You need to identify which security role must be assigned to which user.
DRAG DROP
Your network contains a System Center 2012 Configuration Manager environment.
Three users named User1, User2, and User3 will perform the following tasks:
User1 will review software metering data and inventory reports.
User2 will deploy Applications and create alerts.
User3 will create configuration items.
You need to identify which security role must be assigned to which user.
What should you identify?
To answer, drag the appropriate security role to the correct user in the answer are
a Each security role may be used once, more than once, or not at all. Additionally, you may need to
drag the split bar between panes or scroll to view content.
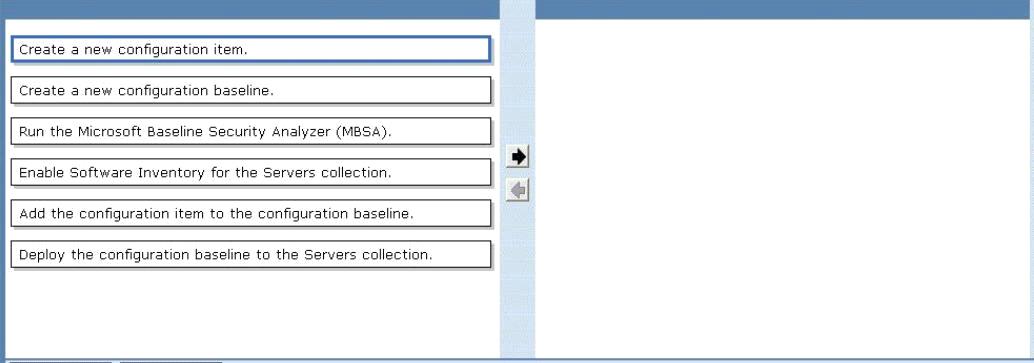
You need to inventory the desktop settings of the All Marketing Users collection
DRAG DROP
Your network contains a System Center 2012 Configuration Manager environment.
You create a collection named All Marketing Users.
You need to inventory the desktop settings of the All Marketing Users collection.
What should you do?
To answer, move the four appropriate actions from the list of actions to the answer area and
arrange them in the correct order.
You need to identify which servers do not comply with the security policy
DRAG DROP
Your network contains a System Center 2012 Configuration Manager environment.
Your company has a security policy that contains mandatory registry settings for all servers.
You have a collection named Servers that contains all of the servers.
You need to identify which servers do not comply with the security policy.
What should you do?
To answer, move the four appropriate actions from the list of actions to the answer area and
arrange them in the correct order.
Which log files should you review?
HOTSPOT
You deploy System Center 2012 R2 Configuration Manager Service Pack 1 (SP1) to a server named
Server1.
Configuration Manager manages all of the client computers, including a computer named Client1.
A hardware inventory cycle is initiated on Client1.
You need to identify which Inventory classes were collected on Client1 and when the inventory was
added to the site database.
Which log files should you review? To answer, select the appropriate options in the answer area.
Which two log files should you review?
Your network contains a System Center 2012 R2 Configuration Manager Service Pack 1 (SP1)
environment.
In Default Client Settings, you enable Hardware Inventory and Software Inventory.
You discover that a group of client computers fails to report hardware inventory dat
a. The client computers report software inventory data.
You verify that Configuration Manager can deploy applications to the client computers.
You need to identify what is causing the reporting issue.
Which two log files should you review? Each correct answer presents part of the solution.
You need to ensure that the .abc files are inventoried
Your network contains a System Center 2012 R2 Configuration Manager Service Pack 1 (SP1)
environment.
Software Inventory and Hardware Inventory are enabled for all of the client computers.
All of the client computers have an application named App1 installed. App1 saves files to the C:\ABC
folder. All of the files saved by App1 have a file name extension of .abc.
You configure Software Inventory to inventory all of the files that have the .abc extension and the
.exe extension.
After six months, you discover that some of the client computers fail to inventory .abc files.
All of the client computers inventory .exe files.
You need to ensure that the .abc files are inventoried.
What should you do?
Which object should you configure in Configuration Manager?
You have a System Center 2012 R2 Configuration Manager Service Pack 1 (SP1) deployment.
Hardware inventory is enabled for all of the Configuration Manager clients.
You create a device collection named Finance. All of the client computers in the finance department
are members of the Finance collection.
You need to include Trusted Platform Module (TPM) information in the hardware inventory of the
finance department computers.
Which object should you configure in Configuration Manager?
Which two tasks should you perform?
You have Windows 8.1 images that are rebuilt quarterly and imported to System Center 2012 R2
Configuration Manager Service Pack 1 (SP1).
The Microsoft Deployment Toolkit (MDT) 2013 is integrated with Configuration Manager.
You need to reduce the network security risks when the images are deployed by using Operating
System Deployment (OSD).
Which two tasks should you perform? Each correct answer presents a complete solution.
Which four actions should you perform in sequence?
DRAG DROP
Your network contains a single Active Directory domain named contoso.com. System Center 2012 R2
Configuration Manager Service Pack 1 (SP1) is deployed to contoso.com.
You have a Windows 8.1 operating system image named Image1 in Configuration Manager. Image1
has the data source of \\server1.contoso.com\source\Image1.wim.
New client computers are deployed by using Image1.
You have an application named App1. App1 is a configuration utility that must be installed by using a
Windows Installer (MSI) package.
You need to ensure that App1 is included in all future deployments of Image1.
Which four actions should you perform in sequence? To answer, move the appropriate actions from
the list of actions to the answer area and arrange them in the correct order.
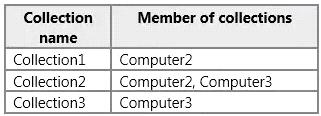
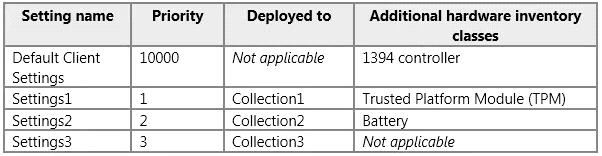
You need to identify which additional hardware inventory classes will be collected from Computer2 and Computer
DRAG DROP
You have a System Center 2012 R2 Configuration Manager Service Pack 1 (SP1) deployment. The
deployment includes the collections described in the following table.
Configuration Manager has the client settings configured as shown in the following table.
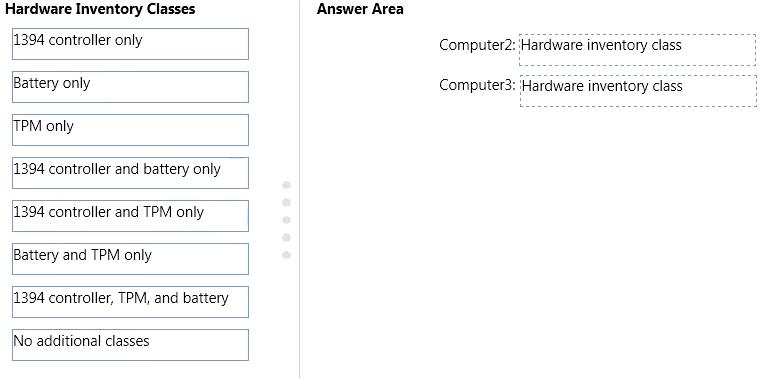
You need to identify which additional hardware inventory classes will be collected from Computer2
and Computer3.
What should you identify? To answer, drag the appropriate hardware inventory classes to the
correct computers. Each hardware inventory class may be used once, more than once, or not at all.
You may need to drag the split bar between panes or scroll to view content.