You need to ensure that the website is always responsive
###BeginCaseStudy###
Case Study: 2
Contoso, Ltd
Background
Contoso, Ltd. is developing a patient monitoring solution for a hospital. The solution consists
of an Azure website and a set of mobile applications that health care providers use to monitor
patients remotely.
Monitoring devices that run the embedded version of Windows will be attached to patients.
The devices will collect information from patients and will transmit real-time continuous data
to a service that runs on Azure. The service collects and distributes data. The data that the
service provides must be accessible by the website and by the mobile applications.
Business Requirements
Patients
All patient data must be stored securely on Azure. Data security must meet or exceed Health
Insurance Portability and Accountability Act of 1996 (HIPAA) standards in the United States
and must meet or exceed ISO/ICE 27002 data security standards in the rest of the world.
Contractors
Third-party contractors will develop the mobile applications. All contractors must develop
the applications by using virtual machines (VMs) that are hosted on Azure. Only authorized
contractors and authorized IP addresses are permitted to access the VMs. The contractors can
use Near Field Communication (NFC) tags to launch Remote Desktop (RD) connections to
the VMs from NFC-enabled devices. For testing purposes, contractors must be able to run
multiple instances of mobile applications within the VMs.
Data Collection and Distribution Service
The service must monitor the patient data and send out alerts to health care providers when
specific conditions are detected. The service must send the alerts to mobile applications and
to the website in real time so that doctors, nurses, and caregivers can attend to the patient.
Partner organizations and diagnostic laboratories must be able to securely access the data and
the website from remote locations.
Current Issues
A partner that is testing a prototype of the website reports that after signing in to the website,
the partner is redirected to the settings page instead of to the home page.
The data from the patient devices is slow to appear on the website and does not always
appear. All patient devices online have active connections to the data collection service.
Technical Requirements
Contractors
All contractors will use virtual machines that are initially configured as size A3. Contractors
must sign in to the assigned VM by using IP addresses from a list of preapproved addresses.
Data Collection and Distribution Service
• The service runs Node.js in a worker role.
• The service must use at least 2048-bit encryption and must use port 8888.
• All patient information must be encrypted and stored by using a NoSQL data store.
• Data must be stored and retrieved securely by using RESTful endpoints.
• Data must NOT be stored within a virtual machine.
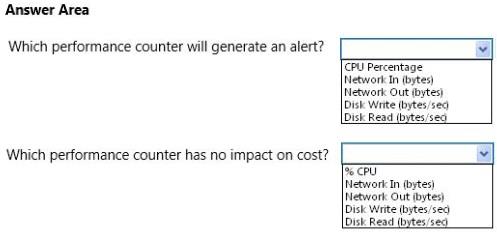
All deployed services must send an alert email to watchguard@contoso.com when any of the
following conditions is met:
• The CPU Percentage metric is at or above 85 percent for at least 10 minutes.
• The Network In metric is at or above 2 KB for at least 10 minutes.
• The Network Out metric is at or above 2 KB for at least 10 minutes.
• The Disk Write metric is at or above 1 KB/sec for at least 30 minutes.
• The Disk Read metric is at or above 1 KB/sec for at least 30 minutes.
Website and Mobile Devices
The website must be secure and must be accessible only within the hospital’s physical
grounds. All mobile applications and websites must be responsive. All websites must produce
error logs that can be viewed remotely.
Virtual Machines
• All Azure instances must be deployed and tested on staging instances before they are
deployed to production instances.
• All deployed instances must scale up to the next available CPU instance at a CPU
usage threshold of 90 percent and scale down when the usage is below 10 percent.
Application Structure
Relevant portions of the application files are shown in the following code segments. Line
numbers in the code segments are included for reference only and include a two-character
prefix that denotes the specific file to which they belong.
###EndCaseStudy###
Users report that after periods of inactivity the website is slow to render pages and to process sign-in
attempts.
You need to ensure that the website is always responsive.
What should you do?
Which command should you run?
Your network contains a single Active Directory domain. All servers run Windows Server 2008 R2. A
DHCP server is deployed on the network and configured to provide IPv6 prefixes. You need to ensure
that when you monitor network traffic, you see the interface identifiers derived from the Extended
Unique Identifier (EUI)-64 address. Which command should you run?
Which method should you call on the ObjectContext?
You use Microsoft Visual Studio 2010 and Microsoft .NET Framework 4 to create an application. The
application connects to a Microsoft SQL Server database. The application uses the ADO.NET Entity
Framework to manage order data. The application makes a Web service call to obtain orders from an
order-tracking system. You need to ensure that the orders are added to the local data store. Which
method should you call on the ObjectContext?
