Which three inbound firewall ports should you open on Firewall1?
Your network contains a server named Server1 that has the Streaming Media Services server role
installed. Server1 is located in the perimeter network. A firewall named Firewall1 connects the
perimeter network and the Internet. You need to ensure that clients from the Internet can access
streaming content from Server1 by using RTSP and HTTP. The solution must minimize the number of
open ports on Firewall1. Which three inbound firewall ports should you open on Firewall1? (Each
correct answer presents part of the solution, choose three.)
Which Diskpart command should you run first?
Your network contains an Active Directory domain named adatum.com. The domain contains a
server named Servers that runs windows Server 2008 R2 Service Pack 1 (SP1). Server5 contains a
mirrored volume named Volume1. You need to replace one of the disks in Volume1. Which Diskpart
command should you run first?
What should you recommend?
###BeginCaseStudy###
Case Study: 8
Blue yonder Airlines
COMPANY OVERVIEW
Blue Yonder Airlines has a main office and four branch offices.
PLANNED CHANGES
Blue Yonder Airlines plans to implement the following changes:
• Upgrade all client computers to Windows 7.
• Deploy a virtualization solution for the company’s developers.
• Implement coexistence between the users in Fabrikam and the users in Blue Yonder Airlines.
EXISTING ENVIRONMENT
One user in each office runs a point-of-sale (POS) application named Appl. App 1 requires access to a
local USB device and only runs on Windows XP Service Pack 3 (SP3).
Blue Yonder Airlines has a finance department.
Business Goals
Blue Yonder Airlines plans to acquire a company named Fabrikam, Inc. Fabrikam has an Active
Directory forest named fabrikam.com. Fabrikam.com contains only domain controllers that run
Windows Server 2003 Service Pack 2 (SP2).
Fabrikam.com contains multiple Web servers that are secured by using certificates. All server
certificates are issued by the internal CA of Fabrikam.
Existing Active Directory Environment
The network contains an Active Directory forest named blueyonderairlines.com. The forest contains
a single domain.
The domain contains domain controllers that run Windows Server 2008. The domain controllers are
configured as shown in the following table.
The forest contains a single Active Directory site. A subnet object is defined for each office.
The forest contains a certification authority (CA).
Existing Network Infrastructure
Each office has a file server and a print server.
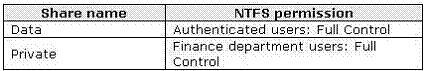
The main office has a file server named Server1. The shared folders on Server1 are configured as
shown in the following table.
Blueyonderairlines.com has a standalone DFS root named \\serverl\corp that contains a link named
sales. Replicas of \\serverl\corp\sales are deployed in each office.
Current Administration Model
Administrators manage the Active Directory objects by using the Active Directory module for
Windows Power Shell.
TECHNICAL REQUIREMENTS
Blue Yonder Airlines must meet the following requirements for coexistence between Blue Yonder
Airlines and Fabrikam:
• Only specific users in Fabrikam must be allowed to access specific shares in
blueyonderairlines.com.
• Users in Blue Yonder Airlines must be able to access the secure Web servers in fabrikam.com
without receiving a warning message about the certificate.
• All administrators in Blue Yonder Airlines must be able to administer Active Directory objects
in fabrikam.com by using their default administrative tools.
The corporate security policy states that when a domain controller fails, all references to the domain
controller must be permanently removed from the domain before the domain controller is replaced.
Blue Yonder Airlines must meet the following virtualization requirements:
• Ensure that each developer can create and manage his own virtual machine (VM).
• Prevent the developers from configuring the settings of other developers’ VMs.
• Prevent the developers from creating VMs that use more than 2 GB of memory,
• Minimize the amount of bandwidth used when users access files over WAN links.
###EndCaseStudy###
You need to recommend a certificate strategy that meets the company’s technical requirements.
What should you recommend?
You need to ensure that when you connect to the Default Web Site by using Computer1, you do not receive a cert
Your network contains a server named Web1 that runs Windows Server 2008 R2 Service Pack 1
(SP1). Web1 has the Web Server (IIS) server role installed. You configure the Default Web Site to use
a self-signed certificate. You have a client computer named Computer1 that runs Windows 7. You
need to ensure that when you connect to the Default Web Site by using Computer1, you do not
receive a certificate error. What should you do?
Which tool should you use?
Your network contains an Active directory domain named fabrikam.com. The domain contains a
Web server named Web1 that runs Windows Server 2008 R2. Web1 contains three Web sites named
Corp, Sales, and Marketing. You discover that the CPU utilization of web1 is abnormally high. You
need to identify the amount of memory that each Web site is using. Which tool should you use?
You need to ensure that all of the client computers can use certificates issued by Server5 if Server5 fails
###BeginCaseStudy###
Case Study: 9
Humongous Insurance
COMPANY OVERVIEW
Humongous Insurance has a main office and 20 branch offices. The main office is located in New
York. The branch offices are located throughout North America. The main office has 8,000 users.
Each branch office has 2 to 250 users.
PLANNED CHANGES
Humongous Insurance plans to implement the following changes:
• Deploy one Read-only Domain Controller (RODC) to Site3 and one RODC to Site4.
• Issue certificates to the users in Contoso. The certificates will be based on custom certificate
templates.
• Deploy a Remote Desktop Services (RDS) infrastructure that will contain 10 Remote Desktop
servers. Users will connect to all Remote Desktop servers from the Internet by using port 443.
