How many of each should you identify?
HOTSPOT
A school has 200 students and 10 classes. Each class has 20 students. Each class has one teacher. The
school has five administrative staff members.
You need to design an Exchange Server 2013 organization for the school. The design must meet the
following requirements:
Students must be able to view only the email addresses of the other students in their class, the
teacher of their class, and the entire administrative staff.
Teachers must be able to view only the email addresses of the students in their class, all of the other
teachers, and the entire administrative staff.
The administrative staff must be able to see the email addresses of everyone.
Everyone will use Microsoft Outlook 2013 to view a list of all the users.
You need to identify the minimum number of address lists, global address lists, Offline Address
Books (OABs), and address book policies required for the design.
How many of each should you identify? (To answer, select the appropriate numbers in the answer
area.)
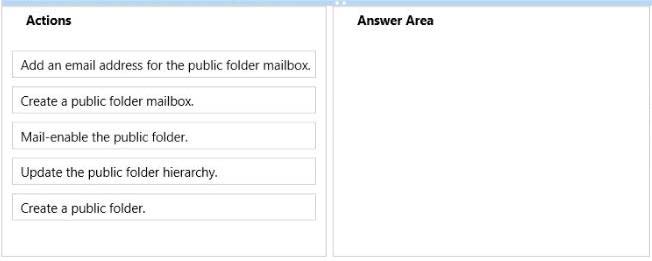
Which three actions should you perform in sequence?
DRAG DROP
You have an Exchange Server 2013 organization that contains a database availability group (DAG)
named DAG1. The organization contains three servers. The servers are configured as shown in the
following table.
EX1 and EX2 are members of DAG1. EX1 has an active copy of a database named DB1 and a passive
copy of a database named DB2. EX2 has a passive copy of DB1 and an active copy of DB2.
You plan to create a public folder named Invoices.
You need to ensure that users can access the Invoices public folder if one of the DAG members fails.
The solution must ensure that the users can send email messages to the Invoices public folder.
Which three actions should you perform in sequence? (To answer, move the appropriate three
actions from the list of actions to the answer area and arrange them in the correct order.)
You need to ensure that a user named User1 can decrypt private keys archived in the Active Directory Certifica
Your network contains an Active Directory domain named adatum.com. The domain contains a
server named CA1 that runs Windows Server 2012 R2. CA1 has the Active Directory Certificate
Services server role installed and is configured to support key archival and recovery.
You need to ensure that a user named User1 can decrypt private keys archived in the Active
Directory Certificate Services (AD CS) database.
The solution must prevent User1 from retrieving the private keys from the AD CS database.
What should you do?
You need to ensure that the users can locate ConfRoom1 on the All Rooms address list
You create a mailbox named ConfRoom1 as shown in the exhibit. (Click the Exhibit button.)
Users report that when they schedule meetings and attempt to locate ConfRoom1 in the All Rooms
address list, they do not see ConfRoom1 on the list.
You need to ensure that the users can locate ConfRoom1 on the All Rooms address list.
What should you do?
You need to identify what prevents DB2 from mounting on EX1
You have an Exchange Server 2013 organization that contains two servers named EX1 and EX2.
EX1 and EX2 are the members of a database availability group (DAG) named DAG1. DAG1 contains
two mailbox databases named DB1 and DB2. DB1 is active on EX1. DB2 is active on EX2.
A disk on EX2 fails. DB2 fails over to EX1.
Users who have mailboxes in DB2 report that Microsoft Outlook can no longer connect to the
Exchange Server organization.
You discover that DB2 is dismounted on EX1.
When you attempt to mount DB2 on EX1, the operation fails.
You need to identify what prevents DB2 from mounting on EX1.
What should you do?
You need to disable temporarily the antimalware scanning on a server that has Exchange Server 2013 installed
You have an Exchange Server 2013 organization.
You are troubleshooting an email delivery problem.
You need to disable temporarily the antimalware scanning on a server that has Exchange Server
2013 installed. The solution must ensure that the antimalware engine continues to download
updates.
What should you run?
You need to ensure that the users in Site2 are authenticated by DC1 or DC2 only if DC3 is unavailable
Your network contains an Active Directory domain named contoso.com.
The domain contains two sites named Site1 and Site2 and two domain controllers named DC1
and DC2. Both domain controllers are located in Site1.
You install an additional domain controller named DC3 in Site1 and you ship DC3 to Site2.
A technician connects DC3 to Site2.
You discover that users in Site2 are authenticated by all three domain controllers.
You need to ensure that the users in Site2 are authenticated by DC1 or DC2 only if DC3 is
unavailable.
What should you do?
What should you identify?
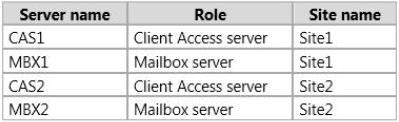
Your company has two offices. Each office is configured as an Active Directory site.
You have an Exchange Server 2013 organization that contains four servers. The servers are
configured as shown in the following table.
MBX1 and MBX2 are members of a database availability group (DAG) named DAG1. A mailbox
database named DB1 has a copy on each Mailbox server. DB1 is active on MBX2.
You are creating a disaster recovery plan for the organization.
You need to identify how email messages will be received for the mailboxes on DB1 if the Exchange
Server transport services fail on MBX2 because of messages in the poison message queue.
What should you identify?
You need to ensure that email sent to D_Sales from the Internet is received by CAS1, and then routed from MBX1
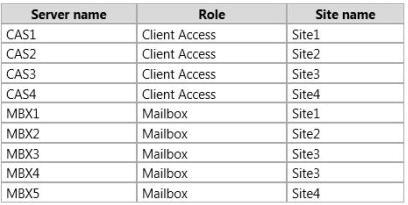
Your company has four offices. Each office is configured as an Active Directory site.
You have an Exchange Server 2013 organization that contains nine servers. The servers are
configured as shown in the following table.
A user named User1 is in a distribution group named D_Sales. The mailbox of User1 is in a database
that is active on MBX4 and is configured to use MBX5 as an expansion server.
You need to ensure that email sent to D_Sales from the Internet is received by CAS1, and then
routed from MBX1 to MBX4.
What should you do?
Which two cmdlets should you run?
You have an Exchange Server 2013 organization that contains four servers.
All users access their email by using Microsoft Outlook 2010.
An administrator deploys a shared mailbox named Project.
You assign all of the users in the marketing department Full Access permissions to Project.
You discover that Project automatically appears in Outlook to all of the marketing department users.
You need to ensure that Project only appears in Outlook to the marketing department users who
add the mailbox manually to their Outlook profile.
Which two cmdlets should you run? (Each correct answer presents part of the solution. Choose two.)