Which Advanced Boot Option should you select?
You have a server named Server1 that runs Windows Server 2012 R2 and is used for
testing.
A developer at your company creates and installs an unsigned kernel-mode driver on
Server1. The developer reports that Server1 will no longer start.
You need to ensure that the developer can test the new driver.
The solution must minimize the amount of data loss.
Which Advanced Boot Option should you select?
Which tool should you use?
You have a server named Server1 that runs Windows Server 2012 R2.
When you install a custom Application on Server1 and restart the server, you receive the
following error message: “The Boot Configuration Data file is missing some required
information.
File: \Boot\BCD
Error code: 0x0000034.”
You start Server1 by using Windows PE.
You need to ensure that you can start Windows Server 2012 R2 on Server1.
Which tool should you use?
How should you configure the UM dial plan?
###BeginCaseStudy###
Case Study: 4
Trey Research
Overview
General Overview
Trey Research is a brokerage firm that has 5,000 users. Trey Research has a
finance department, a human resources department, an investment department, and
a legal department.
Trey Research is acquiring a partner company named Fabrikam, Inc.
Physical Locations
Trey Research has four main offices located in Boston, Chicago, New York, and
Atlanta.
The offices connect to each other by using a WAN link. The Chicago office connects
directly to the Internet.
Existing Environment
Network Environment
Trey Research has an Active Directory forest named treyresearch.com. The forest
contains a single domain. All domain controllers run Windows Server 2012.
Each office is configured as an Active Directory site.
All user accounts are in an organizational unit (OU) based on their department. All
users are in a universal security group based on their department.
Trey Research has a Lync Server 2013 infrastructure. The infrastructure is
configured to required encryption for voice traffic.
Exchange Server Organization
Trey Research has an Exchange Server organization that contains five servers. The
servers are configured as shown in the following table.
The mailbox databases are mounted on the Exchange servers shown in the
following table.
All of the mailboxes of the users in the executives department are mounted on DB3.
A public folder database named PF1 is mounted on EX5.
The Exchange Server organization has the following configurations:
Users in the legal department use a shared mailbox named Legal. Legal is enabled
for In-Place Hold. Legal is the only mailbox on DB2.
All inbound and outbound email messages to and from the Internet are routed
through EX1.
Email messages sent and received by Fabrikam are secured by using Mutual TLS.
All public folders are stored in PF1.
All users connect to their mailbox by using Microsoft Outlook 2013 and Outlook Web
App.
Fabrikam has an Exchange Server 2013 organization.
Problem Statements
Trey Research identifies the following issues:
After a change to a certificate, users report that email messages sent to Fabrikam
are not delivered.
The storage for DB3 fails. The storage will be offline for the next two days.
Requirements
Planned Changes
Trey Research plans to implement the following changes:
Move all public folders to an Exchange Server 2013 server. The solution must
ensure that all users cannot modify the public folders stored on EX5 after the
planned move.
Integrate Unified Messaging (UM) services with the Lync Server 2013 infrastructure.
Collaboration Requirements
Custom recipient MailTips created in the Exchange Server organization of Trey
Research must be visible to the users at Fabrikam. The solution must ensure that
administrators can define a subset of users who can share their MailTips.
Auditing Requirements
The following actions must be audited for actions in the Legal mailbox only:
Delegate – Purge mailbox content
Delegate – Transfer file between folders
Administrator – Messages sent by administrator
Administrator – Open any content within the mailbox
Security Requirements
Trey Research identifies the following security requirements:
Ensure that the users in the finance department can protect email messages from
being altered in transit, regardless of the recipient.
Prevent the email messages sent to the users in the human resources department
from being forwarded to external recipients.
Prevent the audio files in voice mail message marked as Private from being
extracted from email messages.
Redirect email messages that contain social security information to the legal
department.
Compliance Requirements
Trey Research identifies the following compliance requirements:
All users must be notified before they send an email message that contains any five
bank account numbers to an external recipient. The users must be able to override
the requirement if they have a valid business reason to send the email message.
Users must use a custom message classification when they send email messages
that contain information about the planned acquisition of Fabrikam.
1 Only the users in the legal department must be able to use eDiscovery to view the
contents of email messages sent by the finance department users.
###EndCaseStudy###
How should you configure the UM dial plan? (To answer, select the appropriate dial plan type and
VoIP security mode in the answer area.)
You need to ensure that multiple backup copies are maintained
You have a server named Server1 that runs Windows Server 2012 R2.
Server1 is backed up by using Windows Server Backup. The backup configuration is shown
in the exhibit. (Click the Exhibit button.)
