Fabrikam plans to exchange sensitive information with
###BeginCaseStudy###
Testlet 1
Topic 1, Fabrikam, Inc
Overview
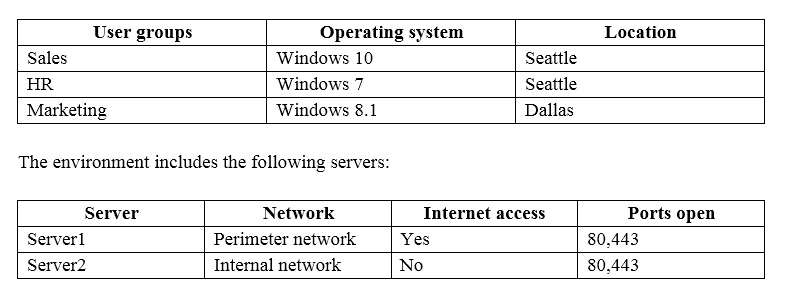
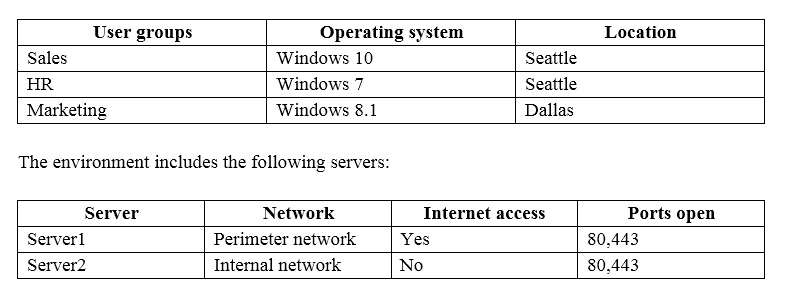
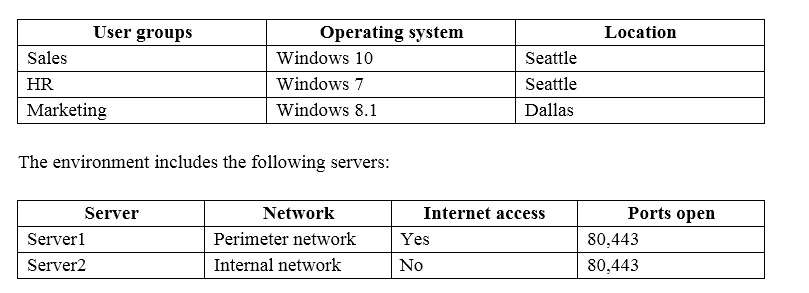
Fabrikam, Inc., is a pharmaceutical company located in Europe. The company has 5,000 users.
The company is finalizing plans to deploy an Exchange Server 2013 organization.
The company has offices in Paris and Amsterdam.
Existing Environment
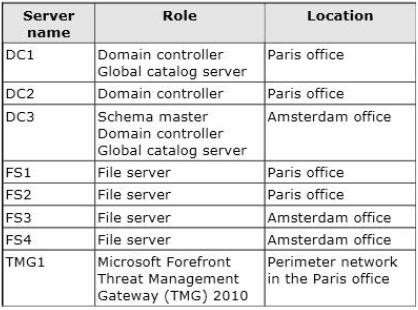
Active Directory Environment
The network contains an Active Directory domain named fabrikam.com. An Active Directory
site exists for each office.
Network Infrastructure
The roles and location of each server are configured as shown in the following table.
Client computers run either Windows 7 or Windows 8 and have Microsoft Office 2010 installed.
The Paris office uses the 192.168.1.0/24 IP range. The Amsterdam office uses the 192.168.2.0/24 IP range.
The offices connect to each other by using a high-speed, low-latency WAN link. Each office has a 10-Mbps
connection to the Internet.
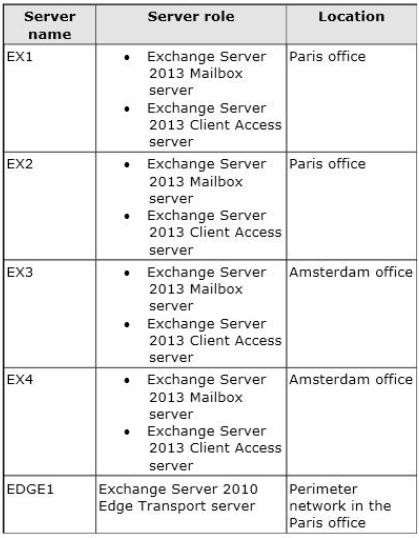
Planned Exchange Infrastructure
The company plans to deploy five servers that run Exchange Server. The servers will be configured as shown
in the following table.
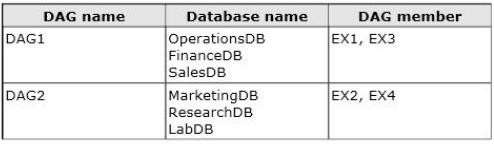
The company plans to have mailbox databases replicated in database availability groups (DAGs). The mailbox
databases and DAGs will be configured as shown in the following table.