You need to ensure that the following requirements are met: The control is reusable in multiple forms
You are designing a Windows application by using Microsoft .NET Framework 4 and
Microsoft Visual Studio 2010. You plan to implement control caching to improve the loading
time of a control. It is not required to refresh the content of the control after the application
loads. The application will be compiled by using the .NET 4 client profile. You need to
ensure that the following requirements are met: The control is reusable in multiple forms.
Data in the control is cached when the application is loaded. What should you do?
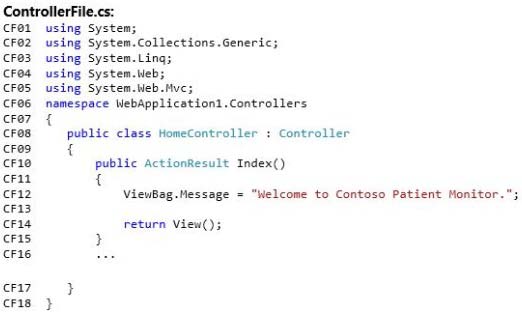
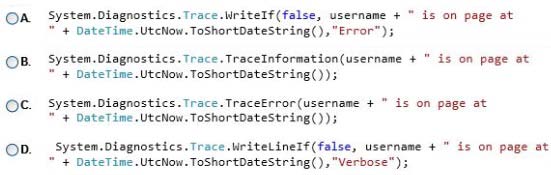
Which code segment should you insert at line CF13?
###BeginCaseStudy###
Case Study: 2
Contoso, Ltd
Background
Contoso, Ltd. is developing a patient monitoring solution for a hospital. The solution consists
of an Azure website and a set of mobile applications that health care providers use to monitor
patients remotely.
Monitoring devices that run the embedded version of Windows will be attached to patients.
The devices will collect information from patients and will transmit real-time continuous data
to a service that runs on Azure. The service collects and distributes data. The data that the
service provides must be accessible by the website and by the mobile applications.
Business Requirements
Patients
All patient data must be stored securely on Azure. Data security must meet or exceed Health
Insurance Portability and Accountability Act of 1996 (HIPAA) standards in the United States
and must meet or exceed ISO/ICE 27002 data security standards in the rest of the world.
Contractors
Third-party contractors will develop the mobile applications. All contractors must develop
the applications by using virtual machines (VMs) that are hosted on Azure. Only authorized
contractors and authorized IP addresses are permitted to access the VMs. The contractors can
use Near Field Communication (NFC) tags to launch Remote Desktop (RD) connections to
the VMs from NFC-enabled devices. For testing purposes, contractors must be able to run
multiple instances of mobile applications within the VMs.
Data Collection and Distribution Service
The service must monitor the patient data and send out alerts to health care providers when
specific conditions are detected. The service must send the alerts to mobile applications and
to the website in real time so that doctors, nurses, and caregivers can attend to the patient.
Partner organizations and diagnostic laboratories must be able to securely access the data and
the website from remote locations.
Current Issues
A partner that is testing a prototype of the website reports that after signing in to the website,
the partner is redirected to the settings page instead of to the home page.
The data from the patient devices is slow to appear on the website and does not always
appear. All patient devices online have active connections to the data collection service.
Technical Requirements
Contractors
All contractors will use virtual machines that are initially configured as size A3. Contractors
must sign in to the assigned VM by using IP addresses from a list of preapproved addresses.
Data Collection and Distribution Service
• The service runs Node.js in a worker role.
• The service must use at least 2048-bit encryption and must use port 8888.
• All patient information must be encrypted and stored by using a NoSQL data store.
• Data must be stored and retrieved securely by using RESTful endpoints.
• Data must NOT be stored within a virtual machine.
All deployed services must send an alert email to watchguard@contoso.com when any of the
following conditions is met:
• The CPU Percentage metric is at or above 85 percent for at least 10 minutes.
• The Network In metric is at or above 2 KB for at least 10 minutes.
• The Network Out metric is at or above 2 KB for at least 10 minutes.
• The Disk Write metric is at or above 1 KB/sec for at least 30 minutes.
• The Disk Read metric is at or above 1 KB/sec for at least 30 minutes.
Website and Mobile Devices
The website must be secure and must be accessible only within the hospital’s physical
grounds. All mobile applications and websites must be responsive. All websites must produce
error logs that can be viewed remotely.
Virtual Machines
• All Azure instances must be deployed and tested on staging instances before they are
deployed to production instances.
• All deployed instances must scale up to the next available CPU instance at a CPU
usage threshold of 90 percent and scale down when the usage is below 10 percent.