You discover that only the last copy of the backup is maintained.
You need to ensure that multiple backup copies are maintained.
What should you do?
Which three actions should you perform?
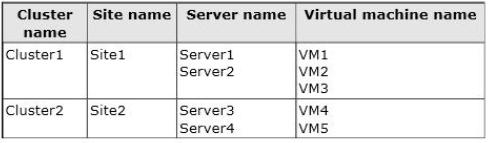
Your network contains an Active Directory domain named contoso.com. The domain
contains four servers named Server1, Server2, Server3, and Server4 that run Windows
Server 2012 R2. All servers have the Hyper-V server role and the Failover Clustering feature
installed.
You need to replicate virtual machines from Cluster1 to Cluster2.
Which three actions should you perform? (Each correct answer presents part of the solution.
Choose three.)
which directory on EX1 should you review the log files?
###BeginCaseStudy###
Case Study: 4
Trey Research
Overview
General Overview
Trey Research is a brokerage firm that has 5,000 users. Trey Research has a
finance department, a human resources department, an investment department, and
a legal department.
Trey Research is acquiring a partner company named Fabrikam, Inc.
Physical Locations
Trey Research has four main offices located in Boston, Chicago, New York, and
Atlanta.
The offices connect to each other by using a WAN link. The Chicago office connects
directly to the Internet.
Existing Environment
Network Environment
Trey Research has an Active Directory forest named treyresearch.com. The forest
contains a single domain. All domain controllers run Windows Server 2012.
Each office is configured as an Active Directory site.
All user accounts are in an organizational unit (OU) based on their department. All
users are in a universal security group based on their department.
Trey Research has a Lync Server 2013 infrastructure. The infrastructure is
configured to required encryption for voice traffic.
Exchange Server Organization
Trey Research has an Exchange Server organization that contains five servers. The
servers are configured as shown in the following table.
The mailbox databases are mounted on the Exchange servers shown in the
following table.
All of the mailboxes of the users in the executives department are mounted on DB3.
A public folder database named PF1 is mounted on EX5.
The Exchange Server organization has the following configurations:
Users in the legal department use a shared mailbox named Legal. Legal is enabled
for In-Place Hold. Legal is the only mailbox on DB2.
All inbound and outbound email messages to and from the Internet are routed
through EX1.
Email messages sent and received by Fabrikam are secured by using Mutual TLS.
All public folders are stored in PF1.
All users connect to their mailbox by using Microsoft Outlook 2013 and Outlook Web
App.
Fabrikam has an Exchange Server 2013 organization.
Problem Statements
Trey Research identifies the following issues:
After a change to a certificate, users report that email messages sent to Fabrikam
are not delivered.
The storage for DB3 fails. The storage will be offline for the next two days.
Requirements
Planned Changes
Trey Research plans to implement the following changes:
Move all public folders to an Exchange Server 2013 server. The solution must
ensure that all users cannot modify the public folders stored on EX5 after the
planned move.
Integrate Unified Messaging (UM) services with the Lync Server 2013 infrastructure.
Collaboration Requirements
Custom recipient MailTips created in the Exchange Server organization of Trey
Research must be visible to the users at Fabrikam. The solution must ensure that
administrators can define a subset of users who can share their MailTips.
Auditing Requirements
The following actions must be audited for actions in the Legal mailbox only:
Delegate – Purge mailbox content
Delegate – Transfer file between folders
Administrator – Messages sent by administrator
Administrator – Open any content within the mailbox
Security Requirements
Trey Research identifies the following security requirements:
Ensure that the users in the finance department can protect email messages from
being altered in transit, regardless of the recipient.
Prevent the email messages sent to the users in the human resources department
from being forwarded to external recipients.
Prevent the audio files in voice mail message marked as Private from being
extracted from email messages.
Redirect email messages that contain social security information to the legal
department.
Compliance Requirements
Trey Research identifies the following compliance requirements:
All users must be notified before they send an email message that contains any five
bank account numbers to an external recipient. The users must be able to override
the requirement if they have a valid business reason to send the email message.
Users must use a custom message classification when they send email messages
that contain information about the planned acquisition of Fabrikam.
1 Only the users in the legal department must be able to use eDiscovery to view the
contents of email messages sent by the finance department users.
