Which cmdlet should you use?
Your network contains one Active Directory domain named contoso.com. The forest functional level
is Windows Server 2012. All servers run Windows Server 2012 R2. All client computers run Windows
8.1.
The domain contains 10 domain controllers and a read-only domain controller (RODC) named
RODC01. All domain controllers and RODCs are hosted on a Hyper-V host that runs Windows Server
2012 R2.
You need to identify whether deleted objects can be recovered from the Active Directory Recycle
Bin.
Which cmdlet should you use?
Which cmdlet should you use?
Your network contains one Active Directory domain named contoso.com. The forest functional level
is Windows Server 2012. All servers run Windows Server 2012 R2. All client computers run Windows
8.1.
The domain contains 10 domain controllers and a read-only domain controller (RODC) named
RODC01. All domain controllers and RODCs are hosted on a Hyper-V host that runs Windows Server
2012 R2.
You need to identify which domain controllers are authorized to be cloned by using virtual domain
controller cloning.
Which cmdlet should you use?
Which two Group Policy settings should you configure?
HOTSPOT
Your network contains one Active Directory domain named contoso.com. The domain contains 10
file servers that run Windows Server 2012 R2.
You plan to enable BitLocker Drive Encryption (BitLocker) for the operating system drives of the file
servers.
You need to configure BitLocker policies for the file servers to meet the following requirements:
Ensure that all of the servers use a startup PIN for operating system drives encrypted with BitLocker.
Ensure that the BitLocker recovery key and recovery password are stored in Active Directory.
Which two Group Policy settings should you configure? To answer, select the appropriate settings in
the answer area.
Which cmdlet should you use?
Your network contains one Active Directory domain named contoso.com. The forest functional level
is Windows Server 2012. All servers run Windows Server 2012 R2. All client computers run Windows
8.1.
The domain contains 10 domain controllers and a read-only domain controller (RODC) named
RODC01. All domain controllers and RODCs are hosted on a Hyper-V host that runs Windows Server
2012 R2.
You need to identify which security principals are authorized to have their password cached on
RODC1.
Which cmdlet should you use?
You need to identify the domain-specific reference in GPO1
Your network contains two Active Directory forests named contoso.com and adatum.com. All
domain controllers run Windows Server 2012 R2.
The adatum.com domain contains a Group Policy object (GPO) named GPO1. An administrator from
adatum.com backs up GPO1 to a USB flash drive.
You have a domain controller named dc1.contoso.com. You insert the USB flash drive in
dc1.contoso.com.
You need to identify the domain-specific reference in GPO1.
What should you do?
Which type of record should you create?
You have a DNS server that runs Windows Server 2012 R2. The server hosts the zone for
contoso.com and is accessible from the Internet.
You need to create a DNS record for the Sender Policy Framework (SPF) to list the hosts that are
authorized to send email for contoso.com.
Which type of record should you create?
You need to ensure that Server02 synchronizes updates from Server01
You have two Windows Server Update Services (WSUS) servers named Server01 and Server02.
Server01 synchronizes from Microsoft Update. Server02 synchronizes updates from Server01. Both
servers are members of the same Active Directory domain.
You configure Server01 to require SSL for all WSUS metadata by using a certificate issued by an
enterprise root certification authority (CA).
You need to ensure that Server02 synchronizes updates from Server01.
What should you do on Server02?
Which two nodes should you configure?
HOTSPOT
Your network contains an Active Directory domain named contoso.com. The domain contains a
server named Server1 that runs Windows Server 2012 R2. Server1 has the File Server Resource
Manager role service installed.
You need to configure Server1 to meet the following requirements:
Ensure that old files in a folder named Folder1 are archived automatically to a folder named
Archive1.
Ensure that JPG files can always be saved to a local computer, even when a file screen exists.
Which two nodes should you configure? To answer, select the appropriate two nodes in the answer
area.
How should you configure the rules?
###BeginCaseStudy###
Case Study: 1
Fabrikam, Inc
Overview
General Overview
Fabrikam, Inc., is a plastics manufacturer.
Fabrikam has an Exchange Server organization that contains only servers that have Exchange
Server 2013 installed.
Physical Locations
Fabrikam has two main offices. The main offices are located in Tampa and Charlotte. The
company has 8, 000 users in each office.
Existing Environment
Active Directory Environment
Fabrikam has an Active Directory forest that contains one domain named fabrikam.com.
Each office is configured as an Active Directory site.
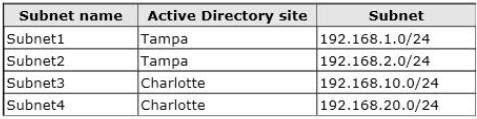
The network contains four subnets. The subnets are configured as shown in the following
table.
All of the traffic from Subnet1 is routable to Subnet3. All of the traffic from Subnet2 is
routable to Subnet4.
All client computers are on Subnet1 and Subnet3 only. Subnet 192.168.1.0/24 and subnet
192.168.10.0/24 are assigned as the MAPI network.
