Which role service should you include in the recommendation?
###BeginCaseStudy###
Case Study: 9
Humongous Insurance
COMPANY OVERVIEW
Humongous Insurance has a main office and 20 branch offices. The main office is located in New
York. The branch offices are located throughout North America. The main office has 8,000 users.
Each branch office has 2 to 250 users.
PLANNED CHANGES
Humongous Insurance plans to implement the following changes:
• Deploy one Read-only Domain Controller (RODC) to Site3 and one RODC to Site4.
• Issue certificates to the users in Contoso. The certificates will be based on custom certificate
templates.
• Deploy a Remote Desktop Services (RDS) infrastructure that will contain 10 Remote Desktop
servers. Users will connect to all Remote Desktop servers from the Internet by using port 443.
EXISTING ENVIRONMENT
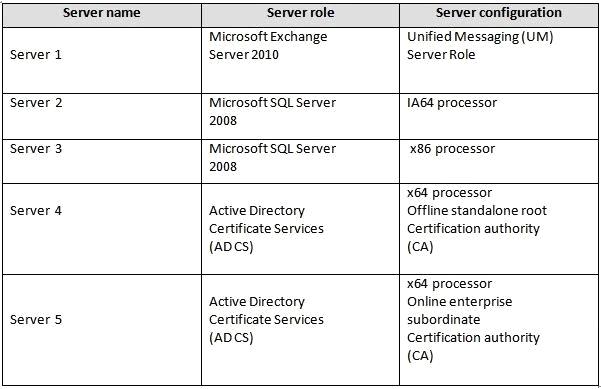
The network contains the servers configured as shown in the following table.
Business Goals
All of the strategies for deploying physical servers and virtual servers must meet the Microsoft
guidelines for product support.
Existing Active Directory Environment
The network contains a single Active Directory forest named humongousinsurance.com. The
functional level of the forest is Windows Server 2008 R2.
The Active Directory sites are shown in the exhibit. (Click the Case Study Exhibit button.)
Existing Network Infrastructure
Humongous Insurance issues smart cards to administrators. Smart cards are not required for logon.
Humongous Insurance acquires a company named Contoso, Ltd.
REQUIREMENTS
Technical Requirements
All of the users in Contoso must be able to enroll for certificates by using the Public Key
Infrastructure (PKI) of Humongous Insurance.
Humongous Insurance must meet the following requirements for managing Group Policy objects
(GPOs):
• Minimize administrative effort.
• Support offline editing of the GPOs.
• Retain multiple versions of the GPOs.
Security Requirements
Only administrators who log on by using smart cards must be able to manage objects in Active
Directory.
The corporate security policy states that a forest trust to any other forest must not exist.
CASE STUDY EXHIBIT
Click the case study exhibit button to view the exhibit.
###EndCaseStudy###
You need to recommend an RDS solution that supports the company’s planned changes.
Which role service should you include in the recommendation?
Which tool should you use?
You manage a Web server named Server1 that runs windows server 2008 R2. Server1 has the FTP
Server role installed. You need to manage the FTP settings on Server1. Which tool should you use?
Which feature should you configure from Internet Information Services (IIS) Manager?
Your network contains a Web server named Server1 that runs Windows Server 2008 R2. Server1
contains a Web site named Site1. Site1 contains a Web page named Priv.aspx. The Web page is
stored on a FAT partition. You need to ensure that only a user named User1 can access Priv.aspx. All
other content on Sitel must be accessible to everyone. Which feature should you configure from
Internet Information Services (IIS) Manager?
What should you recommend?
###BeginCaseStudy###
Case Study: 10
Litware Inc.
COMPANY OVERVIEW
Litwate Inc. is a manufacturing company that has a main office and four branch offices.
PLANNED CHANGES
Litware plans to deploy Group Policy object (GPOs). The planned deployment must meet the
following requirements:
Deploy a GPO to a client computer based on its respective local office.
Minimize the amount of administrative effort required to manage the GPOs.
Prevent the users m each department from receiving CPOs from other departments.
Deploy a GPO to a user based on his respective department.
Litware plans to change the name of AD.liteware.com to east.ktware.com. The planned change must
meet the following retirements:
Minimize administrative effort.
Minimize the impact on the users m AD.liteware.com.
Litware plans to deploy RemoteApp programs to meet the following requirements:
The RemoteApp programs must be visible from the Start menu on each client computer.
The RemoteApp programs must be published by using the minimum amount of administrative
effort.
Litware plans to deploy several Hyper-V servers that will host multiple virtual machines (VMs). The
deployment must meet the following requirements:
Minimize administrative effort.
Back up the VMs to a tape library.
Store all of the VM files on a Storage Area Network (SAN).
Convert all of the client computers in the finance department to a VM.
Litware plans to deploy a network access solution. The planned deployment must use the minimum
amount of administrative effort.