Application Structure
Relevant portions of the application files are shown in the following code segments. Line
numbers in the code segments are included for reference only and include a two-character
prefix that denotes the specific file to which they belong.
###EndCaseStudy###
You need to implement tracing for the website after the website is deployed.
Which code segment should you insert at line CF13?
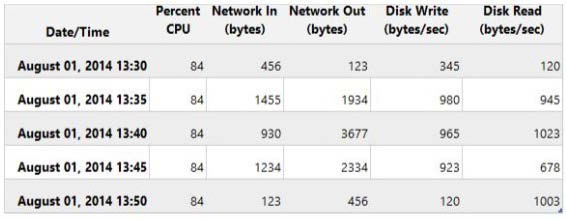
The metrics shown in the following exhibit represent the average values for each five-minute period.
###BeginCaseStudy###
Case Study: 2
Contoso, Ltd
Background
Contoso, Ltd. is developing a patient monitoring solution for a hospital. The solution consists
of an Azure website and a set of mobile applications that health care providers use to monitor
patients remotely.
Monitoring devices that run the embedded version of Windows will be attached to patients.
The devices will collect information from patients and will transmit real-time continuous data
to a service that runs on Azure. The service collects and distributes data. The data that the
service provides must be accessible by the website and by the mobile applications.
Business Requirements
Patients
All patient data must be stored securely on Azure. Data security must meet or exceed Health
Insurance Portability and Accountability Act of 1996 (HIPAA) standards in the United States
and must meet or exceed ISO/ICE 27002 data security standards in the rest of the world.
Contractors
Third-party contractors will develop the mobile applications. All contractors must develop
the applications by using virtual machines (VMs) that are hosted on Azure. Only authorized
contractors and authorized IP addresses are permitted to access the VMs. The contractors can
use Near Field Communication (NFC) tags to launch Remote Desktop (RD) connections to
the VMs from NFC-enabled devices. For testing purposes, contractors must be able to run
multiple instances of mobile applications within the VMs.
Data Collection and Distribution Service
The service must monitor the patient data and send out alerts to health care providers when
specific conditions are detected. The service must send the alerts to mobile applications and
to the website in real time so that doctors, nurses, and caregivers can attend to the patient.
Partner organizations and diagnostic laboratories must be able to securely access the data and
the website from remote locations.
Current Issues
A partner that is testing a prototype of the website reports that after signing in to the website,
the partner is redirected to the settings page instead of to the home page.
The data from the patient devices is slow to appear on the website and does not always
appear. All patient devices online have active connections to the data collection service.
Technical Requirements
Contractors
All contractors will use virtual machines that are initially configured as size A3. Contractors
must sign in to the assigned VM by using IP addresses from a list of preapproved addresses.
Data Collection and Distribution Service
• The service runs Node.js in a worker role.
• The service must use at least 2048-bit encryption and must use port 8888.
• All patient information must be encrypted and stored by using a NoSQL data store.
• Data must be stored and retrieved securely by using RESTful endpoints.
• Data must NOT be stored within a virtual machine.
All deployed services must send an alert email to watchguard@contoso.com when any of the
following conditions is met:
• The CPU Percentage metric is at or above 85 percent for at least 10 minutes.
• The Network In metric is at or above 2 KB for at least 10 minutes.
• The Network Out metric is at or above 2 KB for at least 10 minutes.
• The Disk Write metric is at or above 1 KB/sec for at least 30 minutes.
• The Disk Read metric is at or above 1 KB/sec for at least 30 minutes.
Website and Mobile Devices
The website must be secure and must be accessible only within the hospital’s physical
grounds. All mobile applications and websites must be responsive. All websites must produce
error logs that can be viewed remotely.
Virtual Machines
• All Azure instances must be deployed and tested on staging instances before they are
deployed to production instances.
• All deployed instances must scale up to the next available CPU instance at a CPU
usage threshold of 90 percent and scale down when the usage is below 10 percent.
Application Structure
Relevant portions of the application files are shown in the following code segments. Line
numbers in the code segments are included for reference only and include a two-character
prefix that denotes the specific file to which they belong.
###EndCaseStudy###
HOTSPOT
You configure alerts in Azure. The metrics shown in the following exhibit represent the average values for each
five-minute period.
To answer, make the appropriate selections in the answer area.
Which two actions should you recommend?
You are designing an ASP.NET Web application that allows users to type a value in a text
box. The application must function with JavaScript disabled. You need to design a method
for using a Web service to validate the user-typed value before the form is processed.
Which two actions should you recommend? (Each correct answer presents part of the
solution. Choose two.)
Which code segment should you insert at line 02?
