which column in the Employee table should you create a Primary Key constraint for this table?
You administer a Microsoft SQL Server 2012 database.
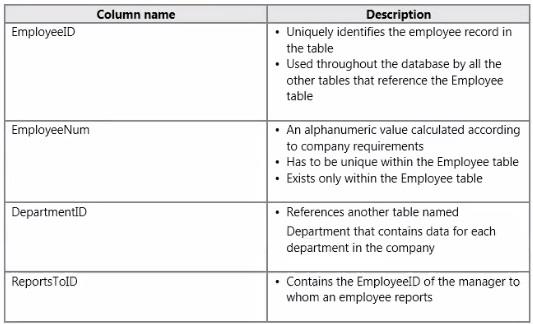
The database contains a table named Employee. Part of the Employee table is shown in the exhibit.
(Click the Exhibit button.)
Unless stated above, no columns in the Employee table reference other tables.
Confidential information about the employees is stored in a separate table named EmployeeData.
One record exists within EmployeeData for each record in the Employee table.
You need to assign the appropriate constraints and table properties to ensure data integrity and
visibility.
On which column in the Employee table should you create a Primary Key constraint for this table?
Which Transact-SQL statement should you use?
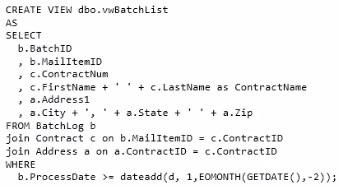
You create a view based on the following statement:
You grant the Select permission to User1.
You need to change the view so that it displays only the records that were processed in the month
prior to the current month. You need to ensure that after the changes, the view functions correctly
for User1.
Which Transact-SQL statement should you use?
Which TransactSQL statement should you use?
You have a user named John. He has SELECT access to the Sales schema. You need to eliminate
John’s SELECT access rights from the Sales.SalesOrder table without affecting his other permissions.
Which TransactSQL statement should you use?
Which is correct?
Your workstation has installed Microsoft SQL Server Management Studio (SSMS), and not
installed Microsoft Business Intelligence Development Studio (BIDS).
-You should design a package, which has the following features: -The package should be
transactional. -The package should be optimized for 10 tables. -The package should be
stored safely in the msdb database of a server which is remote.
Which is correct?
Which two column definitions should you choose?
You need to create a column that allows you to create a unique constraint.
Which two column definitions should you choose? (Each correct answer presents a complete
solution.
Choose two.)
Which is the correct answer?
You are mastering the company database called TesterDB; the database includes a
database that uses SQL Server log shipping. Log shipping will happen half a hour. You
should make the full backup.
In order to cut the net bandwidth utilization when maintenance every night.
Which is the correct answer?
Does this meet the goal?
Your network contains 50 servers that run Windows Server 2003 and 50 servers that run
Windows Server 2008.
You plan to implement Windows Server 2012 R2.
You need to create a report that includes the following information:
• The servers that run applications and services that can be moved to Windows Server
2012 R2
• The servers that have hardware that can run Windows Server 2012 R2
• The servers that are suitable to be converted to virtual machines hosted on Hyper-V
hosts that run Windows Server 2012 R2
Solution: You install Windows Server 2012 R2 on a new server, and then you run Microsoft
Deployment Toolkit (MDT) 2012.
Does this meet the goal?
Does this meet the goal?
Your network contains 50 servers that run Windows Server 2003 and 50 servers that run
Windows Server 2008.
You plan to implement Windows Server 2012 R2.
You need to create a report that includes the following information:
• The servers that run applications and services that can be moved to Windows Server
2012 R2
• The servers that have hardware that can run Windows Server 2012 R2
• The servers that are suitable to be converted to virtual machines hosted on Hyper-V
hosts that run Windows Server 2012 R2
Solution: You install Windows Server 2012 R2 on a new server, and then you run the
Windows Server Migration Tools. Does this meet the goal?
Which is the correct answer?
You are mastering the company database, Users complaints that the SQL Server 2008
application is running slowly. You should check the information of the CPU utilization, disk
utilization, and memory utilization. The network should be considered. the detailed
information should be checked for the proper example of SQL Server2008.Which is the
correct answer?
Does this meet the goal?
Your network contains an Active Directory domain named contoso.com. The domain
contains multiple sites.
You plan to deploy DirectAccess.
The network security policy states that when client computers connect to the corporate
network from the Internet, all of the traffic destined for the Internet must be routed through
the corporate network.
You need to recommend a solution for the planned DirectAccess deployment that meets the
security policy requirement
Solution: You set the ISATAP State to state disabled.
Does this meet the goal?