EXISTING ENVIRONMENT
All servers run Widows Server 2008 R2. All client computers run Windows 7.
Litware has three departments, including a finance department. Each department has users n each
office. The network contains a Microsoft Exchange Server 2010 organization.
Existing Active Directory Environment
The network contains a single Active Directory forest named litware.com. The Forest contains one
child domain named AD.litware.com and two other domains.
The functional level of the forest is Windows Server 2003.
A single Active Directory site exists for all of the offices.
Existing Network Infrastructure
The network contains an internal network and a perimeter network that are separated by a
hardware-based firewall. A hardware-based firewall also separates the perimeter network and the
Internet.
The following protocols on the default ports are allowed through the firewall that is connected to
the Internet:
HTTP
HTTPS
Point-To-Point Tunneling Protocol (PPTP)
Only the client computers on the perimeter network can connect to the client computers on the
internal network.
The perimeter network contains a VPN server. Users who work remotely use PPTP to establish VPN
connections to the network.
Current Administration Model
Each domain contains a file server that stores confidential documents.
Each domain has dedicated user Accounts for auditing purposes. The user accounts are only used for
auditing the company’s confidential documents.
SECURITY REQUIREMLNTS
The corporate security policy states the following requirements:
• Ensure that the latest windows updates are installed on all client computers.
• Ensure that Windows Firewall is enabled on every client computer that connects remotely.
• Prevent all client computers that do not comply with the security policy from connecting to
the internal servers.
The corporate auditing poky must meet the following requirements:
• Only the dedicated user accounts must be able access servers that contain confidential
documents.
• The dedicated user accounts must be assigned auditing rights as a group, not as individual
users.
• The number of groups that contain the dedicated user accounts must be minimized.
###EndCaseStudy###
You need to recommend an organizational unit (OU) structure that supports the company’s planned
changes.
What should you recommend?
Which tool should you use?
Your network contains an Active directory domain named fabrikam.com. The domain contatins a
Web server named Web1 that runs Windows Server 2008 R2. You install the SMTP Server feature on
Web1. You need to verify whether you can establish an SMTP connection to Web1. Which tool
should you use?
Which command should you run on the server?
You install the Web Server (IIS) server role on a server that runs Windows Server 2008 R2. You
configure a Web site named contoso.com and a Web application named Accounting on the Web
server. The Web server runs out of disk space. You move Accounting to another drive on the Web
server. The following table shows the current application configuration:
Users report that they cannot access the Accounting application. You need to enable users to access
Accounting application. Which command should you run on the server?
What should you include in the recommendation?
###BeginCaseStudy###
Case Study: 10
Litware Inc.
COMPANY OVERVIEW
Litwate Inc. is a manufacturing company that has a main office and four branch offices.
PLANNED CHANGES
Litware plans to deploy Group Policy object (GPOs). The planned deployment must meet the
following requirements:
Deploy a GPO to a client computer based on its respective local office.
Minimize the amount of administrative effort required to manage the GPOs.
Prevent the users m each department from receiving CPOs from other departments.
Deploy a GPO to a user based on his respective department.
Litware plans to change the name of AD.liteware.com to east.ktware.com. The planned change must
meet the following retirements:
Minimize administrative effort.
Minimize the impact on the users m AD.liteware.com.
Litware plans to deploy RemoteApp programs to meet the following requirements:
The RemoteApp programs must be visible from the Start menu on each client computer.
The RemoteApp programs must be published by using the minimum amount of administrative
effort.
Litware plans to deploy several Hyper-V servers that will host multiple virtual machines (VMs). The
deployment must meet the following requirements:
Minimize administrative effort.
Back up the VMs to a tape library.
Store all of the VM files on a Storage Area Network (SAN).
Convert all of the client computers in the finance department to a VM.
Litware plans to deploy a network access solution. The planned deployment must use the minimum
amount of administrative effort.
EXISTING ENVIRONMENT
All servers run Widows Server 2008 R2. All client computers run Windows 7.
Litware has three departments, including a finance department. Each department has users n each
office. The network contains a Microsoft Exchange Server 2010 organization.
Existing Active Directory Environment
The network contains a single Active Directory forest named litware.com. The Forest contains one
child domain named AD.litware.com and two other domains.
The functional level of the forest is Windows Server 2003.
A single Active Directory site exists for all of the offices.
Existing Network Infrastructure
The network contains an internal network and a perimeter network that are separated by a
hardware-based firewall. A hardware-based firewall also separates the perimeter network and the
Internet.
The following protocols on the default ports are allowed through the firewall that is connected to
the Internet:
HTTP
HTTPS
Point-To-Point Tunneling Protocol (PPTP)
Only the client computers on the perimeter network can connect to the client computers on the
internal network.