DAG1 will use FS1 as a file share witness. DAG2 will use FS3 as a file share witness.
You plan to create the following networks on each DAG:
A dedicated replication network named DAGNET1
A MAPI network named DAGNET2
All replication traffic will run on DAGNET1. All client connections will run on DAGNET2. Client connections must
never occur on DAGNET1. Replication traffic must only occur on DAGNET2 if DAGNET1 is unavailable.
Each Exchange Server 2013 Mailbox server will be configured to have two network adapters.
The following two mailbox databases will not be replicated as part of the DAGs:
A mailbox database named AccountingDB that is hosted on EX1
A mailbox database named TempStaffDB that is hosted on EX4EDGE1 will have an Edge Subscription configured, with both EX1 and EX2 as targets.
Requirements
Planned Changes
An external consultant reviews the Exchange Server 2013 deployment plan and identifies the following areas of
concern:
The DAGs will not be monitored.
Multiple Edge Transport servers are required to prevent the potential for a single point of failure.
Technical Requirements
Fabrikam must meet the following technical requirements:
Email must be evaluated for SPAM before the email enters the internal network.
Production system patching must minimize downtime to achieve the highest possible service to users.
Users must be able to use the Exchange Control Panel to autonomously join and disjoin their department’s
distribution lists.
Users must be able to access all Internet-facing Exchange Server services by using the names of
mail.fabrikam.com and autodiscover.fabrikam.com.
The company establishes a partnership with another company named A. Datum Corporation. A Datum uses the SMTP suffix adatum.com for all email addresses. Fabrikam plans to exchange sensitive information with A.
Datum and requires that the email messages sent between the two companies be encrypted. The solution must
use Domain Security.
Users in the research and development (R&D) department must be able to view only the mailboxes of the users
in their department from Microsoft Outlook. The users in all of the other departments must be prevented from
viewing the mailboxes of the R&D users from Outlook.
Administrators plan to produce HTML reports that contain information about recent status changes to the
mailbox databases.
Fabrikam is evaluating whether to abort its plan to implement an Exchange Server 2010 Edge Transport server
and to implement a Client Access server in the Paris office instead. The Client Access server will have antispam agents installed.
###EndCaseStudy###
You need to recommend a design that meets the technical requirements for communication between Fabrikam and A Datum.
Which three actions should you perform in fabrikam.com? (Each correct answer presents part of the solution. Choose three.)
Fabrikam plans to exchange sensitive information with
###BeginCaseStudy###
Testlet 1
Topic 1, Fabrikam, Inc
Overview
Fabrikam, Inc., is a pharmaceutical company located in Europe. The company has 5,000 users.
The company is finalizing plans to deploy an Exchange Server 2013 organization.
The company has offices in Paris and Amsterdam.
Existing Environment
Active Directory Environment
The network contains an Active Directory domain named fabrikam.com. An Active Directory
site exists for each office.
Network Infrastructure
The roles and location of each server are configured as shown in the following table.
Client computers run either Windows 7 or Windows 8 and have Microsoft Office 2010 installed.
The Paris office uses the 192.168.1.0/24 IP range. The Amsterdam office uses the 192.168.2.0/24 IP range.
The offices connect to each other by using a high-speed, low-latency WAN link. Each office has a 10-Mbps
connection to the Internet.
Planned Exchange Infrastructure
The company plans to deploy five servers that run Exchange Server. The servers will be configured as shown
in the following table.
The company plans to have mailbox databases replicated in database availability groups (DAGs). The mailbox
databases and DAGs will be configured as shown in the following table.
DAG1 will use FS1 as a file share witness. DAG2 will use FS3 as a file share witness.
You plan to create the following networks on each DAG:
A dedicated replication network named DAGNET1
A MAPI network named DAGNET2
All replication traffic will run on DAGNET1. All client connections will run on DAGNET2. Client connections must
never occur on DAGNET1. Replication traffic must only occur on DAGNET2 if DAGNET1 is unavailable.
Each Exchange Server 2013 Mailbox server will be configured to have two network adapters.
The following two mailbox databases will not be replicated as part of the DAGs:
A mailbox database named AccountingDB that is hosted on EX1
A mailbox database named TempStaffDB that is hosted on EX4EDGE1 will have an Edge Subscription configured, with both EX1 and EX2 as targets.
Requirements
Planned Changes
An external consultant reviews the Exchange Server 2013 deployment plan and identifies the following areas of
concern:
The DAGs will not be monitored.
Multiple Edge Transport servers are required to prevent the potential for a single point of failure.
Technical Requirements
Fabrikam must meet the following technical requirements:
Email must be evaluated for SPAM before the email enters the internal network.
Production system patching must minimize downtime to achieve the highest possible service to users.
Users must be able to use the Exchange Control Panel to autonomously join and disjoin their department’s
distribution lists.
Users must be able to access all Internet-facing Exchange Server services by using the names of
mail.fabrikam.com and autodiscover.fabrikam.com.
The company establishes a partnership with another company named A. Datum Corporation. A Datum uses the SMTP suffix adatum.com for all email addresses. Fabrikam plans to exchange sensitive information with A.
