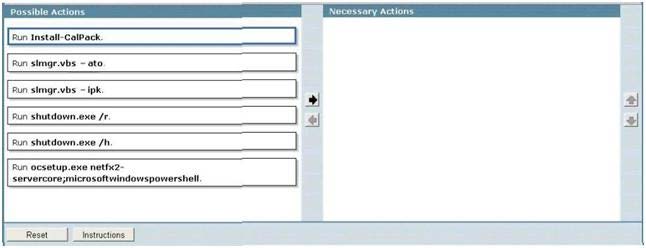
You need to configure VM1 to use Disk l as a pass-through disk
DRAG DROP
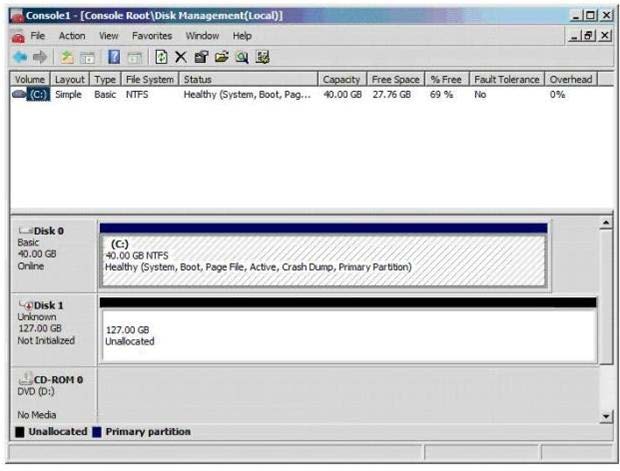
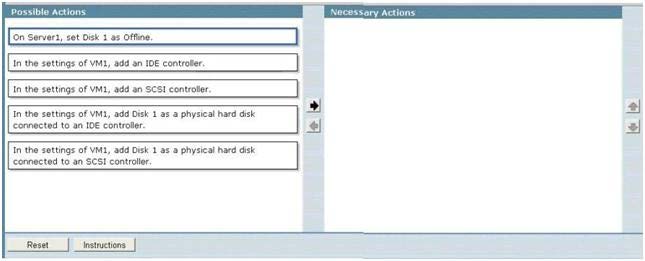
Your network contains a Hyper-V host named Server1 that runs Windows Server 2008 R2. The disks
on Server1 are configured as shown in the exhibit. (Click the Exhibit button.)
You create a virtual machine (VM) named VM1. You deploy Windows Server 2008 R2 to VM1. You
need to configure VM1 to use Disk l as a pass-through disk. The solution must minimize downtime
on VM1. What should you do? To answer, move the appropriate actions from the Possible Actions
list to the Necessary Actions area and arrange them in the correct order.
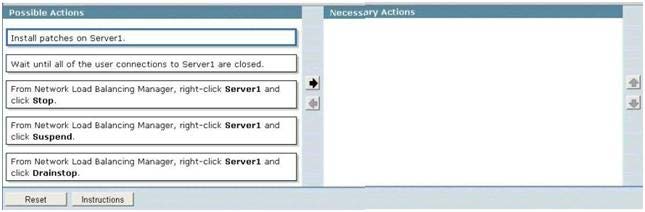
You need to install Windows updates on Server1 to meet the following requirements:
DRAG DROP
Your network contains a Network Load Balancing (NLB) cluster named NLB01. NLB01 contains two
servers named Server1 and Server2 that run Windows Server 2008 B2.
You need to install Windows updates on Server1 to meet the following requirements:
•Prevent new connections to Server1 while the updates are installed.
• Provide connected users with the ability to complete their session on server1 before the updates
are installed.
What should you do?
To answer, move the appropriate actions from the Possible Actions list to the Necessary Actions area
and arrange them in the correct order.
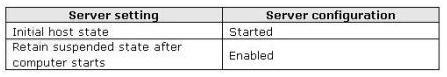
You need to activate Windows Server 2008 R2 on the server
DRAG DROP
Your network uses Multiple Activation Key (MAX) licenses. A network technician performs a Server
Core installation of Windows Server 2008 R2. Dunng the installation, the technician does not enter
the license key. You need to activate Windows Server 2008 R2 on the server. What should you do?
To answer, move the appropriate actions from the Possible Actions list to the Necessary Actions area
and arrange them in the correct order.
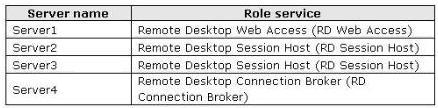
You need to ensure that the RemoteApp programs are listed on the RD Web Access Web page on Server1
Your network contains four servers that run Windows Server 2008 R2. The servers are configured as
shown in the following table:
Server2 and Server3 are configured as RemoteApp sources on Server4. You need to ensure that the
RemoteApp programs are listed on the RD Web Access Web page on Server1. What should you do?
