Which code segment should you use?
You have a table named Books that has columns named BookTitle and Description. There is a fulltext
index on these columns. You need to return rows from the table in which the word ‘computer’ exists
in
either column. Which code segment should you use?
You need to move the data from the oldest year into a new table in a different Schema to archive the data
You administer a Microsoft SQL Server 2008 R2 database that contains an OrderItems
table. The table has the following definition:
Currently, the table is partitioned by year with each year in its own filegroup.
You need to move the data from the oldest year into a new table in a different Schema to
archive the data. What should you do?
Which two tasks should you perform?
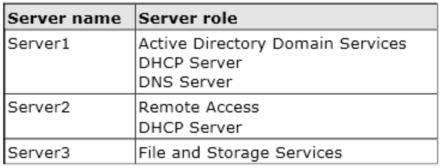
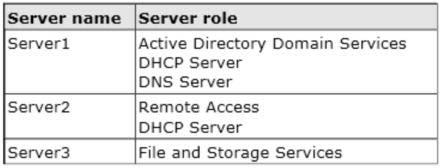
Your network contains three servers that run Windows Server 2012 R2. The servers are configured
as shown in the following table. Server3 is configured to obtain an IP address automatically.
You need to ensure that Server3 only receives an IP address from Server1. The IP address must
always be the same.
Which two tasks should you perform? (Each correct answer presents part of the solution. Choose
two.)
You need to ensure that Computer1 can receive an IP address from DC1
Your network contains an Active Directory domain named contoso.com. The domain contains a
domain controller named DC1 that runs Windows Server 2012 R2 and a client computer named
Computer1 that runs Windows 8. DC1 is configured as a DHCP server as shown in the exhibit.
Computer1 is configured to obtain an IP address automatically.
You need to ensure that Computer1 can receive an IP address from DC1.
What should you do?
What should you create?
Your network contains an Active Directory domain named contoso.com.
You need to prevent users from installing a Windows Store app named App1.
What should you create?
You need to ensure that the new server meets the security policy
Your company’s security policy states that all of the servers deployed to a branch office must not
have the graphical user interface (GUI) installed. In a branch office, a support technician installs a
server with a GUI installation of Windows Server 2012 on a new server, and then configures the
server as a DHCP server.
You need to ensure that the new server meets the security policy. You want to achieve this goal by
using the minimum amount of Administrative effort.
What should you do?
Which process should you use?
You maintain a SQL Server 2008 instance.
You use SQL Server Database Mail to distribute multiple reports that are scheduled and
generated every night.
You need to enforce a mail retention policy to delete copies of automatically generated mails
after 60 days.
Which process should you use?
You need to ensure that the share for Folder1 is not visible when users browse the network
Your network contains a file server named Server1 that runs Windows Server 2012 R2. All client
computers run Windows 8. Server1 contains a folder named Folder1. Folder1 contains the
installation files for the company’s desktop applications. A network technician shares Folder1 as
Share 1.
You need to ensure that the share for Folder1 is not visible when users browse the network.
What should you do?
Which FullText Search component should you use?
You need to configure FullText
Search to ignore specific words. Which FullText
Search component
should you use?
Which command should you run from Server1?
Your network contains an Active Directory domain named contoso.com. The domain contains two
member servers named Server1 and Server2 that run Windows Server 2012 R2. You log on to
Server1. You need to retrieve the IP configurations of Server2. Which command should you run from
Server1?