Datum and requires that the email messages sent between the two companies be encrypted. The solution must
use Domain Security.
Users in the research and development (R&D) department must be able to view only the mailboxes of the users
in their department from Microsoft Outlook. The users in all of the other departments must be prevented from
viewing the mailboxes of the R&D users from Outlook.
Administrators plan to produce HTML reports that contain information about recent status changes to the
mailbox databases.
Fabrikam is evaluating whether to abort its plan to implement an Exchange Server 2010 Edge Transport server
and to implement a Client Access server in the Paris office instead. The Client Access server will have antispam agents installed.
###EndCaseStudy###
You need to recommend which task is required to prepare Active Directory for the planned Exchange Server 2013 implementation.
What should you recommend?
Fabrikam plans to exchange sensitive information with
###BeginCaseStudy###
Testlet 1
Topic 1, Fabrikam, Inc
Overview
Fabrikam, Inc., is a pharmaceutical company located in Europe. The company has 5,000 users.
The company is finalizing plans to deploy an Exchange Server 2013 organization.
The company has offices in Paris and Amsterdam.
Existing Environment
Active Directory Environment
The network contains an Active Directory domain named fabrikam.com. An Active Directory
site exists for each office.
Network Infrastructure
The roles and location of each server are configured as shown in the following table.
Client computers run either Windows 7 or Windows 8 and have Microsoft Office 2010 installed.
The Paris office uses the 192.168.1.0/24 IP range. The Amsterdam office uses the 192.168.2.0/24 IP range.
The offices connect to each other by using a high-speed, low-latency WAN link. Each office has a 10-Mbps
connection to the Internet.
Planned Exchange Infrastructure
The company plans to deploy five servers that run Exchange Server. The servers will be configured as shown
in the following table.
The company plans to have mailbox databases replicated in database availability groups (DAGs). The mailbox
databases and DAGs will be configured as shown in the following table.
DAG1 will use FS1 as a file share witness. DAG2 will use FS3 as a file share witness.
You plan to create the following networks on each DAG:
A dedicated replication network named DAGNET1
A MAPI network named DAGNET2
All replication traffic will run on DAGNET1. All client connections will run on DAGNET2. Client connections must
never occur on DAGNET1. Replication traffic must only occur on DAGNET2 if DAGNET1 is unavailable.
Each Exchange Server 2013 Mailbox server will be configured to have two network adapters.
The following two mailbox databases will not be replicated as part of the DAGs:
A mailbox database named AccountingDB that is hosted on EX1
A mailbox database named TempStaffDB that is hosted on EX4EDGE1 will have an Edge Subscription configured, with both EX1 and EX2 as targets.
Requirements
Planned Changes
An external consultant reviews the Exchange Server 2013 deployment plan and identifies the following areas of
concern:
The DAGs will not be monitored.
Multiple Edge Transport servers are required to prevent the potential for a single point of failure.
Technical Requirements
Fabrikam must meet the following technical requirements:
Email must be evaluated for SPAM before the email enters the internal network.
Production system patching must minimize downtime to achieve the highest possible service to users.
Users must be able to use the Exchange Control Panel to autonomously join and disjoin their department’s
distribution lists.
Users must be able to access all Internet-facing Exchange Server services by using the names of
mail.fabrikam.com and autodiscover.fabrikam.com.
The company establishes a partnership with another company named A. Datum Corporation. A Datum uses the SMTP suffix adatum.com for all email addresses. Fabrikam plans to exchange sensitive information with A.
Datum and requires that the email messages sent between the two companies be encrypted. The solution must
use Domain Security.
Users in the research and development (R&D) department must be able to view only the mailboxes of the users
in their department from Microsoft Outlook. The users in all of the other departments must be prevented from
viewing the mailboxes of the R&D users from Outlook.
Administrators plan to produce HTML reports that contain information about recent status changes to the
mailbox databases.
Fabrikam is evaluating whether to abort its plan to implement an Exchange Server 2010 Edge Transport server
and to implement a Client Access server in the Paris office instead. The Client Access server will have antispam agents installed.
###EndCaseStudy###
An administrator recommends removing EDGE1 from the implementation plan and adding a new Client Access
server named CAS-8 instead.
You need to identify which anti-spam feature will NOT be available on CAS-8.
Which anti-spam feature should you identify?
Fabrikam plans to exchange sensitive information with
###BeginCaseStudy###
Testlet 1
Topic 1, Fabrikam, Inc
Overview
Fabrikam, Inc., is a pharmaceutical company located in Europe. The company has 5,000 users.
The company is finalizing plans to deploy an Exchange Server 2013 organization.
The company has offices in Paris and Amsterdam.
Existing Environment
Active Directory Environment
The network contains an Active Directory domain named fabrikam.com. An Active Directory
site exists for each office.
Network Infrastructure
The roles and location of each server are configured as shown in the following table.
Client computers run either Windows 7 or Windows 8 and have Microsoft Office 2010 installed.
The Paris office uses the 192.168.1.0/24 IP range. The Amsterdam office uses the 192.168.2.0/24 IP range.