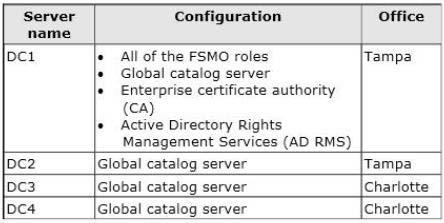
The network contains four domain controllers. The domain controllers are configured as
shown in the following table.
Network Infrastructure
The network contains the following components:
• Two 10-gigabits per second WAN links that connect the Tampa office
and the Charlotte office. The links have a latency of less than 15 ms.
• One IP-PBX that is located in the Tampa office. The IP-PBX can use
only unencrypted communications.
• An Internet connection in the Tampa office and an Internet connection
the Charlotte office.
Exchange Environment
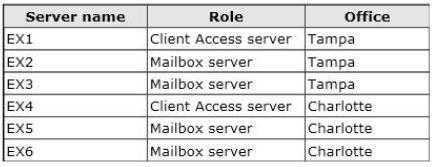
The network contains six servers that have Exchange Server 2013 installed. The servers are
configured as shown in the following table.
The Exchange Server environment has the following configurations:
• Two data loss prevention (DLP) policies named DLP_Finance and
DLP_PII. DLP_Finance is based on a template named Financial Data –
U.S. DLP_PII is based on a template named PII (U.S.).
• A mailbox database named UM that hosts only Unified Messaging
(UM)-enabled mailboxes and is replicated between the Mailbox
servers in the Tampa office only.
• A database availability group (DAG) named DAG1 that contains EX2,
EX3, EX5, and EX6. DAG1 is configured to use DHCP to obtain an IP
address.
• A Send connector named Tampa SMTP that uses SMTP1 as a smart
host. The cost of the Tampa SMTP connector is 10.
• Mailbox servers in the Tampa office that provide outbound SMTP
services to the Internet.
• A UM dial plan named UM1.
• An SMTP relay device named SMTP2 in the Charlotte office.
• An SMTP relay device named SMTP1 in the Tampa office.
• No client access services are published to the Internet.
Requirements
Exchange Server Issues
• The current Exchange Server environment has the following issues:
• Due to power failures, the Exchange servers unexpectedly fail, causing
databases to fail over. During the database failovers, the preferred
database is not activated, causing an unexpected distribution of active
databases.
• An IRM template named No Print or Screenshot is deployed, but the
template fails to prevent users from taking screenshots of email
messages.
Technical Requirements
You identify the following technical requirements:
• Assign a static IP address to DAG1.
• Block all personally identifiable information (PII) data and financial
data without exception.
• Prevent the forwarding of email messages sent by users who have a
value of Legal in their Department field.
• Ensure that the members of a group named HR1 can search all of the
mailboxes for sensitive email content.
• Use Information Rights Management (IRM) to protect all of the voice
mails left for the telephone number of the human resource (HR)
department.
• Implement an archiving policy that moves all of the email messages
from the mailbox folders to an Archive mailbox after 30 days and
permanently deletes all of the email messages after 365 days.
###EndCaseStudy###
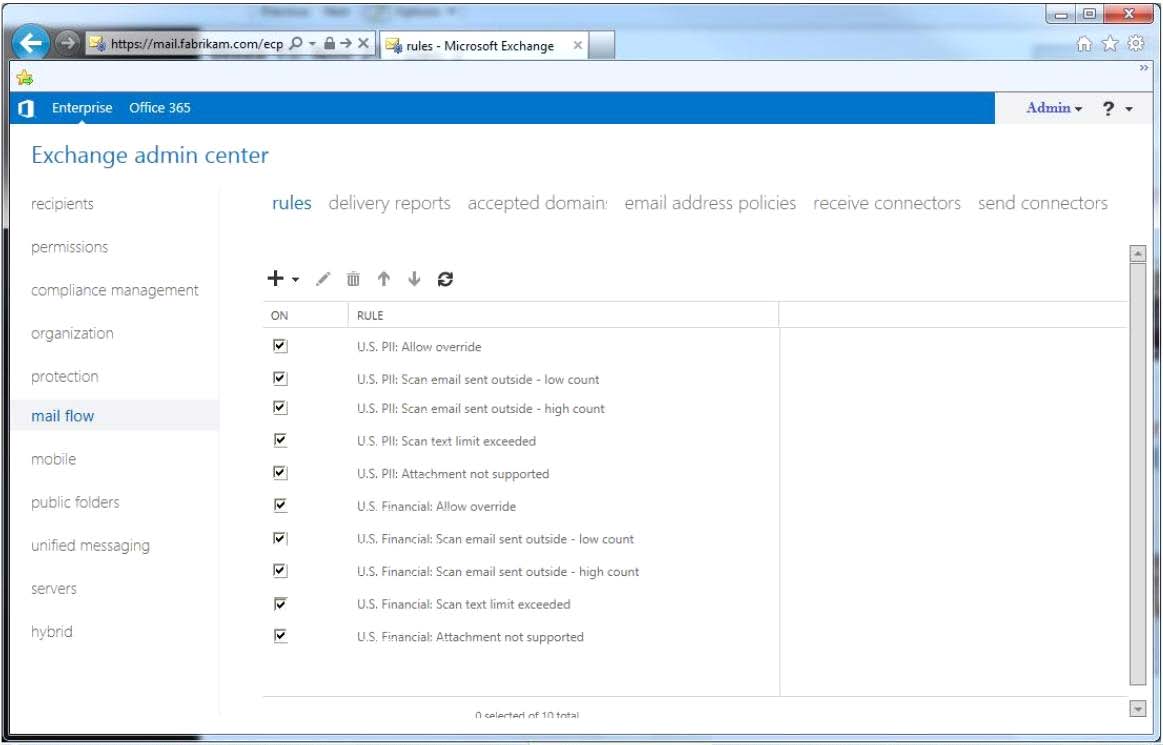
HOTSPOT
You need to configure transport rules to meet the technical requirements for the PII data and the
financial data.