The perimeter network contains a VPN server. Users who work remotely use PPTP to establish VPN
connections to the network.
Current Administration Model
Each domain contains a file server that stores confidential documents.
Each domain has dedicated user Accounts for auditing purposes. The user accounts are only used for
auditing the company’s confidential documents.
SECURITY REQUIREMLNTS
The corporate security policy states the following requirements:
• Ensure that the latest windows updates are installed on all client computers.
• Ensure that Windows Firewall is enabled on every client computer that connects remotely.
• Prevent all client computers that do not comply with the security policy from connecting to
the internal servers.
The corporate auditing poky must meet the following requirements:
• Only the dedicated user accounts must be able access servers that contain confidential
documents.
• The dedicated user accounts must be assigned auditing rights as a group, not as individual
users.
• The number of groups that contain the dedicated user accounts must be minimized.
###EndCaseStudy###
You need to recommend a solution for the client computers in the finance department. The solution
must support the company’s planned changes.
What should you include in the recommendation?
Which tool should you use?
You manage a Web server named Server1 that runs Windows Server 2008 R2. Server1 has the SMTP
Server feature installed. You need to manage the SMTP server settings. Which tool should you use?
What should you include in the recommendation?
###BeginCaseStudy###
Case Study: 10
Litware Inc.
COMPANY OVERVIEW
Litwate Inc. is a manufacturing company that has a main office and four branch offices.
PLANNED CHANGES
Litware plans to deploy Group Policy object (GPOs). The planned deployment must meet the
following requirements:
Deploy a GPO to a client computer based on its respective local office.
Minimize the amount of administrative effort required to manage the GPOs.
Prevent the users m each department from receiving CPOs from other departments.
Deploy a GPO to a user based on his respective department.
Litware plans to change the name of AD.liteware.com to east.ktware.com. The planned change must
meet the following retirements:
Minimize administrative effort.
Minimize the impact on the users m AD.liteware.com.
Litware plans to deploy RemoteApp programs to meet the following requirements:
The RemoteApp programs must be visible from the Start menu on each client computer.
The RemoteApp programs must be published by using the minimum amount of administrative
effort.
Litware plans to deploy several Hyper-V servers that will host multiple virtual machines (VMs). The
deployment must meet the following requirements:
Minimize administrative effort.
Back up the VMs to a tape library.
Store all of the VM files on a Storage Area Network (SAN).
Convert all of the client computers in the finance department to a VM.
Litware plans to deploy a network access solution. The planned deployment must use the minimum
amount of administrative effort.
EXISTING ENVIRONMENT
All servers run Widows Server 2008 R2. All client computers run Windows 7.
Litware has three departments, including a finance department. Each department has users n each
office. The network contains a Microsoft Exchange Server 2010 organization.
Existing Active Directory Environment
The network contains a single Active Directory forest named litware.com. The Forest contains one
child domain named AD.litware.com and two other domains.
The functional level of the forest is Windows Server 2003.
A single Active Directory site exists for all of the offices.
Existing Network Infrastructure
The network contains an internal network and a perimeter network that are separated by a
hardware-based firewall. A hardware-based firewall also separates the perimeter network and the
Internet.
The following protocols on the default ports are allowed through the firewall that is connected to
the Internet:
HTTP
HTTPS
Point-To-Point Tunneling Protocol (PPTP)
Only the client computers on the perimeter network can connect to the client computers on the
internal network.
The perimeter network contains a VPN server. Users who work remotely use PPTP to establish VPN
connections to the network.
Current Administration Model
Each domain contains a file server that stores confidential documents.
Each domain has dedicated user Accounts for auditing purposes. The user accounts are only used for
auditing the company’s confidential documents.
SECURITY REQUIREMLNTS
The corporate security policy states the following requirements:
• Ensure that the latest windows updates are installed on all client computers.
• Ensure that Windows Firewall is enabled on every client computer that connects remotely.
• Prevent all client computers that do not comply with the security policy from connecting to
the internal servers.
The corporate auditing poky must meet the following requirements:
• Only the dedicated user accounts must be able access servers that contain confidential
documents.
• The dedicated user accounts must be assigned auditing rights as a group, not as individual
users.
• The number of groups that contain the dedicated user accounts must be minimized.
###EndCaseStudy###
You need to recommend a backup strategy for the VMs that supports the company’s planned
changes.
What should you include in the recommendation?
You need to enable Server1 to play the content in File1.wmv
Your network contains a server named Server1 that has the Streaming Media Services server role
installed. Windows Media Services is configured to log on as a user named User1. On Server1, you
have a media file named File1.wmv. File1.wmv is protected by Encrypting File System (EFS). You
create a publishing point on WMS1 and select File1.wmv as the content source. When you start the
publishing point, you receive the error message. You need to enable Server1 to play the content in
File1.wmv. What should you do?