The offices connect to each other by using a high-speed, low-latency WAN link. Each office has a 10-Mbps
connection to the Internet.
Planned Exchange Infrastructure
The company plans to deploy five servers that run Exchange Server. The servers will be configured as shown
in the following table.
The company plans to have mailbox databases replicated in database availability groups (DAGs). The mailbox
databases and DAGs will be configured as shown in the following table.
DAG1 will use FS1 as a file share witness. DAG2 will use FS3 as a file share witness.
You plan to create the following networks on each DAG:
A dedicated replication network named DAGNET1
A MAPI network named DAGNET2
All replication traffic will run on DAGNET1. All client connections will run on DAGNET2. Client connections must
never occur on DAGNET1. Replication traffic must only occur on DAGNET2 if DAGNET1 is unavailable.
Each Exchange Server 2013 Mailbox server will be configured to have two network adapters.
The following two mailbox databases will not be replicated as part of the DAGs:
A mailbox database named AccountingDB that is hosted on EX1
A mailbox database named TempStaffDB that is hosted on EX4EDGE1 will have an Edge Subscription configured, with both EX1 and EX2 as targets.
Requirements
Planned Changes
An external consultant reviews the Exchange Server 2013 deployment plan and identifies the following areas of
concern:
The DAGs will not be monitored.
Multiple Edge Transport servers are required to prevent the potential for a single point of failure.
Technical Requirements
Fabrikam must meet the following technical requirements:
Email must be evaluated for SPAM before the email enters the internal network.
Production system patching must minimize downtime to achieve the highest possible service to users.
Users must be able to use the Exchange Control Panel to autonomously join and disjoin their department’s
distribution lists.
Users must be able to access all Internet-facing Exchange Server services by using the names of
mail.fabrikam.com and autodiscover.fabrikam.com.
The company establishes a partnership with another company named A. Datum Corporation. A Datum uses the SMTP suffix adatum.com for all email addresses. Fabrikam plans to exchange sensitive information with A.
Datum and requires that the email messages sent between the two companies be encrypted. The solution must
use Domain Security.
Users in the research and development (R&D) department must be able to view only the mailboxes of the users
in their department from Microsoft Outlook. The users in all of the other departments must be prevented from
viewing the mailboxes of the R&D users from Outlook.
Administrators plan to produce HTML reports that contain information about recent status changes to the
mailbox databases.
Fabrikam is evaluating whether to abort its plan to implement an Exchange Server 2010 Edge Transport server
and to implement a Client Access server in the Paris office instead. The Client Access server will have antispam agents installed.
###EndCaseStudy###
HOTSPOT
You need to recommend which configurations must be set for each network.
Which configurations should you recommend?
To answer, select the appropriate configurations for each network in the answer area.
Hot Area:
Which additional port should you open?
This is a case study. Case studies are not timed separately. You can use as much exam times as you would
like to complete each case. However, there may be additional studies and sections on this exam. You must
manage your time to ensure that you are able to complete all questions included on this exam in the time
provided.
To answer the questions included in a case study, you will need to reference information that is provided in the
case study. Case studies might contain exhibits and other resources that provide more information about the
scenario that is described in the case study. Each question is independent of the other questions in this case
study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to
make changes before you move to the next section of the exam. After you begin a new section, you cannot
return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore
the content of the case study before you answer the questions. Clicking these buttons displays information such
as business requirements, existing environment, and problem statements. If the case study has an All
Information tab, note that the information displayed is identical to the information displayed on the subsequent
tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
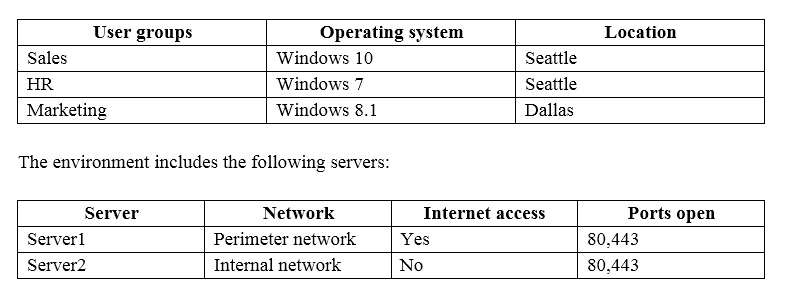
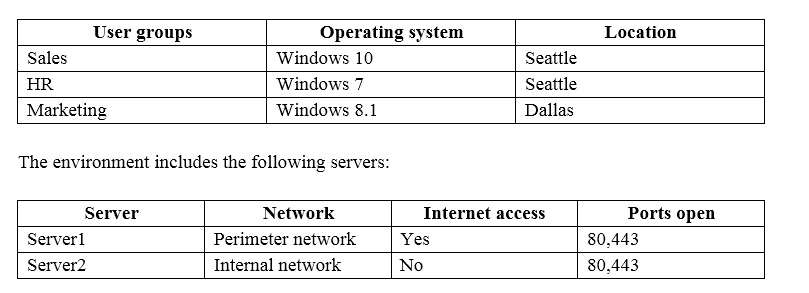
You are the system administrator for an insurance company named Contoso, Ltd. The company has an onpremises Active Directory Services (AD DS) domain named contoso.com, and a Microsoft Office 365
environment. You deploy the following operating systems across the enterprise:
You configure removable storage usage auditing for all Dallas devices.