How should you configure the rules?
To answer, disable the appropriate rule or rules in the answer area.
You need to ensure that all outbound email messages are sent from the Charlotte office during the planned outa
###BeginCaseStudy###
Case Study: 1
Fabrikam, Inc
Overview
General Overview
Fabrikam, Inc., is a plastics manufacturer.
Fabrikam has an Exchange Server organization that contains only servers that have Exchange
Server 2013 installed.
Physical Locations
Fabrikam has two main offices. The main offices are located in Tampa and Charlotte. The
company has 8, 000 users in each office.
Existing Environment
Active Directory Environment
Fabrikam has an Active Directory forest that contains one domain named fabrikam.com.
Each office is configured as an Active Directory site.
The network contains four subnets. The subnets are configured as shown in the following
table.
All of the traffic from Subnet1 is routable to Subnet3. All of the traffic from Subnet2 is
routable to Subnet4.
All client computers are on Subnet1 and Subnet3 only. Subnet 192.168.1.0/24 and subnet
192.168.10.0/24 are assigned as the MAPI network.
The network contains four domain controllers. The domain controllers are configured as
shown in the following table.
Network Infrastructure
The network contains the following components:
• Two 10-gigabits per second WAN links that connect the Tampa office
and the Charlotte office. The links have a latency of less than 15 ms.
• One IP-PBX that is located in the Tampa office. The IP-PBX can use
only unencrypted communications.
• An Internet connection in the Tampa office and an Internet connection
the Charlotte office.
Exchange Environment
The network contains six servers that have Exchange Server 2013 installed. The servers are
configured as shown in the following table.
The Exchange Server environment has the following configurations:
• Two data loss prevention (DLP) policies named DLP_Finance and
DLP_PII. DLP_Finance is based on a template named Financial Data –
U.S. DLP_PII is based on a template named PII (U.S.).
• A mailbox database named UM that hosts only Unified Messaging
(UM)-enabled mailboxes and is replicated between the Mailbox
servers in the Tampa office only.
• A database availability group (DAG) named DAG1 that contains EX2,
EX3, EX5, and EX6. DAG1 is configured to use DHCP to obtain an IP
address.
• A Send connector named Tampa SMTP that uses SMTP1 as a smart
host. The cost of the Tampa SMTP connector is 10.
• Mailbox servers in the Tampa office that provide outbound SMTP
services to the Internet.
• A UM dial plan named UM1.
• An SMTP relay device named SMTP2 in the Charlotte office.
• An SMTP relay device named SMTP1 in the Tampa office.
• No client access services are published to the Internet.
Requirements
Exchange Server Issues
• The current Exchange Server environment has the following issues:
• Due to power failures, the Exchange servers unexpectedly fail, causing
databases to fail over. During the database failovers, the preferred
database is not activated, causing an unexpected distribution of active
databases.
• An IRM template named No Print or Screenshot is deployed, but the
template fails to prevent users from taking screenshots of email
messages.
Technical Requirements
You identify the following technical requirements:
• Assign a static IP address to DAG1.
• Block all personally identifiable information (PII) data and financial
data without exception.
• Prevent the forwarding of email messages sent by users who have a
value of Legal in their Department field.
• Ensure that the members of a group named HR1 can search all of the
mailboxes for sensitive email content.
• Use Information Rights Management (IRM) to protect all of the voice
mails left for the telephone number of the human resource (HR)
department.
• Implement an archiving policy that moves all of the email messages
from the mailbox folders to an Archive mailbox after 30 days and
permanently deletes all of the email messages after 365 days.
###EndCaseStudy###
The Internet link in the Tampa office will be unavailable during the weekend.
You need to ensure that all outbound email messages are sent from the Charlotte office during the
planned outage.
What should you do?