What should you include in the recommendation?
###BeginCaseStudy###
Case Study: 3
Proseware Inc
COMPANY OVERVIEW
Proseware Inc. is an international software development company that has three offices. The offices
are located in New York, London, and Washington.
PLANNED CHANGES
Proseware plans to deploy a remote access solution and a centralized Windows Update solution on
all client computers.
Proseware plans to consolidate 10 physical servers in a virtualization solution.
EXISTING ENVIRONMENT
The network contains client computers that run either Windows XP Service Pack 3 (SP3), Windows
Vista Service Pack 2 (SP2). or Windows 7.
The network contains 10 client computers that run a UNIX-based operating system.
Existing Active Directory Environment
The Active Directory contains the two domains shown in the exhibit. (Click the Case Study Exhibits
button.)
The relevant domain controllers are configured as shown in the following table.
The Active Directory sites are configured as shown in the exhibit. (Click the Case Study Exhibits
button.)
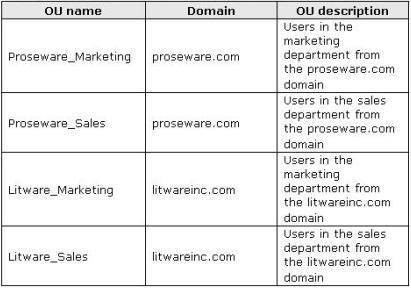
Proseware has a sales department and a marketing department.
The relevant organizational units (OU) are configured as shown in the following table.
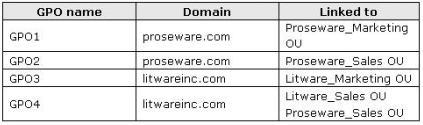
The relevant Group Policy objects (GPO) are configured as shown in the following table.
Existing Network Infrastructure
Users from litwareinc.com regularly travel to the Washington office.
All of the client computers that authenticate to the domain controllers in the Washington office run
Windows 7.
All servers are configured to audit logons by an administrator.
Each office has a Windows Server Update Services (WSUS) server. Each WSUS server is managed
independently.
REQUIREMENTS
Technical Requirements
Proseware must meet the following technical requirements:
• Remote network access must be encrypted.
• A report that contains the following information must be generated monthly:
• All of the client computers that failed to install the latest Windows updates.
• All of the Windows updates that are currently installed on the client computers.
• Each failed attempt to log on to the servers by using the local Administrator account.
• The hardware and software assets on the client computers must be inventoried.
• Only client computers that have the latest antivirus definitions must be able to access the
network.
• Client computers that run the UNIX-based operating system must be able to connect to
shares on the file servers.
• If DC3.proseware.com fails, all of the client computers in proseware.com that are in the
Washington site must authenticate to a domain controller in the New York office.
User Requirements
Users in litewareinc.com report that it takes a long time to log on when they travel to the
Washington office.
Users in the Proseware.com sales department report that it takes a long time to log on when they
travel to the New York office. You verify that the users in the other Proseware departments log on in
an acceptable amount of time.
###EndCaseStudy###
You need to recommend a reporting solution that meets the company’s technical requirements.
What should you include in the recommendation?
Which feature should you configure?
Your network contains an Active Directory domain named fabnkam.com. The domain contains a
Web Server named Web1 that runs Windows Server 2008 R2. You create a new site named Site1.
You need to ensure that when a user enters a URL on site1 for a resource that does not exist, a
custom web page displays. Which feature should you configure?
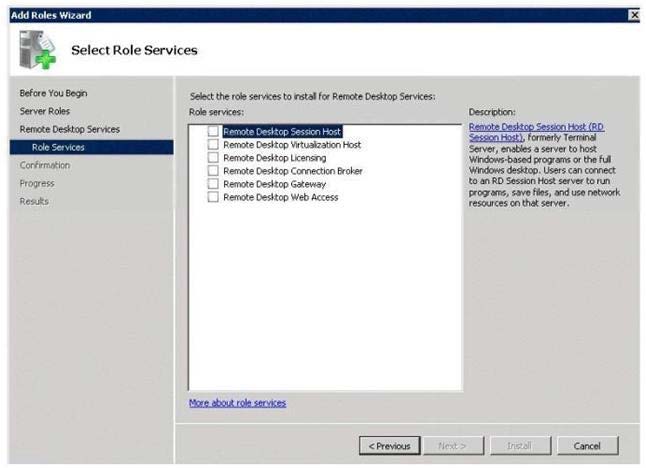
Which role service or role services from the Add Roles Wizard should you install on Server3?