Contractors
You hire 25 contractors. The contractors must use their own devices to access Microsoft SharePoint Online
sites in the company’s Office 365 environment. They must use Windows BitLocker and store a recovery key in
Microsoft OneDrive.User synchronization and authentication
You need to implement synchronization between the on-premises AD DS domain and the Office 365
environment. The solution must use the latest supported Microsoft technologies.
Users must be able to reset their own passwords by using the Microsoft Office 365 portal. When a user resets
their Office 365 password, the password for the user’s on-premises AD DS account must also reset.
Users must be able to sign in to Office 365 by using their AD DS credentials.
Security
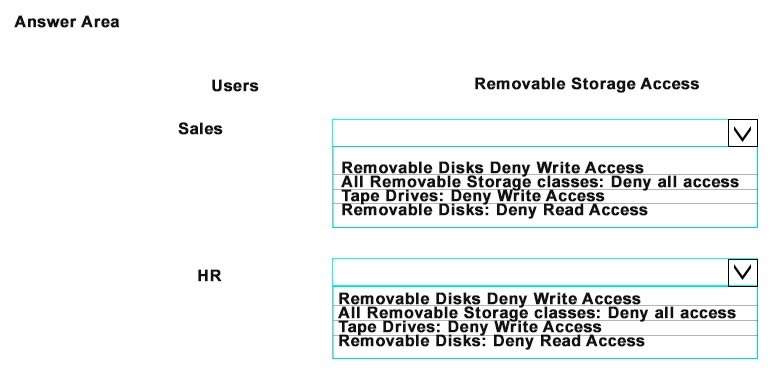
You must prevent all users in Seattle except Sales users from using any removable devices. Sales users must
be able to fully access local attached tape drives. Sales users must be prevented from writing to removable
drives.
Technical requirements
General
You deploy a new application to the devices in Seattle. Sales department users in Seattle run an application
that only works on devices that run windows 7.
You deploy a new display driver to all devices in Dallas.
Backup and Recovery
You create system images for all devices that run Windows 7. You must create a new system image each time
you update these devices. You schedule file versioning for these devices to occur at 09:00 and 17:00 each day
on Monday through Friday.
All devices that run Windows 10 must back up the C:\\CompanyDoes folder to a network drive.
You must configure all devices that run Windows 8.1 to use a recovery drive.
Monitoring
You must review and take action on any alerts for Active Directory Federation Services (AD FS) application.
You must create detailed views of AD FS log on patterns. You must minimize the number of open firewall ports.
You must monitor audit events for all devices used by the Marketing user group.
Problem Statements
User1 makes frequent changes to a Microsoft Excel workbook each day. Today at 12:00, User overwrites the
existing document on a device that runs Windows 7.
Users in Seattle report a variety of computer issues. You must use the quickest method to revert the devices to
a working state. Users in Dallas also report issues. You must correct the issues that are interfering with existing
applications or files.
A Sales department user overwrites a version of a Word document on their device.
You need to configure Azure Active Directory (AD) Connect Health.
Which additional port should you open?
You need to monitor the company’s environment according…
HOTSPOT
This is a case study. Case studies are not timed separately. You can use as much exam times as you would
like to complete each case. However, there may be additional studies and sections on this exam. You must
manage your time to ensure that you are able to complete all questions included on this exam in the time
provided.
To answer the questions included in a case study, you will need to reference information that is provided in the
case study. Case studies might contain exhibits and other resources that provide more information about the
scenario that is described in the case study. Each question is independent of the other questions in this case
study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to
make changes before you move to the next section of the exam. After you begin a new section, you cannot
return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore
the content of the case study before you answer the questions. Clicking these buttons displays information such
as business requirements, existing environment, and problem statements. If the case study has an All
Information tab, note that the information displayed is identical to the information displayed on the subsequent
tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
You are the system administrator for an insurance company named Contoso, Ltd. The company has an onpremises Active Directory Services (AD DS) domain named contoso.com, and a Microsoft Office 365
environment. You deploy the following operating systems across the enterprise:
You configure removable storage usage auditing for all Dallas devices.
Contractors
You hire 25 contractors. The contractors must use their own devices to access Microsoft SharePoint Online
sites in the company’s Office 365 environment. They must use Windows BitLocker and store a recovery key in
Microsoft OneDrive.
User synchronization and authentication
You need to implement synchronization between the on-premises AD DS domain and the Office 365
environment. The solution must use the latest supported Microsoft technologies.
Users must be able to reset their own passwords by using the Microsoft Office 365 portal. When a user resets
their Office 365 password, the password for the user’s on-premises AD DS account must also reset.
Users must be able to sign in to Office 365 by using their AD DS credentials.