###EndCaseStudy###
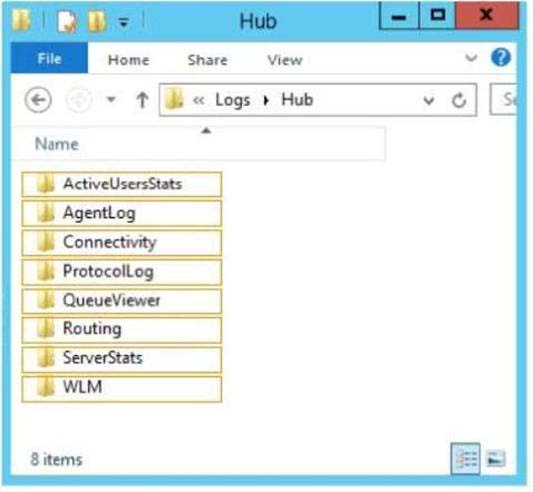
HOTSPOT
You are attempting to resolve the email delivery issue for Fabrikam.
You need to identify which certificate is being used by the servers in the Exchange Server
organization of Fabrikam.
In which directory on EX1 should you review the log files? (To answer, select the appropriate
directory in the answer area.)
You need to perform a bare-metal recovery of Server1 by using the Windows Recovery Environment (Windows RE)
You have a server named Server1 that runs Windows Server 2012 R2.
Each day, Server1 is backed up fully to an external disk.
On Server1, the disk that contains the operating system fails.
You replace the failed disk.
You need to perform a bare-metal recovery of Server1 by using the Windows Recovery
Environment (Windows RE).
What should you do?
Which two cmdlets should you use?
###BeginCaseStudy###
Case Study: 4
Trey Research
Overview
General Overview
Trey Research is a brokerage firm that has 5,000 users. Trey Research has a
finance department, a human resources department, an investment department, and
a legal department.
Trey Research is acquiring a partner company named Fabrikam, Inc.
Physical Locations
Trey Research has four main offices located in Boston, Chicago, New York, and
Atlanta.
The offices connect to each other by using a WAN link. The Chicago office connects
directly to the Internet.
Existing Environment
Network Environment
Trey Research has an Active Directory forest named treyresearch.com. The forest
contains a single domain. All domain controllers run Windows Server 2012.
Each office is configured as an Active Directory site.
All user accounts are in an organizational unit (OU) based on their department. All
users are in a universal security group based on their department.
Trey Research has a Lync Server 2013 infrastructure. The infrastructure is
configured to required encryption for voice traffic.
Exchange Server Organization
Trey Research has an Exchange Server organization that contains five servers. The
servers are configured as shown in the following table.
The mailbox databases are mounted on the Exchange servers shown in the
following table.
All of the mailboxes of the users in the executives department are mounted on DB3.
A public folder database named PF1 is mounted on EX5.
The Exchange Server organization has the following configurations:
Users in the legal department use a shared mailbox named Legal. Legal is enabled
for In-Place Hold. Legal is the only mailbox on DB2.
All inbound and outbound email messages to and from the Internet are routed
through EX1.
Email messages sent and received by Fabrikam are secured by using Mutual TLS.
All public folders are stored in PF1.
All users connect to their mailbox by using Microsoft Outlook 2013 and Outlook Web
App.
Fabrikam has an Exchange Server 2013 organization.
Problem Statements
Trey Research identifies the following issues:
After a change to a certificate, users report that email messages sent to Fabrikam
are not delivered.
The storage for DB3 fails. The storage will be offline for the next two days.
Requirements
Planned Changes
Trey Research plans to implement the following changes:
Move all public folders to an Exchange Server 2013 server. The solution must
ensure that all users cannot modify the public folders stored on EX5 after the
planned move.
Integrate Unified Messaging (UM) services with the Lync Server 2013 infrastructure.
Collaboration Requirements
Custom recipient MailTips created in the Exchange Server organization of Trey
Research must be visible to the users at Fabrikam. The solution must ensure that
administrators can define a subset of users who can share their MailTips.
Auditing Requirements
The following actions must be audited for actions in the Legal mailbox only:
Delegate – Purge mailbox content
Delegate – Transfer file between folders
Administrator – Messages sent by administrator
Administrator – Open any content within the mailbox
Security Requirements
Trey Research identifies the following security requirements:
Ensure that the users in the finance department can protect email messages from
being altered in transit, regardless of the recipient.
Prevent the email messages sent to the users in the human resources department
from being forwarded to external recipients.
Prevent the audio files in voice mail message marked as Private from being
extracted from email messages.
Redirect email messages that contain social security information to the legal
department.
Compliance Requirements
Trey Research identifies the following compliance requirements:
All users must be notified before they send an email message that contains any five
bank account numbers to an external recipient. The users must be able to override
the requirement if they have a valid business reason to send the email message.
