You need to ensure that users in contoso.com can access the mailboxes in the Exchange organization
DRAG DROP
Your network contains two Active Directory forests. The forests contain domain controllers that run
Windows Server 2008 R2. The forests are configured as shown in the following table.
An external trust exists from contoso.com to fabrikam.com.
You plan to deploy an Exchange Server 2010 Service Pack 1 (SP1) organization. The organization will
contain Mailbox servers in fabrikam.com. You need to ensure that users in contoso.com can access
the mailboxes in the Exchange organization. What should you do?
To answer, move the appropriate actions from the list of actions to the answer area and arrange
them in the correct order.
What should you include in the recommendation?
You have an Exchange Server 2010 Service Pack 1 (SP1) organization. The network contains two
Active Directory sites named Site1 and Site2. Site1 contains an Edge Transport server named
Server1. Each site has a direct connection to the Internet. Server1 receives all of the email sent to
the Exchange organization from the Internet. You need to recommend a solution that meets the
following requirements:
• Prevents an email message from being returned to the sender if Server1 fails.
• Prevents an email message from being returned to the sender if the connection to the Internet in
Site1 fails.
What should you include in the recommendation? (Each correct answer presents a complete
solution. Choose all that apply.)
Which tool or cmdlet should you use to perform each task?
DRAG DROP
You have an Exchange Server 2010 Service Pack 1 (SP1) organization. You need to recommend tools
that can be used to monitor the Exchange organization. Which tool or cmdlet should you use to
perform each task?
To answer, drag the appropriate tool or cmdlet to the correct task in the answer area.
What should you include in the plan?
You are a messaging administrator for a company named Contoso, Ltd. Contoso has a UNIX-based
email system for the contoso.com SMTP domain. Contoso has a perimeter network and an internal
network.
Corporate security policy states that only TCP port 25 is allowed from the perimeter network to the
internal network.
You plan to change the UNIX-based email infrastructure to Exchange Server 2010 Service Pack 1
(SP1). The UNIX-based infrastructure will not coexist with the Exchange Server 2010 SP1
organization.
Contoso has a partner company named Fabrikam, Inc. All recipients at Fabrikam are hosted on an
Exchange Server 2003 organization. Fabrikam uses the fabrikam.com SMTP domain.
You need to plan the configuration of the Exchange Server 2010 SP1 accepted domains to meet the
following requirements:
• Ensure that all email messages sent to Contoso and Fabrikam can be received by the Contoso
servers.
• Ensure that the Contoso servers can then relay the email messages to the Fabrikam servers.
• Prevent email messages sent to Fabrikam recipients from being relayed to the internal network.
What should you include in the plan? (Each correct answer presents part of the solution. Choose all
that apply.)
Which management roles should you assign?
DRAG DROP
You plan to implement Exchange Server 2010 Service Pack 1 (SP1) in your organization.
You need to plan the security model for the organization to meet the following requirements:
• A minimum number of permissions must be assigned.
• Members of a group named Support must be able to configure all the properties of mailboxenabled users, distribution groups, and servers.
• Members of a security group named IT-Consultants must be able to generate a report that
contains information about mailbox-enabled users, distribution groups, and server configurations.
Which management roles should you assign?
To answer, drag the appropriate management roles to the correct security group in the answer area.
Which TCP ports should you identify?
DRAG DROP
Your network contains an Active Directory domain named contoso.com. All domain controllers run
Windows Server 2008 R2. The network contains an Exchange Server 2010 Service Pack 1 (SP1)
organization. Corporate security policy states that all user connections from the Internet to the
Exchange organization must be encrypted. You plan to deploy the following client connection
methods for the Exchange organization:
• POP3
• IMAP4
• Outlook Web App
• Outlook Anywhere
You need to identify which firewall ports must be opened to meet the security policy. The solution
must use the default TCP ports of each connection method. Which TCP ports should you identify?
To answer, drag the appropriate TCP port to the correct connection method in the answer area.
You need to configure the Exchange environment to meet the following requirements
Your network contains an Active Directory domain named contoso.com. All domain controllers run
Windows Server 2008 R2. The network contains two Active Directory sites named Los Angeles and
San Francisco. All traffic to and from the Internet is routed through Los Angeles. You have an
Exchange Server 2010 Service Pack 1 (SP1) organization that contains three servers. The servers are
configured as shown in the following table.
Server1 has Windows Integrated Authentication enabled for the default OWA virtual directory. You
need to configure the Exchange environment to meet the following requirements. Ensure that users
can access their mailbox from the Internet by using the light version of Outlook Web App. Prevent
users from being prompted for a username and a password when they connect to Outlook Web App
from a domain-joined client computer on the internal network. What should you do? (Choose all
that apply.)
Which service or services should you identify?
You have an Exchange Server 2010 Service Pack 1 (SP1) organization. You plan to implement a
redundancy solution for Exchange dependencies. You need to identify which services must be
available for the Exchange organization to function correctly for all users. Which service or services
should you identify? (Choose all that apply.)
Which technologies should you identify?
DRAG DROP
You have an Exchange Server 2010 Service Pack 1 (SP1) organization named contoso.com.
You are planning the anti-spam infrastructure for the organization. You need to identify which
Exchange Server 2010 SP1 anti-spam technologies achieve your anti-spam requirements. Which
technologies should you identify?
To answer, drag the appropriate anti-spam technology to the correct anti-spam requirement in the
answer area.
What should you recommend running before you activate the mailbox databases?
DRAG DROP
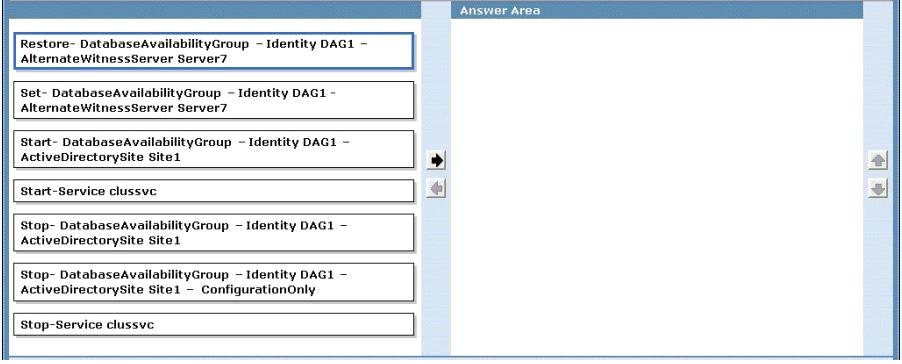
You have an Exchange Server 2010 Service Pack 1 (SP1) organization that contains four servers. The
servers are configured as shown in the following table.
Datacenter Activation Coordination (DAC) node is enabled for DAG1, The file share witness is located
on Servers and the alternate file share witness is located on Server7. Domain controllers are
available in both sites. You need to recommend a solution to activate the databases in Site2 if Site1
becomes unavailable for an extended period of time. What should you recommend running before
you activate the mailbox databases?
To answer, move the appropriate actions from the list of actions to the answer area and arrange
them in the correct order.