Security
You must prevent all users in Seattle except Sales users from using any removable devices. Sales users must
be able to fully access local attached tape drives. Sales users must be prevented from writing to removable
drives.
Technical requirements
General
You deploy a new application to the devices in Seattle. Sales department users in Seattle run an application
that only works on devices that run windows 7.
You deploy a new display driver to all devices in Dallas.
Backup and Recovery
You create system images for all devices that run Windows 7. You must create a new system image each time
you update these devices. You schedule file versioning for these devices to occur at 09:00 and 17:00 each day
on Monday through Friday.
All devices that run Windows 10 must back up the C:\\CompanyDoes folder to a network drive.
You must configure all devices that run Windows 8.1 to use a recovery drive.Monitoring
You must review and take action on any alerts for Active Directory Federation Services (AD FS) application.
You must create detailed views of AD FS log on patterns. You must minimize the number of open firewall ports.
You must monitor audit events for all devices used by the Marketing user group.
Problem Statements
User1 makes frequent changes to a Microsoft Excel workbook each day. Today at 12:00, User overwrites the
existing document on a device that runs Windows 7.
Users in Seattle report a variety of computer issues. You must use the quickest method to revert the devices to
a working state. Users in Dallas also report issues. You must correct the issues that are interfering with existing
applications or files.
A Sales department user overwrites a version of a Word document on their device.
You need to monitor the company’s environment according to the technical requirements.
What should you do? To answer, select the appropriate option from each list in the answer area.
Hot Area:
How should you configure the Group Policy Objects (GPOs)?
HOTSPOT
This is a case study. Case studies are not timed separately. You can use as much exam times as you would
like to complete each case. However, there may be additional studies and sections on this exam. You must
manage your time to ensure that you are able to complete all questions included on this exam in the time
provided.
To answer the questions included in a case study, you will need to reference information that is provided in the
case study. Case studies might contain exhibits and other resources that provide more information about the
scenario that is described in the case study. Each question is independent of the other questions in this case
study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to
make changes before you move to the next section of the exam. After you begin a new section, you cannot
return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explorethe content of the case study before you answer the questions. Clicking these buttons displays information such
as business requirements, existing environment, and problem statements. If the case study has an All
Information tab, note that the information displayed is identical to the information displayed on the subsequent
tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
You are the system administrator for an insurance company named Contoso, Ltd. The company has an onpremises Active Directory Services (AD DS) domain named contoso.com, and a Microsoft Office 365
environment. You deploy the following operating systems across the enterprise:
You configure removable storage usage auditing for all Dallas devices.
Contractors
You hire 25 contractors. The contractors must use their own devices to access Microsoft SharePoint Online
sites in the company’s Office 365 environment. They must use Windows BitLocker and store a recovery key in
Microsoft OneDrive.
User synchronization and authentication
You need to implement synchronization between the on-premises AD DS domain and the Office 365
environment. The solution must use the latest supported Microsoft technologies.
Users must be able to reset their own passwords by using the Microsoft Office 365 portal. When a user resets
their Office 365 password, the password for the user’s on-premises AD DS account must also reset.
Users must be able to sign in to Office 365 by using their AD DS credentials.
Security
You must prevent all users in Seattle except Sales users from using any removable devices. Sales users must
be able to fully access local attached tape drives. Sales users must be prevented from writing to removable
drives.
Technical requirements
General
You deploy a new application to the devices in Seattle. Sales department users in Seattle run an application
that only works on devices that run windows 7.
You deploy a new display driver to all devices in Dallas.Backup and Recovery
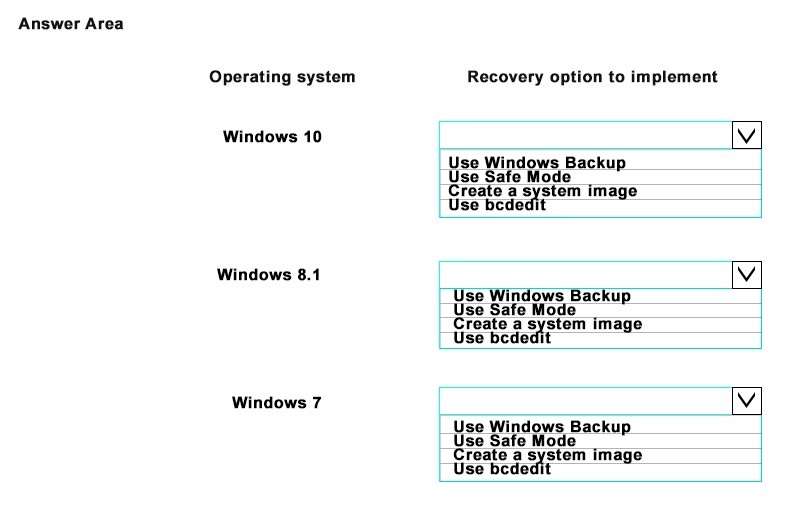
You create system images for all devices that run Windows 7. You must create a new system image each time
you update these devices. You schedule file versioning for these devices to occur at 09:00 and 17:00 each day
on Monday through Friday.