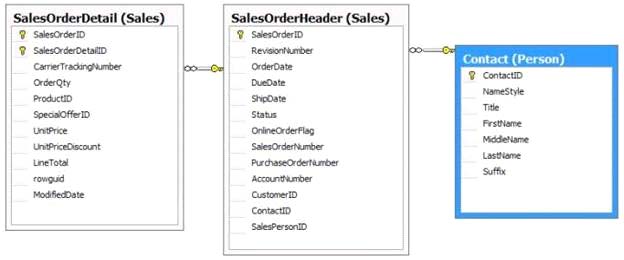
You use Microsoft Visual Studio 2010 and Microsoft .NET Framework 4 to create an application. The
application connects to a Microsoft SQL Server database. The application uses the ADO.NET Entity
Framework to model entities. The database includes objects based on the exhibit. (Click the Exhibit
button.)
The application includes the following code segment. (Line numbers are included for reference only.)
01 using (AdventureWorksEntities advWorksContext = new AdventureWorksEntities()){
02
03 }
You need to retrieve a list of all Products from todays sales orders for a specified customer. You also
need to ensure that the application uses the minimum amount of memory when retrieving the list.
Which code segment should you insert at line 02?
You need to implement endpoint monitoring
###BeginCaseStudy###
Case Study: 3
Mortgage Loan
Background
A company is developing a website that supports mortgage loan processing. You use the
Azure management portal to create a website. You initially configure the website to use the
Basic hosting plan. You register a custom domain for the website with a valid registrar.
Customers complete mortgage applications and upload supporting documents to the website.
A custom executable named FileProcessor.exe processes all of the information received. An
on-premises server that runs Windows Server hosts the executable.
You create a virtual hard disk (VHD) image of the on-premises server. You plan to use this
VHD to replace the on-premises server with a new virtual machine (VM) that is hosted in
Azure.
Business Requirements
Business stakeholders have identified the following requirements for the mortgage loan
processing website:
• The website must provide a secure mortgage application process for the customer.
• Business users must validate new versions of the website before you publish them to
the production site. You must be able to revert to the previous version easily when issues
arise.
• The website must remain available to users while new features and bug fixes are
deployed.
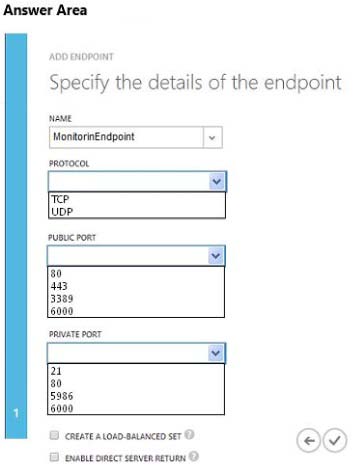
• Network traffic must be monitored on all ports that the website uses.
Technical Requirements
General:
• You must develop the website by using Microsoft Visual Studio 2013.
• The website must be stateless. Subsequent requests from a user might or might not be
routed back to the website instance that the user initially connected to.
Security:
You must secure the custom domain and all subdomains by using SSL.
Storage:
• The custom executable must use native file system APIs to share data between
different parts of the website.
• The custom executable must continue to use a network file share to access files.
Monitoring:
The website must use port 6000 with UDP to submit information to another process. This
port must be actively monitored by using the same external port number.
Deployment:
• You must deploy the VM and the associated VHD. You will need to move this VM to
a different Azure subscription after deployment.
• You must establish a continuous deployment process that uses staged publishing.
• The custom domain must handle requests for multiple subdomains.
• The custom domain must use a www CNAME record that points to the domain’s @ A
record.
• The custom executable must run continuously and must be deployed as an Azure web
job named FileProcessor
• Application Request Routing (ARRJ affinity must be disabled for the website.
Solution Structure
The solution structure for the website is shown in the following exhibit.
HOTSPOT
You need to implement endpoint monitoring.
What should you do? To answer, configure the appropriate options in the dialog box in the answer area.
Which plan should you recommend?
You are designing a SharePoint 2010 application that stores information about each
machine in a factory. This information includes an inventory of parts, the machine’s
maintenance history, and a document library of repair manuals for each machine in
Microsoft Word format. The application must: ·Establish links between the factory machine
data, the machine part inventory, the maintenance history, and the repair manuals to allow
the display of additional fields from the other lists. .Enforce relational integrity between the
data to create custom views for various business users. .Allow nontechnical users to update
the individual list data and views, as well as to update the manuals. .Enforce relationships
that allow cascade deletes of items from the machine parts list when items are deleted from
the machine list, but prevent data in the machine parts list from being orphaned. You need
to design a data access plan that meets all these requirements and allows all data to be
managed within the SharePoint 2010 system. Which plan should you recommend?