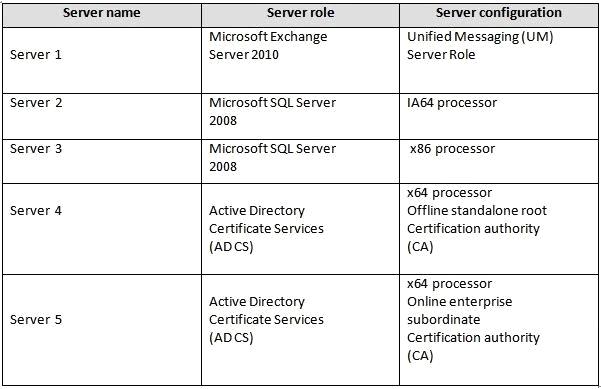
EXISTING ENVIRONMENT
The network contains the servers configured as shown in the following table.
Business Goals
All of the strategies for deploying physical servers and virtual servers must meet the Microsoft
guidelines for product support.
Existing Active Directory Environment
The network contains a single Active Directory forest named humongousinsurance.com. The
functional level of the forest is Windows Server 2008 R2.
The Active Directory sites are shown in the exhibit. (Click the Case Study Exhibit button.)
Existing Network Infrastructure
Humongous Insurance issues smart cards to administrators. Smart cards are not required for logon.
Humongous Insurance acquires a company named Contoso, Ltd.
REQUIREMENTS
Technical Requirements
All of the users in Contoso must be able to enroll for certificates by using the Public Key
Infrastructure (PKI) of Humongous Insurance.
Humongous Insurance must meet the following requirements for managing Group Policy objects
(GPOs):
• Minimize administrative effort.
• Support offline editing of the GPOs.
• Retain multiple versions of the GPOs.
Security Requirements
Only administrators who log on by using smart cards must be able to manage objects in Active
Directory.
The corporate security policy states that a forest trust to any other forest must not exist.
CASE STUDY EXHIBIT
Click the case study exhibit button to view the exhibit.
###EndCaseStudy###
You need to ensure that all of the client computers can use certificates issued by Server5 if Server5
fails. What should you do?
You need to prevent the error message from appearing on Computer1
Your network contains a Key Management Service (KMS) host named Server 1 On a client computer
named Computer1 that runs Windows 7, you discover the following error message in the Event log:
“0xC004F00F The Software Licensing Server reported that the hardware ID binding is beyond level of
tolerance.” You need to prevent the error message from appearing on Computer1. What should you
do from Computer1?
What should you include in the recommendation?
###BeginCaseStudy###
Case Study: 9
Humongous Insurance
COMPANY OVERVIEW
Humongous Insurance has a main office and 20 branch offices. The main office is located in New
York. The branch offices are located throughout North America. The main office has 8,000 users.
Each branch office has 2 to 250 users.
PLANNED CHANGES
Humongous Insurance plans to implement the following changes:
• Deploy one Read-only Domain Controller (RODC) to Site3 and one RODC to Site4.
• Issue certificates to the users in Contoso. The certificates will be based on custom certificate
templates.
• Deploy a Remote Desktop Services (RDS) infrastructure that will contain 10 Remote Desktop
servers. Users will connect to all Remote Desktop servers from the Internet by using port 443.
EXISTING ENVIRONMENT
The network contains the servers configured as shown in the following table.
Business Goals
All of the strategies for deploying physical servers and virtual servers must meet the Microsoft
guidelines for product support.
Existing Active Directory Environment
The network contains a single Active Directory forest named humongousinsurance.com. The
functional level of the forest is Windows Server 2008 R2.
The Active Directory sites are shown in the exhibit. (Click the Case Study Exhibit button.)
Existing Network Infrastructure
Humongous Insurance issues smart cards to administrators. Smart cards are not required for logon.
Humongous Insurance acquires a company named Contoso, Ltd.
REQUIREMENTS
Technical Requirements
All of the users in Contoso must be able to enroll for certificates by using the Public Key
Infrastructure (PKI) of Humongous Insurance.
Humongous Insurance must meet the following requirements for managing Group Policy objects
(GPOs):
• Minimize administrative effort.
• Support offline editing of the GPOs.
• Retain multiple versions of the GPOs.
Security Requirements
Only administrators who log on by using smart cards must be able to manage objects in Active
Directory.
The corporate security policy states that a forest trust to any other forest must not exist.
CASE STUDY EXHIBIT
Click the case study exhibit button to view the exhibit.
###EndCaseStudy###
You need to recommend a PKI strategy for Contoso that meets the company’s technical
requirements.
What should you include in the recommendation?
Which Diskpart command should you run?
Your network contains a server named Server1 that runs Windows Server 2008 R2 Service Pack 1
(SP1). You need to ensure that when you connect a drive that contains volumes to Server1, the
volumes are NOT assigned a drive letter automatically. Which Diskpart command should you run?
You need to ensure that Server1 continues to use Server2 as a Remote Desktop license server
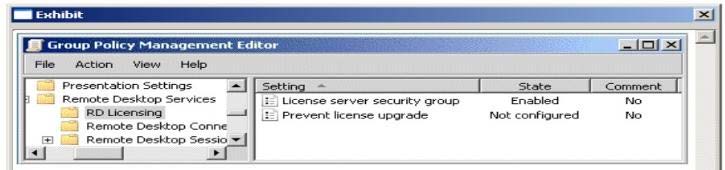
Your network contains an Active Directory domain named conloso.com. The domain contains two
member servers named Server1 and Server2. Server1 has the Remote Desktop Session Host (RD
Session Host) role service installed. Server2 has the Remote Desktop Licensing (RD Licensing) role
service installed. Server1 is configured to use Server2 as a Remote Desktop license server. A domain
administrator configures the Default Domain Policy as shown in the exhibit. (Click the Exhibit
button.)
You need to ensure that Server1 continues to use Server2 as a Remote Desktop license server. What
should you do?