All devices that run Windows 10 must back up the C:\\CompanyDoes folder to a network drive.
You must configure all devices that run Windows 8.1 to use a recovery drive.
Monitoring
You must review and take action on any alerts for Active Directory Federation Services (AD FS) application.
You must create detailed views of AD FS log on patterns. You must minimize the number of open firewall ports.
You must monitor audit events for all devices used by the Marketing user group.
Problem Statements
User1 makes frequent changes to a Microsoft Excel workbook each day. Today at 12:00, User overwrites the
existing document on a device that runs Windows 7.
Users in Seattle report a variety of computer issues. You must use the quickest method to revert the devices to
a working state. Users in Dallas also report issues. You must correct the issues that are interfering with existing
applications or files.
A Sales department user overwrites a version of a Word document on their device.
You need to implement the required Group Policy settings.
How should you configure the Group Policy Objects (GPOs)? To answer, select the appropriate option from
each list in the answer area.
Hot Area:
Which recovery options should you implement?
HOTSPOT
This is a case study. Case studies are not timed separately. You can use as much exam times as you would
like to complete each case. However, there may be additional studies and sections on this exam. You mustmanage your time to ensure that you are able to complete all questions included on this exam in the time
provided.
To answer the questions included in a case study, you will need to reference information that is provided in the
case study. Case studies might contain exhibits and other resources that provide more information about the
scenario that is described in the case study. Each question is independent of the other questions in this case
study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to
make changes before you move to the next section of the exam. After you begin a new section, you cannot
return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore
the content of the case study before you answer the questions. Clicking these buttons displays information such
as business requirements, existing environment, and problem statements. If the case study has an All
Information tab, note that the information displayed is identical to the information displayed on the subsequent
tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
You are the system administrator for an insurance company named Contoso, Ltd. The company has an onpremises Active Directory Services (AD DS) domain named contoso.com, and a Microsoft Office 365
environment. You deploy the following operating systems across the enterprise:
You configure removable storage usage auditing for all Dallas devices.
Contractors
You hire 25 contractors. The contractors must use their own devices to access Microsoft SharePoint Online
sites in the company’s Office 365 environment. They must use Windows BitLocker and store a recovery key in
Microsoft OneDrive.
User synchronization and authentication
You need to implement synchronization between the on-premises AD DS domain and the Office 365
environment. The solution must use the latest supported Microsoft technologies.
Users must be able to reset their own passwords by using the Microsoft Office 365 portal. When a user resets
their Office 365 password, the password for the user’s on-premises AD DS account must also reset.Users must be able to sign in to Office 365 by using their AD DS credentials.
Security
You must prevent all users in Seattle except Sales users from using any removable devices. Sales users must
be able to fully access local attached tape drives. Sales users must be prevented from writing to removable
drives.
Technical requirements
General
You deploy a new application to the devices in Seattle. Sales department users in Seattle run an application
that only works on devices that run windows 7.
You deploy a new display driver to all devices in Dallas.
Backup and Recovery
You create system images for all devices that run Windows 7. You must create a new system image each time
you update these devices. You schedule file versioning for these devices to occur at 09:00 and 17:00 each day
on Monday through Friday.
All devices that run Windows 10 must back up the C:\\CompanyDoes folder to a network drive.
You must configure all devices that run Windows 8.1 to use a recovery drive.
Monitoring
You must review and take action on any alerts for Active Directory Federation Services (AD FS) application.
You must create detailed views of AD FS log on patterns. You must minimize the number of open firewall ports.
You must monitor audit events for all devices used by the Marketing user group.
Problem Statements
User1 makes frequent changes to a Microsoft Excel workbook each day. Today at 12:00, User overwrites the
existing document on a device that runs Windows 7.
Users in Seattle report a variety of computer issues. You must use the quickest method to revert the devices to
a working state. Users in Dallas also report issues. You must correct the issues that are interfering with existing
applications or files.
A Sales department user overwrites a version of a Word document on their device.
You need to plan the backup and recovery options for the devices in the environment.
Which recovery options should you implement? To answer, select the appropriate option from each list in the
answer area.
Hot Area:
Which two actions should you perform?
This is a case study. Case studies are not timed separately. You can use as much exam times as you would
like to complete each case. However, there may be additional studies and sections on this exam. You must
manage your time to ensure that you are able to complete all questions included on this exam in the timeprovided.
To answer the questions included in a case study, you will need to reference information that is provided in the
case study. Case studies might contain exhibits and other resources that provide more information about the
scenario that is described in the case study. Each question is independent of the other questions in this case
study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to
make changes before you move to the next section of the exam. After you begin a new section, you cannot
return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore
the content of the case study before you answer the questions. Clicking these buttons displays information such
as business requirements, existing environment, and problem statements. If the case study has an All
Information tab, note that the information displayed is identical to the information displayed on the subsequent
tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
You are the system administrator for an insurance company named Contoso, Ltd. The company has an onpremises Active Directory Services (AD DS) domain named contoso.com, and a Microsoft Office 365
environment. You deploy the following operating systems across the enterprise:
You configure removable storage usage auditing for all Dallas devices.
