You need to prevent DHCP clients from receiving IP addresses that are currently in use on the network
You have a DHCP server that runs Windows Server 2008 R2. You restore the DHCP
database by using a recent backup. You need to prevent DHCP clients from receiving IP
addresses that are currently in use on the network. What should you do?
What should you identify?
HOTSPOT
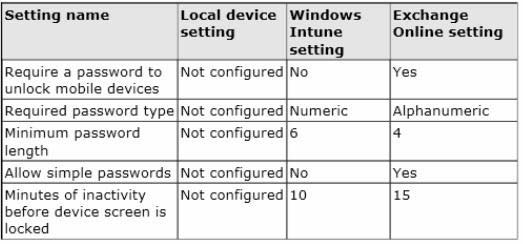
Your company has several Windows RT 8.1 devices that run. The devices connect to Exchange Online in
Microsoft Office 365 and to Windows Intune for device management.
The security policies of Office 365 and Windows Intune are configured as shown in the following table.
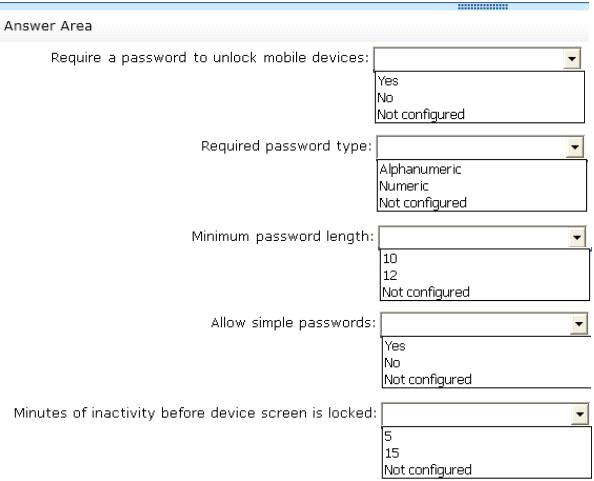
You need to identify the effective settings on the Windows RT devices.
What should you identify? (To answer, select the appropriate effective configuration for each setting in the
answer area.)
Which two actions should you perform?
Your network uses IPv4. You install a server that runs Windows Server 2008 R2 at a branch
office. The server is configured with two network interfaces. You need to configure routing
on the server at the branch office. Which two actions should you perform? (Each correct
answer presents part of the solution. Choose two.)
Which command should you run on WKS1?
Your company has an IPv4 Ethernet network. A router named R1 connects your segment to
the Internet. A router named R2 joins your subnet with a segment named Private1. The
Private1 segment has a network address of 10.128.4.0/26. Your computer named WKS1
requires access to servers on the Private1 network. The WKS1 computer configuration is as
shown in the following table. WKS1 is unable to connect to the Private1 network by using
the current configuration. You need to add a persistent route for the Private1 network to the
routing table on WKS1. Which command should you run on WKS1?
You need to immediately disable all incoming connections to the server
Your network contains one Active Directory domain. You have a member server that runs
Windows Server 2008 R2. You need to immediately disable all incoming connections to the
server. What should you do?
You need to configure the Endpoint Protection client not to scan the C:\TestApp folder for the computers in th
Your network contains an Active Directory domain. All client computers run Windows 8.1 Enterprise.
Microsoft System Center 2012 Endpoint Protection is deployed to all of the computers by using the default
settings contained in the Default Antimalware Policy.
The users in the research department report that a folder named C:\TestApp must not be scanned by the
Endpoint Protection client.
You need to configure the Endpoint Protection client not to scan the C:\TestApp folder for the computers in
the research department only.
What should you do first?
You need to ensure that users can connect to Server1
Your network consists of a single Active Directory domain. The domain contains a server
named Server1 that runs Windows Server 2008 R2. All client computers run Windows 7. All
computers are members of the Active Directory domain. You assign the Secure Server
(Require Security) IPsec policy to Server1 by using a Group Policy object (GPO). Users
report that they fail to connect to Server1. You need to ensure that users can connect to
Server1. All connections to Server1 must be encrypted. What should you do?
Which two actions should you perform?
Your company uses Active Directory-integrated DNS. Users require access to the Internet.
You run a network capture. You notice the DNS server is sending DNS name resolution
queries to a server named f.root-servers.net. You need to prevent the DNS server from
sending queries to f.rootservers. net. The server must be able to resolve names for Internet
hosts. Which two actions should you perform? (Each correct answer presents part of the
solution. Choose two.)
Which tool should you use?
You have several client computers that run Windows 7 Enterprise.
You plan to configure the computers to dual-boot to Windows 8.1 Enterprise by using a native-boot VHD.
You have a VHD file that contains an installation of Windows 8.1 Enterprise.
You need to inject several device drivers into the VHD file.
Which tool should you use?
Which two actions should you perform?
Your company has a single Active Directory forest that has six domains. All DNS servers in
the forest run Windows Server 2008 R2. You need to ensure that all public DNS queries are
channeled through a single-caching-only DNS server. Which two actions should you
perform? (Each correct answer presents part of the solution. Choose two.)