What command should you run?
HOTSPOT
You have a Hyper-V host named Server1 that runs Windows Server 2012 R2. Server1 hosts 40 virtual
machines that run Windows Server 2008 R2. The virtual machines connect to a private virtual switch.
You have a file that you want to copy to all of the virtual machines.
You need to identify to which servers you can copy files by using the Copy-VmFile cmdlet.
What command should you run? To answer, select the appropriate options in the answer area.
You need to assign a specific amount of available network bandwidth to VM1
You have a server named Server1 that runs Windows Server 2012 R2.Server1 has the Hyper-V server
role installed. On Server1, you create a virtual machine named VM1.VM1 has a legacy network
adapter.
You need to assign a specific amount of available network bandwidth to VM1.
What should you do first?
Which Transact-SQL statements should you execute?
You administer a SQL Server 2008 instance. A database developer named User1 views the
definitions of all database objects in a database to read data from all user-defined tables,
views, and table-valued functions. You need to set the required permissions for User1. You
also need to ensure that the same permissions can be granted to other developers by
executing minimum number of Transact-SQL statements. Which Transact-SQL statements
should you execute?
Which setting in the rule should you configure?
Your network contains an Active Directory domain named contoso.com. The domain contains a
server named Server1 that runs Windows Server 2012 R2.
You create a new inbound rule by using Windows Firewall with Advanced Security.
You need to configure the rule to allow Server1 to accept unsolicited inbound packets that are
received through a network address translation (NAT) device on the network.
Which setting in the rule should you configure?
You need to ensure that Server1 can respond to ping requests from computers that do not support IPSec
Your network contains an Active Directory domain named contoso.com. All servers run Windows
Server 2012 R2. A server named Server1 is configured to encrypt all traffic by using IPSec.
You need to ensure that Server1 can respond to ping requests from computers that do not support
IPSec.
What should you do?
You create the executable rules as shown in the exhibit by using the Create Executable Rules wizard.
HOTSPOT
Your network contains an Active Directory domain named contoso.com. All domain controllers run
Windows Server 2012 R2.
All servers are configured to enforce AppLocker policies.
You install a server named Server1.
On Server1, you install an application named App1.exe in a folder located on C:\App1.
You have two domain groups named Group1 and Group2.A user named User1 is a member of
Group1 and Group2.
You create a Group Policy object (GPO) named GPO1. You link GPO1 to contoso.com.
You create the executable rules as shown in the exhibit by using the Create Executable Rules wizard.
(Click the Exhibit button.)
To answer, complete each statement according to the information presented in the exhibit. Each
correct selection is worth one point.
Which tool should you use?
You have a server named Server1 that runs Windows Server 2012 R2.
You need to create a script that will create and mount a virtual hard disk.
Which tool should you use?
Which cmdlet should you use to perform each task?
DRAG DROP
You have a server named Server1 that runs Windows Server 2012 R2.
You need to perform the following storage configuration tasks on Server1:
Bring a disk named Disk1 online.
Defragment a volume named Volume1.
Remove a disk named Disk2 from a storage pool named Pool1.
Which cmdlet should you use to perform each task?
To answer, drag the appropriate cmdlets to the correct tasks. Each cmdlet may be used once, more
than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
You need to ensure that Server1 can accept network traffic on VLAN 10 and VLAN 11
You have a server named Server1 that runs Windows Server 2012 R2.
Server1 has three physical network adapters named NIC1, NIC2, and NIC3.
On Server1, you create a NIC team named Team1 by using NIC1 and NIC2. You configure Team1 to
accept network traffic on VLAN 10.
You need to ensure that Server1 can accept network traffic on VLAN 10 and VLAN 11. The solution
must ensure that the network traffic can be received on both VLANs if a network adapter fails.
What should you do?
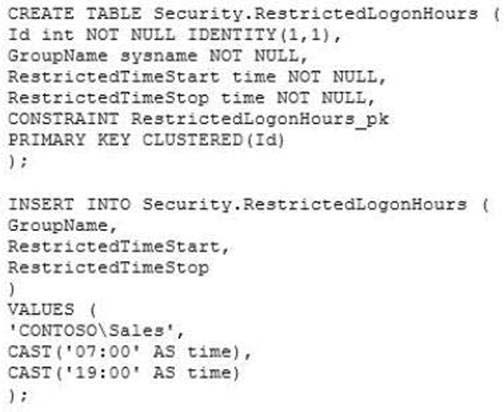
You need to implement the company security policy that is stored in the RestrictedLogonHours table
You administer a SQL Server 2008 instance.
The security policy permits members of a Windows group named CONTOSO\Sales to
establish new connections to the SQL Server instance only during business horns between
07:00 horns and
19:00 hours. Other users may connect to the SQL Server instance any time.
You write the following Transact-SQL statements.
You need to implement the company security policy that is stored in the
RestrictedLogonHours table.
What should you do?