Contractors
You hire 25 contractors. The contractors must use their own devices to access Microsoft SharePoint Online
sites in the company’s Office 365 environment. They must use Windows BitLocker and store a recovery key in
Microsoft OneDrive.
User synchronization and authentication
You need to implement synchronization between the on-premises AD DS domain and the Office 365
environment. The solution must use the latest supported Microsoft technologies.
Users must be able to reset their own passwords by using the Microsoft Office 365 portal. When a user resets
their Office 365 password, the password for the user’s on-premises AD DS account must also reset.
Users must be able to sign in to Office 365 by using their AD DS credentials.Security
You must prevent all users in Seattle except Sales users from using any removable devices. Sales users must
be able to fully access local attached tape drives. Sales users must be prevented from writing to removable
drives.
Technical requirements
General
You deploy a new application to the devices in Seattle. Sales department users in Seattle run an application
that only works on devices that run windows 7.
You deploy a new display driver to all devices in Dallas.
Backup and Recovery
You create system images for all devices that run Windows 7. You must create a new system image each time
you update these devices. You schedule file versioning for these devices to occur at 09:00 and 17:00 each day
on Monday through Friday.
All devices that run Windows 10 must back up the C:\\CompanyDoes folder to a network drive.
You must configure all devices that run Windows 8.1 to use a recovery drive.
Monitoring
You must review and take action on any alerts for Active Directory Federation Services (AD FS) application.
You must create detailed views of AD FS log on patterns. You must minimize the number of open firewall ports.
You must monitor audit events for all devices used by the Marketing user group.
Problem Statements
User1 makes frequent changes to a Microsoft Excel workbook each day. Today at 12:00, User overwrites the
existing document on a device that runs Windows 7.
Users in Seattle report a variety of computer issues. You must use the quickest method to revert the devices to
a working state. Users in Dallas also report issues. You must correct the issues that are interfering with existing
applications or files.
A Sales department user overwrites a version of a Word document on their device.
You need to configure access for the contractors.
Which two actions should you perform? Each correct answer presents part of the solution.
Which actions should you perform?
This is a case study. Case studies are not timed separately. You can use as much exam times as you would
like to complete each case. However, there may be additional studies and sections on this exam. You must
manage your time to ensure that you are able to complete all questions included on this exam in the time
provided.
To answer the questions included in a case study, you will need to reference information that is provided in the
case study. Case studies might contain exhibits and other resources that provide more information about the
scenario that is described in the case study. Each question is independent of the other questions in this case
study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and tomake changes before you move to the next section of the exam. After you begin a new section, you cannot
return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore
the content of the case study before you answer the questions. Clicking these buttons displays information such
as business requirements, existing environment, and problem statements. If the case study has an All
Information tab, note that the information displayed is identical to the information displayed on the subsequent
tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
You are the system administrator for an insurance company named Contoso, Ltd. The company has an onpremises Active Directory Services (AD DS) domain named contoso.com, and a Microsoft Office 365
environment. You deploy the following operating systems across the enterprise:
You configure removable storage usage auditing for all Dallas devices.
Contractors
You hire 25 contractors. The contractors must use their own devices to access Microsoft SharePoint Online
sites in the company’s Office 365 environment. They must use Windows BitLocker and store a recovery key in
Microsoft OneDrive.
User synchronization and authentication
You need to implement synchronization between the on-premises AD DS domain and the Office 365
environment. The solution must use the latest supported Microsoft technologies.
Users must be able to reset their own passwords by using the Microsoft Office 365 portal. When a user resets
their Office 365 password, the password for the user’s on-premises AD DS account must also reset.
Users must be able to sign in to Office 365 by using their AD DS credentials.
Security
You must prevent all users in Seattle except Sales users from using any removable devices. Sales users must
be able to fully access locally attached tape drives. Sales users must be prevented from writing to removable
drives.
Technical requirements
GeneralYou deploy a new application to the devices in Seattle. Sales department users in Seattle run an application
that only works on devices that run windows 7.
You deploy a new display driver to all devices in Dallas.
Backup and Recovery
You create system images for all devices that run Windows 7. You must create a new system image each time
you update these devices. You schedule file versioning for these devices to occur at 09:00 and 17:00 each day
on Monday through Friday.
All devices that run Windows 10 must back up the C:\\CompanyDoes folder to a network drive.
You must configure all devices that run Windows 8.1 to use a recovery drive.
Monitoring
You must review and take action on any alerts for Active Directory Federation Services (AD FS) applications.
You must create detailed views of AD FS log on patterns. You must minimize the number of open firewall ports.
You must monitor audit events for all devices used by the Marketing user group.
Problem Statements
User1 makes frequent changes to a Microsoft Excel workbook each day. Today at 12:00, User1 overwrites the
existing document on a device that runs Windows 7.
Users in Seattle report a variety of computer issues. You must use the quickest method to revert the devices to
a working state. Users in Dallas also report issues. You must correct the issues that are interfering with existing
applications or files.
A Sales department user overwrites a version of a Word document on their device.
You need to configure synchronization.
Which actions should you perform?