Users must use a custom message classification when they send email messages
that contain information about the planned acquisition of Fabrikam.
1 Only the users in the legal department must be able to use eDiscovery to view the
contents of email messages sent by the finance department users.
###EndCaseStudy###
You need to implement a solution that meets the compliance requirements for the members of the
legal department.
Which two cmdlets should you use? (Each correct answer presents part of the solution. Choose two.)
Which three actions should you perform in sequence?
###BeginCaseStudy###
Case Study: 4
Trey Research
Overview
General Overview
Trey Research is a brokerage firm that has 5,000 users. Trey Research has a
finance department, a human resources department, an investment department, and
a legal department.
Trey Research is acquiring a partner company named Fabrikam, Inc.
Physical Locations
Trey Research has four main offices located in Boston, Chicago, New York, and
Atlanta.
The offices connect to each other by using a WAN link. The Chicago office connects
directly to the Internet.
Existing Environment
Network Environment
Trey Research has an Active Directory forest named treyresearch.com. The forest
contains a single domain. All domain controllers run Windows Server 2012.
Each office is configured as an Active Directory site.
All user accounts are in an organizational unit (OU) based on their department. All
users are in a universal security group based on their department.
Trey Research has a Lync Server 2013 infrastructure. The infrastructure is
configured to required encryption for voice traffic.
Exchange Server Organization
Trey Research has an Exchange Server organization that contains five servers. The
servers are configured as shown in the following table.
The mailbox databases are mounted on the Exchange servers shown in the
following table.
All of the mailboxes of the users in the executives department are mounted on DB3.
A public folder database named PF1 is mounted on EX5.
The Exchange Server organization has the following configurations:
Users in the legal department use a shared mailbox named Legal. Legal is enabled
for In-Place Hold. Legal is the only mailbox on DB2.
All inbound and outbound email messages to and from the Internet are routed
through EX1.
Email messages sent and received by Fabrikam are secured by using Mutual TLS.
All public folders are stored in PF1.
All users connect to their mailbox by using Microsoft Outlook 2013 and Outlook Web
App.
Fabrikam has an Exchange Server 2013 organization.
Problem Statements
Trey Research identifies the following issues:
After a change to a certificate, users report that email messages sent to Fabrikam
are not delivered.
The storage for DB3 fails. The storage will be offline for the next two days.
Requirements
Planned Changes
Trey Research plans to implement the following changes:
Move all public folders to an Exchange Server 2013 server. The solution must
ensure that all users cannot modify the public folders stored on EX5 after the
planned move.
Integrate Unified Messaging (UM) services with the Lync Server 2013 infrastructure.
Collaboration Requirements
Custom recipient MailTips created in the Exchange Server organization of Trey
Research must be visible to the users at Fabrikam. The solution must ensure that
administrators can define a subset of users who can share their MailTips.
Auditing Requirements
The following actions must be audited for actions in the Legal mailbox only:
Delegate – Purge mailbox content
Delegate – Transfer file between folders
Administrator – Messages sent by administrator
Administrator – Open any content within the mailbox
Security Requirements
Trey Research identifies the following security requirements:
Ensure that the users in the finance department can protect email messages from
being altered in transit, regardless of the recipient.
Prevent the email messages sent to the users in the human resources department
from being forwarded to external recipients.
Prevent the audio files in voice mail message marked as Private from being
extracted from email messages.
Redirect email messages that contain social security information to the legal
department.
Compliance Requirements
Trey Research identifies the following compliance requirements:
All users must be notified before they send an email message that contains any five
bank account numbers to an external recipient. The users must be able to override
the requirement if they have a valid business reason to send the email message.
Users must use a custom message classification when they send email messages
that contain information about the planned acquisition of Fabrikam.
1 Only the users in the legal department must be able to use eDiscovery to view the
contents of email messages sent by the finance department users.
###EndCaseStudy###
DRAG DROP
You restore the files of DB3 to EX3.
You need to mount DB3 on EX3. The solution must ensure that email messages sent to the users of
DB3 while the database was offline are delivered once DB3 is mounted.
Which three actions should you perform in sequence? (To answer, move the appropriate three
actions from the list of actions to the answer area and arrange them in the correct order.)
You need to add an additional replica of VM1
You have a virtual machine named VM1 that runs on a host named Host1.
You configure VM1 to replicate to another host named Host2. Host2 is located in the same
physical location as Host1.
You need to add an additional replica of VM1. The replica will be located in a different
physical site.
What should you do?