company documents to OU1. Each file server contains more
than 40 shared folders.
You need to audit all of the failed attempts to access the files on the file servers in OU1. The solution must
minimize administrative effort.
Which two audit policies should you configure in GPO1?
To answer, select the appropriate two objects in the answer area.
Your network contains an Active Directory domain named contoso.com…
HOTSPOT
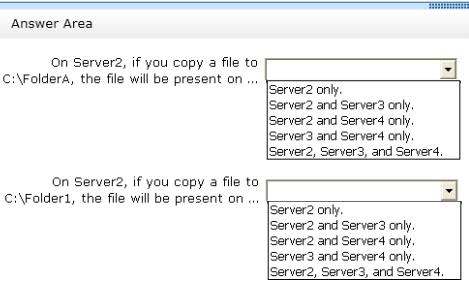
Your network contains an Active Directory domain named contoso.com. The domain contains three servers
named Server2, Server3, and Server4.
Server2 and Server4 host a Distributed File System (DFS) namespace named Namespace1.
You open the DFS Management console as shown in the exhibit. (Click the Exhibit button.)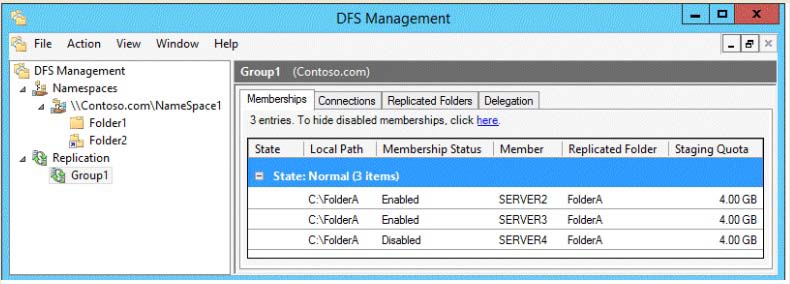
To answer, complete each statement according to the information presented in the exhibit. Each correct
selection is worth one point.
which server should you deploy the feature?
Your network contains an Active Directory domain named contoso.com. The domain contains five servers. The
servers are configured as shown in the following table.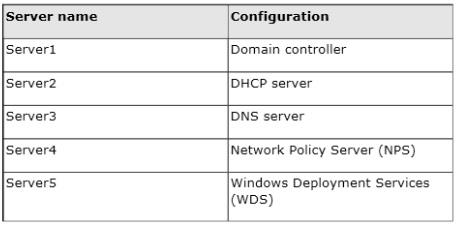
All desktop computers in contoso.com run Windows 8 and are configured to use BitLocker Drive Encryption
(BitLocker) on all local disk drives.
You need to deploy the Network Unlock feature. The solution must minimize the number of features and
server roles installed on the network.
To which server should you deploy the feature?
What should you configure on Server1?
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the File Server Resource
Manager role service installed.
Server1 has a folder named Folder1 that is used by the human resources department.
You need to ensure that an email notification is sent immediately to the human resources manager when a
user copies an audio file or a video file to Folder1.
What should you configure on Server1?
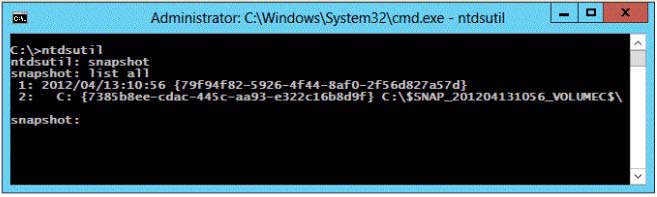
You need to ensure that you can access the contents of the mounted snapshot
You need to provide the members of RODC_Admins with the ability to manage the hardware and the software on R0D
Your network contains an Active Directory domain named contoso.com. The domain contains a read-only
domain controller (RODC) named R0DC1.
You create a global group named RODC_Admins.
You need to provide the members of RODC_Admins with the ability to manage the hardware and the software
on R0DC1. The solution must not provide RODC_Admins with the ability to manage Active Directory objects.
What should you do?
What should you identify?
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains 30 user accounts
that are used for network administration. The user accounts are members of a domain global group named
Group1.
You identify the security requirements for the 30 user accounts as shown in the following table.
You need to identify which settings must be implemented by using a Password Settings object (PSO) and which
settings must be implemented by modifying the properties of the user accounts.
What should you identify?
To answer, configure the appropriate settings in the dialog box in the answer area.
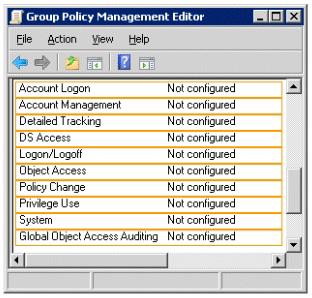
Which two auditing policies should you configure?
HOTSPOT
Your network contains 25 Web servers that run Windows Server 2012 R2.
You need to configure auditing policies that meet the following requirements:
Generate an event each time a new process is created.
Generate an event each time a user attempts to access a file share.
Which two auditing policies should you configure?
To answer, select the appropriate two auditing policies in the answer area.
Which Cryptography setting of the certificate template should you modify?
HOTSPOT
Your network contains an Active Directory domain named contoso.com.
You need to create a certificate template for the BitLocker Drive Encryption (BitLocker) Network Unlock
feature.
Which Cryptography setting of the certificate template should you modify?
To answer, select the appropriate setting in the answer area.
Which command should you run?
Your network contains an Active Directory domain named contoso.com. The domain contains a virtual
machine named Server1 that runs Windows Server 2012 R2.
Server1 has a dynamically expanding virtual hard disk that is mounted to drive E.
You need to ensure that you can enable BitLocker Drive Encryption (BitLocker) on drive E.
Which command should you run?