HOTSPOT
Your network contains three servers named Server1, Server2, and Server3. Server3 is located on a
perimeter network. Users connect to Server1 and Server2 to run RemoteApp programs. You need to
ensure that remote users can run the RemoteApp programs on Server1 and Server?. The solution
must minimize the number of ports that must be opened on the internal firewall. Which role service
or role services from the Add Roles Wizard should you install on Server3? To answer, select the
appropriate role service or role services in the answer are a. Select only the required role service or
role services.
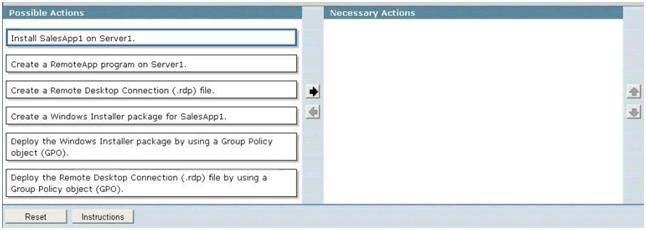
You need to ensure that when users in the sales department open files that have the .abc file extension…
DRAG DROP
Your network contains two servers. The servers are configured as shown in the following table All
client computers run the 32-bit version of Windows Vista. Your company purchases a new sales
application named SalesAppl. SalesAppl is a 64-bit application. SalesAppl is associated with the .abc
file I extension. You need to ensure that when users in the sales department open files that have the
.abc file extension, SalesAppl automatically opens. What should you do? To answer, move the
appropriate actions from the Possible Actions list to the Necessary Actions area and arrange them in
the correct order.
What should you include in the recommendation?
###BeginCaseStudy###
Case Study: 3
Proseware Inc
COMPANY OVERVIEW
Proseware Inc. is an international software development company that has three offices. The offices
are located in New York, London, and Washington.
PLANNED CHANGES
Proseware plans to deploy a remote access solution and a centralized Windows Update solution on
all client computers.
Proseware plans to consolidate 10 physical servers in a virtualization solution.
EXISTING ENVIRONMENT
The network contains client computers that run either Windows XP Service Pack 3 (SP3), Windows
Vista Service Pack 2 (SP2). or Windows 7.
The network contains 10 client computers that run a UNIX-based operating system.
Existing Active Directory Environment
The Active Directory contains the two domains shown in the exhibit. (Click the Case Study Exhibits
button.)
The relevant domain controllers are configured as shown in the following table.
The Active Directory sites are configured as shown in the exhibit. (Click the Case Study Exhibits
button.)
Proseware has a sales department and a marketing department.
The relevant organizational units (OU) are configured as shown in the following table.
The relevant Group Policy objects (GPO) are configured as shown in the following table.
Existing Network Infrastructure
Users from litwareinc.com regularly travel to the Washington office.
All of the client computers that authenticate to the domain controllers in the Washington office run
Windows 7.
All servers are configured to audit logons by an administrator.
Each office has a Windows Server Update Services (WSUS) server. Each WSUS server is managed
independently.
REQUIREMENTS
Technical Requirements
Proseware must meet the following technical requirements:
• Remote network access must be encrypted.
• A report that contains the following information must be generated monthly:
• All of the client computers that failed to install the latest Windows updates.
• All of the Windows updates that are currently installed on the client computers.
• Each failed attempt to log on to the servers by using the local Administrator account.
• The hardware and software assets on the client computers must be inventoried.
• Only client computers that have the latest antivirus definitions must be able to access the
network.
• Client computers that run the UNIX-based operating system must be able to connect to
shares on the file servers.
• If DC3.proseware.com fails, all of the client computers in proseware.com that are in the
Washington site must authenticate to a domain controller in the New York office.
User Requirements
Users in litewareinc.com report that it takes a long time to log on when they travel to the
Washington office.
Users in the Proseware.com sales department report that it takes a long time to log on when they
travel to the New York office. You verify that the users in the other Proseware departments log on in
an acceptable amount of time.
###EndCaseStudy###
You need to recommend an Active Directory solution for the Washington office that meets the
company’s technical requirements. What should you include in the recommendation?
Which feature should you configure from Internet Information Services (IIS) Manager?
Your network contains a Web server named Server1 that runs Windows Server 2008 R2. The
network contains two subnets named Subnet1 and Subnet2. Server1 contains a Web site named
Site1. You need to prevent Server1 from responding to requests that originate from subnet2. Which
feature should you configure from Internet Information Services (IIS) Manager?